No less than six distinct botnet malware operations are attempting to find TP-Hyperlink Archer AX21 (AX1800) routers susceptible to a command injection safety difficulty reported and addressed final yr.
Tracked as CVE-2023-1389, the flaw is a high-severity unauthenticated command injection downside within the locale API reachable by means of the TP-Hyperlink Archer AX21 internet administration interface.
A number of researchers found it in January 2023 and reported to the seller by means of the Zero-Day Initiative (ZDI). TP-Hyperlink addressed the issue with the discharge of firmware safety updates in March 2023. Proof-of-concept exploit code emerged shortly after the safety advisories turned public.
Following that, cybersecurity groups warned about a number of botnets, together with three Mirai variants (1, 2, 3) and a botnet named “Condi,” that focused unpatched gadgets.
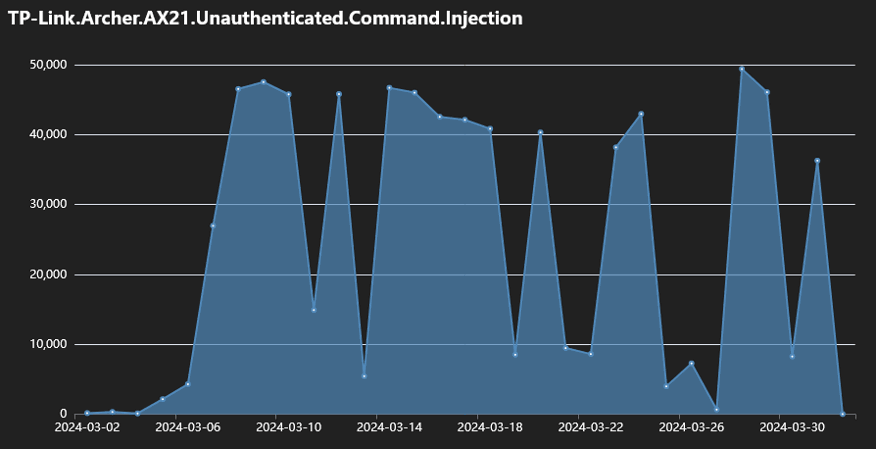
Yesterday, Fortinet issued one other warning saying that it noticed a surge within the malicious exercise exploiting the vulnerability, noting that it originated from six botnet operations.
Fortinet’s telemetry knowledge exhibits that beginning in March 2024, each day an infection makes an attempt leveraging CVE-2023-1389 usually went past 40,000 and as much as 50,000.
(Fortinet)
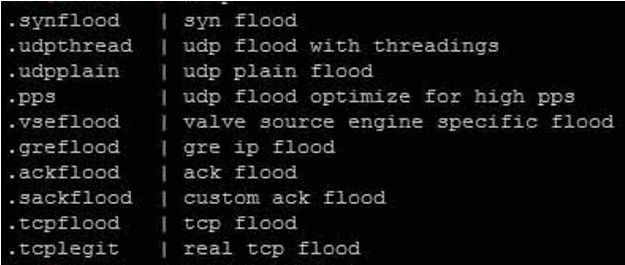
Every of those botnets makes use of totally different strategies and scripts to take advantage of the vulnerability, set up management over the compromised gadgets, and command them to participate in malicious actions comparable to distributed denial of service (DDoS) assaults.
- AGoent: Downloads and executes scripts that fetch and run ELF recordsdata from a distant server, then erases the recordsdata to cover traces.
- Gafgyt variant: Makes a speciality of DDoS assaults by downloading scripts to execute Linux binaries and sustaining persistent connections to C&C servers.
- Moobot: Recognized for initiating DDoS assaults, it fetches and executes a script to obtain ELF recordsdata, executes them primarily based on structure, after which removes traces.
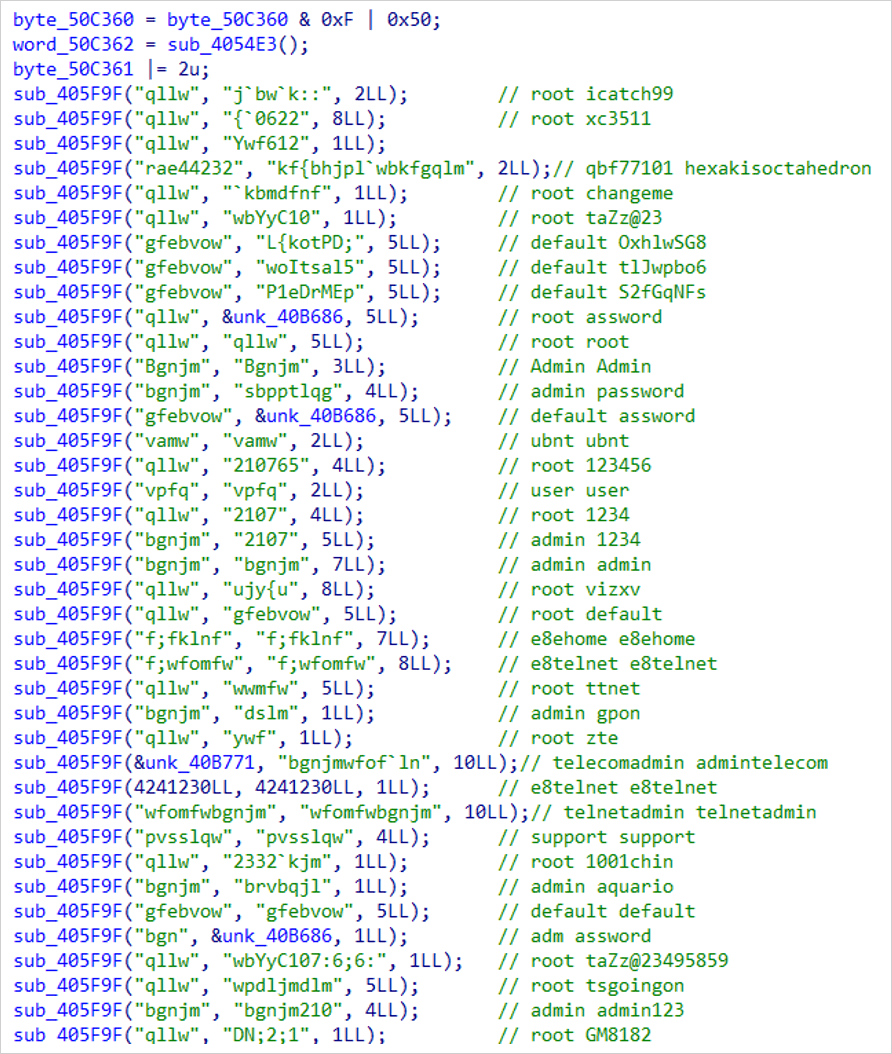
- Miori: Makes use of HTTP and TFTP to obtain ELF recordsdata, executes them, and makes use of hardcoded credentials for brute drive assaults.
(Fortinet)
- Mirai variant: Downloads a script that subsequently fetches ELF recordsdata, that are compressed utilizing UPX. Screens and terminates packet evaluation instruments to keep away from detection.
- Condi: Makes use of a downloader script to reinforce an infection charges, prevents system reboots to keep up persistence, and scans for and terminates particular processes to keep away from detection.
(Fortinet)
Fortinet’s report signifies that regardless of the seller’s launch of a safety replace final yr, a big variety of customers proceed to make use of outdated firmware.
TP-Hyperlink Archer AX21 (AX1800) router customers are suggested to comply with the seller’s firmware upgrading directions, accessible right here. They need to additionally change the default admin passwords to one thing distinctive and lengthy, and disable internet entry to the admin panel if not wanted.