Having AST capabilities constructed into the tooling that we use in our day-to-day duties as builders supplies a number of worth once we’re making an attempt to ship dependable and safe merchandise, regardless that it might really feel like an extreme requirement that’s simply there to satisfy company requirements. There are IDE plugins for performing native checks earlier than you decide to Git, and it looks as if there are numerous scanners all through the CI/CD pipeline, from pull requests to manufacturing. Each has a purpose to be there, and every one is important for sustaining a safe utility profile.
These scans do present worthwhile knowledge. For instance, they will discover locations that reference outdated libraries, which might result in defects and after-hours calls from panicked operations of us. Along with decreasing avoidable defects, scans can determine variables and unused dependencies that trigger utility bloat. They will even guarantee that the code is styled in the identical method (so you possibly can lastly choose a successful facet within the tabs vs. areas flame warfare).
So Many Locations, So Little Time
The bigger and older your group is, the extra doubtless it’s that you simply’re utilizing scanning know-how that’s been blended and matched. There are a couple of causes for this. For one, the group’s suite of instruments was doubtless assembled over time, which most likely concerned discovering options to new necessities in a vacuum. The chosen instrument may need been best-of-breed or absolutely the most cost-effective obtainable, relying on who was working the procurement cycle on the time. As well as, the group would possibly lack a centralized strategy, both as a result of they only allowed completely different improvement teams to do their very own factor, or as a result of they skilled many alternative mergers and left acquisitions semi-autonomous.
In an atmosphere the place there are a number of instruments from a number of distributors, every with its personal technique of retrieving knowledge, it may be a frightening job for a developer simply to recollect all the scans that she or he must carry out, to not point out maintain monitor of the place to get the outcomes of every one. In conditions like this, aggregation could be a enormous assist.
There are a number of completely different ranges of aggregation, and attaining any one in every of them is a step in the appropriate course. For instance, you possibly can combination the method of kicking off your whole scans utilizing hooks in your favourite model management software program at a sure gateway step (like a merge request). This strategy permits builders to seek out all the outcomes for any scans that the group requires. You may even have them block requests till any points are resolved.
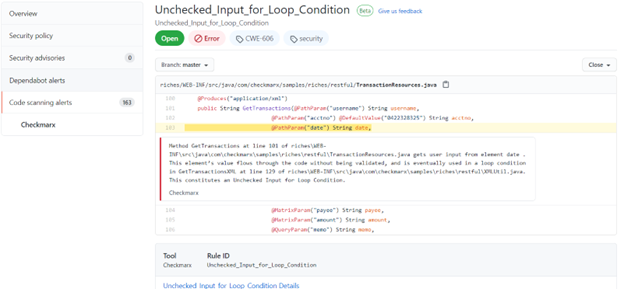
For instance, you would possibly see one thing like this when you’ve built-in scans into GitHub pull requests:
(supply: https://github.com)
One other instance of aggregation is a dashboard that mixes all the outcomes right into a single, easy-to-access view. This strategy doesn’t appear to be as frequent, since among the instruments concerned might not have an API or a simple level of integration. Some organizations, nonetheless, have the luxurious of standardizing their safety testing with a single vendor that gives end-to-end integrations and a handy console. This normally comes about when the group lastly will get critical about its funding in safety.
One View to Rule Them All
Single-vendor consoles come closest to what a developer would possibly contemplate the height of ease-of-use, which might be the correlation of all outcomes from all scans towards any utility code base in context.
Bits and items of this perfect do exist – like the power to point out an inventory of dependencies which can be outdated, or the power to point out static code leads to an IDE by highlighting strains that aren’t as much as the required requirements. However it isn’t all proven in context, and it’s lacking different issues – just like the outcomes of IAST scans that may pinpoint a dependency or line of code that’s inflicting an error.
As soon as these bits and items have been introduced collectively in a single console, distributors might take it even additional by integrating runtime knowledge generated by CWPP, CASM, CWPS, or CNAPP tooling (which watches the reside atmosphere and continuously appears for tactics to enhance and areas that want consideration.) Distributors might additionally lengthen past safety knowledge to incorporate APM suites that builders use to collect utilization knowledge that permits them to fine-tune and improve their purposes.
Conclusion
Aggregating the outcomes of all the varied safety scans that an utility undergoes from keyboard to manufacturing in a single place is a superb first step. It might be even higher when you had a couple of entry factors to get to the outcomes. However having a centralized view the place you might see all the related points whereas viewing the code could be finest. Distributors are getting there, and builders are simply ready for them to take that subsequent step so that each one of that consolidated knowledge might be introduced into their protected place: the code. As an alternative of merely attaining an operations-friendly atmosphere, this final step would create a utopia for builders.
In the event you’re seeking to leverage a single vendor for your whole AppSec wants, contemplate the Checkmarx One™ Software Safety Platform. Checkmarx One is constructed from our industry-leading AppSec options—SAST, SCA, IaC, API Safety, Container Safety, and Provide Chain Safety (SCS)—and delivered from the cloud. It supplies fast, correlated, and correct outcomes to hurry remediation all on a single, unified report.
Bio

Vince Energy is an Enterprise Architect with a deal with digital transformation constructed with cloud enabled applied sciences. HE has intensive expertise working with Agile improvement organizations delivering their purposes and providers utilizing DevOps ideas together with safety controls, identification administration, and check automation. You will discover @vincepower on Twitter.