DrayTek has launched safety updates for a number of router fashions to handle 14 vulnerabilities of various severity, together with a distant code execution flaw that obtained the utmost CVSS rating of 10.
The issues, which Forescout Analysis – Vedere Labs found, influence each actively supported and fashions which have reached end-of-life. Nevertheless, as a result of severity, DrayTek has offered fixes for routers in each classes.
The researchers warned that their scans revealed that roughly 785,000 DrayTek routers is perhaps susceptible to the newly found set of flaws, with over 704,500 having their internet interface uncovered to the web.
Vulnerability particulars
Most vulnerabilities found by Vedere Labs are medium-severity buffer overflow and cross-site scripting issues dictated by a number of exploitation necessities.
Nevertheless, 5 of the issues carry vital dangers, requiring instant consideration. These are summarized as follows:
- FSCT-2024-0006: A buffer overflow vulnerability within the “GetCGI()” operate, accountable for dealing with HTTP request information, which may result in denial of service (DoS) or distant code execution (RCE). (CVSS rating: 10.0)
- FSCT-2024-0007: Command Injection in OS Communication – The “recvCmd” binary used for communication between the host and visitor working programs is susceptible to command injection assaults, doubtlessly permitting VM escape. (CVSS rating: 9.1)
- FSCT-2024-0014: The net server backend makes use of a static string to seed the pseudo-random quantity generator (PRNG) in OpenSSL for TLS connections, which might result in data disclosure and man-in-the-middle (MiTM) assaults. (CVSS rating: 7.6)
- FSCT-2024-0001: The usage of an identical admin credentials throughout your complete system can result in full system compromise if these credentials are obtained. (CVSS rating: 7.5)
- FSCT-2024-0002: An HTML web page within the Internet UI improperly handles enter, permitting for mirrored XSS vulnerabilities. (CVSS rating: 7.5)
As of but, there have been no experiences of lively exploitation of those flaws, and the publication of analytical particulars has been withheld to permit customers sufficient time to use the safety updates.
The above flaws influence 24 router fashions, of which 11 have reached the tip of life but nonetheless obtained fixes.
The impacted fashions and goal firmware variations to improve to may be seen within the desk beneath.
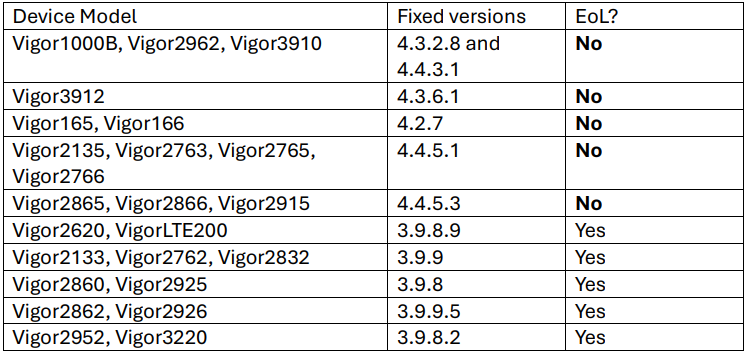
Customers might obtain the most recent firmware for his or her machine mannequin from DrayTek’s official obtain portal.
Over 700,000 DrayTex units uncovered on-line
Verdere Labs experiences that it discovered over 704,500 units have the DrayTek Vigor Internet person interface uncovered to the web, although it ought to solely be accessible from a neighborhood community.
Practically half of the units underneath Forescout’s direct visibility are situated in the USA, however Shodan outcomes present vital numbers in the UK, Vietnam, the Netherlands, and Australia.
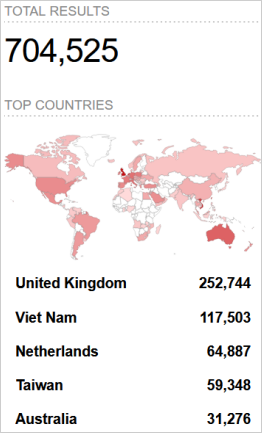
Supply: Verdere Labs
Other than making use of the most recent firmware updates, customers are beneficial to take the next actions:
- Disable distant entry if not wanted, and use an entry management record and two-factor authentication when lively.
- Examine settings for arbitrary alterations or the addition of admin customers or distant entry profiles.
- Disable SSL VPN connections by way of port 443.
- Allow syslog logging to observe for suspicious occasions.
- Allow auto-upgrade to HTTPs pages in your internet browser.
All DrayTek customers ought to verify that their machine’s distant entry console is disabled, as exploits and brute power assaults generally goal these providers.
