Darktrace AI detected and stopped a thread hijacking assault in real-time, stopping electronic mail account compromise and information theft. The assault concerned a hidden electronic mail rule diverting messages from the meant recipient.
Cybersecurity specialists have noticed an increase in thread hijacking assaults, which criminals use to infiltrate electronic mail conversations and steal delicate information. This system is especially stealthy as a consequence of its near-invisibility to traditional safety measures and human detection.
In thread hijacking attackers acquire entry to a person’s electronic mail account, monitor conversations, and infiltrate conversations between people or organizations, exploiting belief inside these threads.
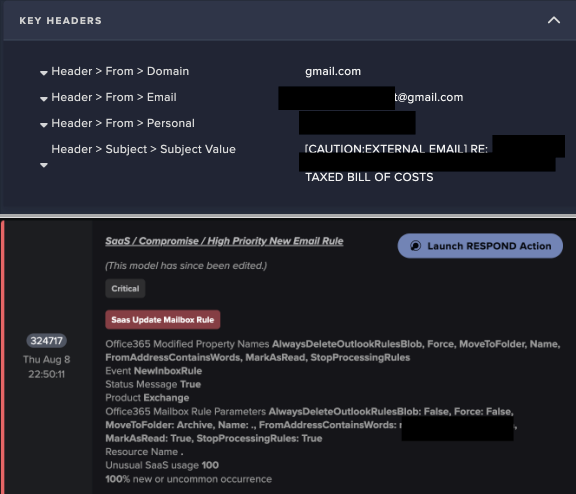
In a latest incident, Darktrace’s AI expertise detected and halted a thread hijacking assault in real-time, concentrating on a serious firm. The assault vector on this case is an electronic mail despatched to a SaaS (Software program-as-a-Service) person hours earlier than a brand new electronic mail rule was created, allegedly a reply to a earlier electronic mail concerning tax and fee particulars, which Darktrace AI detected as anomalous. The hidden electronic mail rule was created to divert particular messages away from the meant recipient.
Assault Particulars
In line with Darktrace’s weblog put up shared with Hackread.com forward of publishing on Monday, a person’s electronic mail account was compromised by an attacker probably by way of phishing, malware, or exploiting weak passwords. They monitored the person’s electronic mail threads in search of exploitable ongoing conversations after which inserted themselves into conversations by replying to current emails. As a result of the e-mail appeared to come back from a trusted supply inside an ongoing thread, it bypassed many conventional safety filters and raised much less suspicion.
The attacker created a brand new mailbox rule to ahead emails to an archive folder, making it tougher for the client to note the malicious exercise. Utilizing the belief established within the dialog, the attacker tried to control the person into clicking on malicious hyperlinks or offering delicate data.
“This evasion technique is typically used to move any malicious emails or responses to a rarely opened folder, ensuring that the genuine account holder does not see replies to phishing emails or other malicious messages sent by attackers.”
Darktrace
Darktrace’s Response
Darktrace’s Self-Studying AI detected the anomaly on August 8, 2024, which was a suspiciously named “.” mailbox rule. Darktrace’s RESPOND software took fast motion by disabling the compromised SaaS person for twenty-four hours, stopping additional escalation of the assault.
Moreover, a Proactive Menace Notification was despatched to the Darktrace SOC crew, permitting them to research the incident and inform the client. Total, the incident highlights the significance of superior risk detection and response instruments like Darktrace to guard organizations from refined cyberattacks like thread hijacking.
RELATED TOPICS
- How AI is Tightening Cybersecurity for Companies
- LockBit 3.0 Posts Doubtful Claims of Breaching Darktrace
- IT and Cybersecurity Jobs within the Age of Rising AI Applied sciences
- Electronic mail Hacking Reigns as Prime Cybersecurity Menace, Indusface Research
- The Way forward for Phishing Electronic mail Coaching for Workers in Cybersecurity