Governance, safety and compliance grow to be tough initiatives at scale. In the event you’re an enterprise working out of Google Cloud, you’re possible on the lookout for methods to handle entry, implement guardrails, and make configuration constraints to sources throughout your group. Under, we are going to introduce all it’s essential to learn about GCP Group Insurance policies and describe how one can leverage them to centralize management over your atmosphere.
Are you multi-cloud? Find out about Azure Coverage right here and AWS Service Management Insurance policies right here.
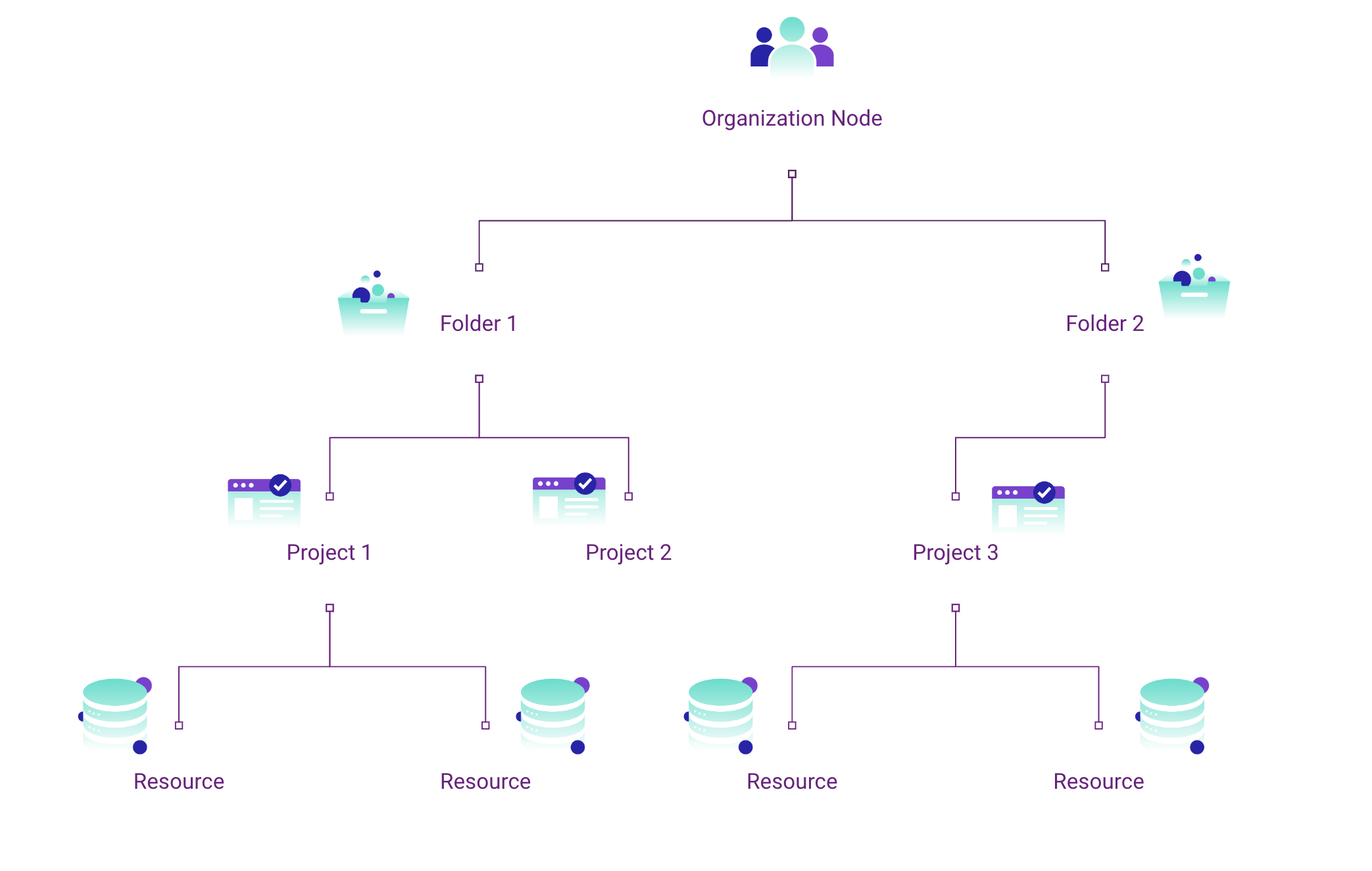
What’s a GCP Group Coverage?
Group Coverage is a strong device supplied by Google Cloud, designed to present you centralized and systematic management over your cloud sources. This coverage isn’t just a function; it’s a cornerstone for managing and securing your cloud atmosphere successfully. So, what precisely is it?
A GCP Group Coverage is a algorithm and constraints that govern how sources in your Google Cloud atmosphere can be utilized. It’s the spine of useful resource administration, guaranteeing that your group’s cloud utilization stays inside safety, compliance and governance boundaries.
GCP Group Insurance policies centralize management. It’s like having a command heart for all of your cloud sources, the place you may arrange guardrails in your growth groups, guaranteeing they function inside safe boundaries whereas nonetheless working effectively.
GCP hierarchy construction. Be taught extra about hierarchy analysis right here.
Key Ideas of GCP Group Coverage
Now, let’s break down the important thing parts of a GCP Group Coverage:
- The Coverage: At its core, an Group Coverage is a group of guidelines utilized to your group’s sources. It’s like a rulebook that dictates what can and can’t be finished inside your cloud atmosphere. There are built-in (Google owned) insurance policies or customized insurance policies.
- Guidelines: These are the particular directives throughout the coverage that decide how and when a constraint is utilized. Consider them as particular person directions or clauses in your rulebook. For example, a rule may implement a constraint solely on sources tagged with atmosphere=growth.
- Constraints: These are the precise restrictions utilized by the coverage. Constraints in GCP coverage are just like the legal guidelines in your rulebook. They outline the boundaries for the conduct of your cloud providers. For instance, “Disable Source Code Download” for AppEngine, or “Restrict which KMS Cryptokey types may be created” for Cloud KMS.
- Inheritance: While you set a coverage on the group stage, it cascades down and applies to all of the sources beneath it – like folders and initiatives. This inheritance ensures that insurance policies are uniformly utilized throughout your group, offering a constant administration method and fewer guide work.
Examples of GCP Org Coverage
useful resource “google_org_policy_policy” “resource_locations” {
identify = “organizations/123456789/policies/gcp.resourceLocations”
spec {
guidelines {
situation {
expression = “resource.location == ‘europe-west4′”
}
deny_all = “FALSE”
}
}
}
The above constraint coverage limits the geo location of recent useful resource deployments to Europe-West4.
identify: organizations/ORGANIZATION_ID/insurance policies/gcp.disableCloudLogging
spec:
guidelines:
-condition:
expression:useful resource.matchTag(”ORGANIZATION_ID/atmosphere”,”growth”)
title:””
implement:true
– implement: false
The above constraint disables Cloud Logging for sources which can be tagged with atmosphere=growth, however permits it all over the place else.
GCP Group Coverage Finest Practices
Some beneficial GCP Group Coverage greatest practices to implement which can be comparatively low hanging fruit embrace:
- Prohibit public IP entry on cloud SQL situations: Self-explanatory, you need to maintain your workloads inaccessible to the general public.
- Implement uniform bucket-level entry: Guarantee all objects have the identical permission and entry greatest practices utilized.
- Prohibit Area Sharing: Prohibit which domains (suppose: a random gmail person) could be added to an IAM coverage and get permissions in your sources.
- Disable automated IAM grants for default service accounts: Default service accounts with default (learn: broad) permissions are good for testing issues however dangerous for dealing with prod workloads.
- Disable service account key creation: By default, service account keys don’t expire till far, far sooner or later. This implies they primarily don’t expire. Implementing this coverage helps forestall key misuse and encourage key rotation coverage within the org and restrict new creations.
A normal phrase of warning when creating organization-level insurance policies: take a look at them out in a separate folder or mission earlier than activating throughout the org. This helps keep away from ‘breaking’ something essential or delicate if a coverage deployment goes unsuitable.
Utilizing Group Coverage for IAM
Now, there’s a distinction between IAM coverage and organizational coverage. Google Cloud gives IAM insurance policies to outline who can take what actions on which sources. The Principal defines the ‘who.’ Subsequent, is the ‘what actions’, which is outlined by roles and their related permissions. Lastly, ‘which resource’ is outlined by the place your coverage is utilized to – the place in your cloud can the principal execute their privilege.
Nevertheless, you should use IAM insurance policies on the organizational scope to operate like a gcp org coverage.
Some factors to notice: 1) GCP is deny by default, that means if there is no such thing as a deny or permit coverage hooked up to an identification, the identification is not going to maintain entry by default. 2) A deny coverage will override any permit permission.
Instance Use Case for GCP IAM Group Coverage
Leveraging the organizational scope when making use of IAM insurance policies is a strong device due to its cascading impact. IAM insurance policies are inherited down from a father or mother useful resource. Let’s say you need your CFO to have ‘read’ entry throughout your total enterprise to allow them to audit how your enterprise is spending cash. You may set a coverage on the org stage providing them the ‘Billing Account Costs Manager’ predefined position so every BU inherits this entry.
Managing Coverage Inheritance
As we’ve launched, org insurance policies work hierarchically, that means the principles set there or at a father or mother useful resource trickle downstream to folders and initiatives and subsequent sources and identities. This lends identities to accumulate privilege not explicitly outlined to them. Now mix these org insurance policies with insurance policies set at useful resource or identification scopes and you’ve got quite a few competing permissions and constraints.
Permissions can grow to be muddled in a short time within the cloud, making perception into what any given identification’s efficient permissions are, tough. In the event you’re a multi cloud enterprise, this permission and entry administration will get much more tough.
Handle Coverage, Safe Entry with Sonrai Safety
Sonrai Safety’s patented permission analytics are constructed to ingest all types of coverage – IAM or useful resource primarily based, organizational, folder or mission particular – and compute how they work together. This perception is unmatched when paired with Sonrai’s nightly assault path evaluation.
Sonrai’s Cloud Infrastructure Entitlement Administration resolution computes efficient permissions, alerts to any related potential dangers like lateral motion and privilege escalation, and gives respective remediation.
Be taught extra in regards to the resolution or watch an on demand demo to see it in motion.

FAQs
GCP Group Insurance policies work alongside instruments like Cloud IAM and Useful resource Supervisor to supply a layered safety method, with IAM specializing in who has entry and Group Insurance policies dictating how sources can be utilized.
For extra granular management, GCP Group Insurance policies could be utilized particularly to sure providers or sources by leveraging constraints at totally different ranges of the useful resource hierarchy, reminiscent of initiatives, folders, or the complete group. This focused method permits directors to fine-tune their insurance policies to swimsuit the wants of various components of their group, guaranteeing flexibility and specificity in entry management and useful resource utilization.
Managing GCP Group Insurance policies at scale entails navigating challenges like sustaining consistency throughout numerous insurance policies, guaranteeing that insurance policies don’t inadvertently block vital entry or operations, and coping with the complexity of hierarchical inheritance.