Attackers born within the cloud
Cloud attackers are swift and complicated, requiring strong menace detection and response packages that may preserve tempo with these malicious actors born within the cloud. They exploit the automation and scale of the cloud, together with new methods, to speed up all levels of an assault and inflict injury inside minutes.
A pertinent instance of cloud assaults executed by these new-age menace actors is SSH-Snake (found by Sysdig TRT). SSH-Snake is a self-modifying worm that leverages SSH credentials found on a compromised system to start out spreading itself all through the community. The worm routinely searches by way of identified credential places and shell historical past information to find out its subsequent transfer. Extra element might be discovered about SSH-Snake in a deep-dive weblog we did post-discovery. We’ve got additionally finished a deep dive into the opposite subtle assaults, similar to SCARLETEEL, previously.
To maintain up with such assaults (and attackers), safety groups require custom-made tooling that friends deep into the crevices of the cloud, identifies danger, and helps reply quick sufficient to comprise threats. Actually, due to these assaults, your entire paradigm of what constitutes an ideal response technique within the cloud must be re-conceived. The 555 Benchmark guides organizations to detect and reply to cloud assaults quicker than adversaries can full them. In brief, defenders have 5 seconds to detect, 5 minutes to analyze, and 5 minutes to answer any cloud assault.
Arming defenders of the cloud with insights and automation
Torq and Sysdig are two corporations “born in the cloud” which might be partnering to assist prospects keep forward of cloud-savvy menace actors. Torq.io is an AI-Pushed hyper automation software program that helps safety groups with automations that speed up investigation and response for the cloud. When leveraged along with Sysdig, the chief in cloud safety powered by runtime insights, prospects can get unmatched visibility into the cloud for detections, and automate their incident response workflows to fulfill the 555 benchmark.
Redefining cloud detection, investigation, and response
Sysdig allows prospects to optimize their cloud detection and response (CDR) use instances with automated assortment and correlation of all their cloud knowledge, together with occasions, posture misconfigurations, and exploitable vulnerabilities to identities. The cloud context Sysdig supplies is unparalleled. An interactive visualization of this context helps analysts immediately conceptualize assaults, unlocking five-minute investigations throughout essentially the most superior threats. Some key capabilities to spotlight embrace:
Integration and workflow automation targeted on cloud safety for the SOC
Sysdig has partnered with Torq with the target of offering important out-of-the-box SOC automation workflows because it pertains to CDR. Our joint prospects can now reply by way of ready-to-use remediation workflow units that assist obtain the 555 benchmark with on the spot actions associated to every of the steps. They’ll edit the out-of-the-box templated playbook and likewise construct extra subtle ones when required. So, the concept is to facilitate (and encourage) purpose-built workflow playbooks that may take particular actions as they relate to real-world cloud threats.
Here’s a 10,000-foot view of how knowledge flows inside this integration:
- Preliminary safety occasions are gathered from the Sysdig HTTPS notification channel and despatched to Torq.
- These are triaged in seconds (in actual time) by an motion set within the Torq workflow that leverages Sysdig APIs. This ensures that the time to analyze and begin case enrichment with contextual knowledge is diminished to seconds with almost on the spot detection and automation.
- Torq makes use of the specialised context offered by Sysdig (i.e., Kubernetes namespace in case of occasions associated to containerized workloads) to seek out the perfect staff and assignee in a undertaking/case administration software program, like JIRA or ServiceNow.
- These case tickets are created, triaged, enriched, and assigned to the suitable staff and person seconds after the menace has been captured.
- Groups can add auto response steps inside Torq to additional sharpen the investigation, mitigation, and response methods.
Listed below are the varied actions that may be taken leveraging this integration:
- Question stock of cloud belongings and cloud-native workloads for danger components associated to the deployment topology.
- Get picture vulnerabilities and runtime insights for container and host photographs.
- Get customers associated to Kubernetes occasions.
- Retrieve occasions by ID.
- Retrieve your entire related occasions historical past detected by Sysdig.
Automated cloud investigations and case element enrichment for the SOC
It’s typical for cloud safety instruments to assemble huge quantities of information and safety findings. Typically, this can be a reside telemetry of occasions similar to file dumps or captures from containers, cloud providers, and identities throughout a number of cloud service suppliers. Gathering this knowledge in a consumable format is the vital job that’s anticipated from the SOC analysts, Incident responders, and safety menace researchers.
Right here is the place the utility of a hyper-automation instrument like Torq actually comes into play. Take, for instance, the under screenshot the place Sysdig has captured (immediately) the truth that a terminal shell was opened up by an attacker whereas executing a cloud assault, similar to SCARLETEEL or SSH-Snake. Sysdig alerted Torq.
When you test these instances getting created in Torq’s personal case administration system:
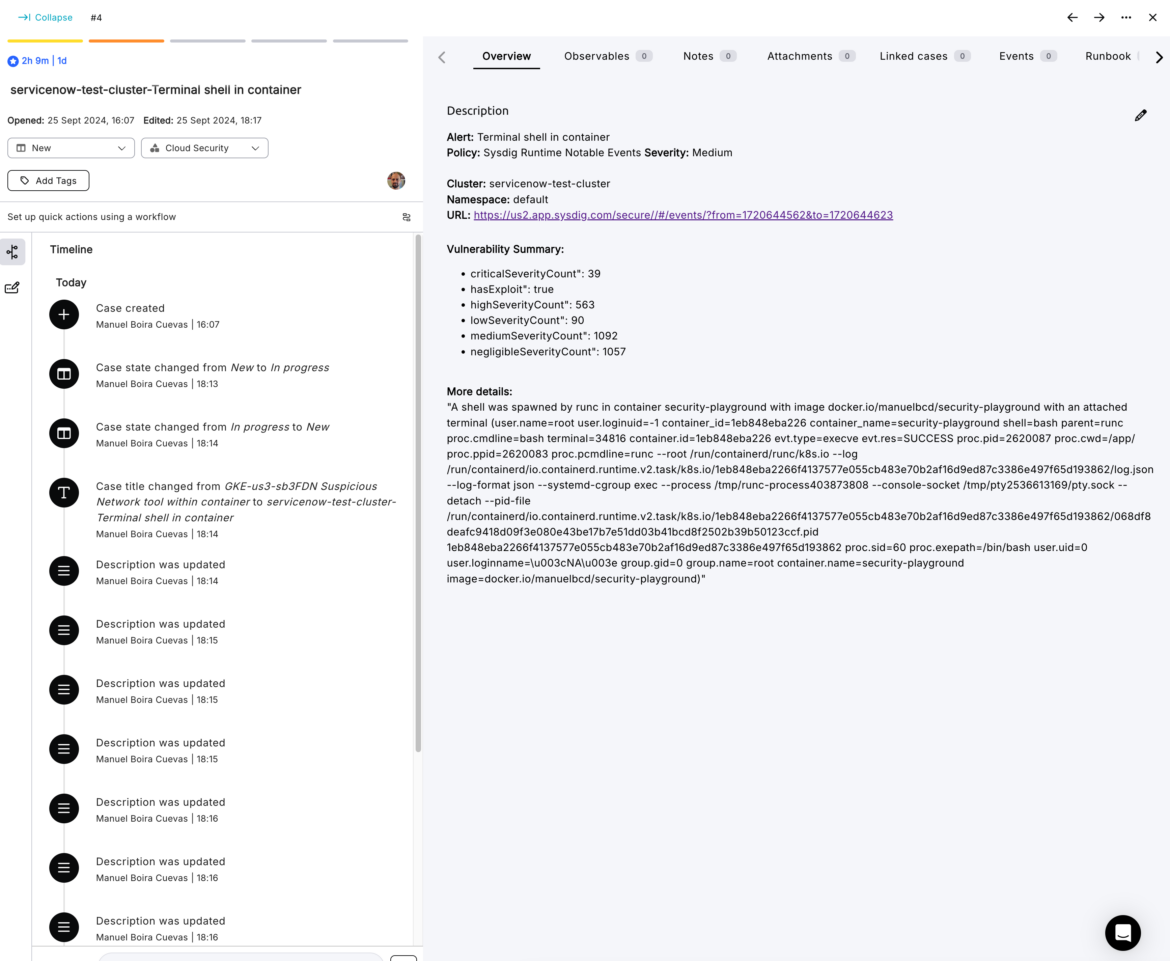
Torq was capable of fetch all the small print from this Sysdig alert and create a well-formulated JIRA/Torq case ticket for the Incident Response or the Forensics staff:
Discover the granularity and depth of the occasion metadata captured by Sysdig. Typical cloud safety instruments fail to understand the small print related to Kubernetes or containerized workflows. Nonetheless, Sysdig is ready to seize each the cloud and workload particulars in order that safety menace researchers can correlate them — both throughout incident response or forensics. This workflow is not only capturing particulars from an alert, but additionally enriching the occasion particulars based mostly on the kind of the occasion (Kubernetes or container occasion).
Torq improves its response workflows based mostly on the context offered by Sysdig, together with container particulars, vulnerability abstract, and different related particulars related to the detected occasion. Observe how Torq is ready to devour Sysdig occasion logs within the screenshot under:
Inside this workflow playbook, Torq also can question Sysdig APIs to take completely different actions like within the screenshot under:
Lastly, the under workflow playbook is absolutely customizable, so a buyer can change and modify the completely different steps when required.
To summarize the info circulate:
Preliminary safety occasions are gathered from the Sysdig HTTPS notification channel, after which instantly triaged in actual time by an motion set within the Torq workflow that leverages Sysdig APIs. This ensures that the time to analyze and begin case enrichment with contextual knowledge is diminished to seconds with almost on the spot detection and automation.
- Sysdig identifies malicious exercise and notifies it to Torq in actual time.
- Torq workflow queries a Sysdig API (Sysdig stock API) to extract extra context concerning the container picture, configuration, and its vulnerabilities.
- Torq makes use of the specialised context offered by Sysdig (i.e., Kubernetes namespace) to seek out the perfect staff and assignee in Jira by querying Atlassian APIs.
- A Jira ticket is created, triaged, and assigned to the suitable staff and person seconds after the menace has been captured.
Additional: Groups might wish to add auto response mechanisms, like narrowing down the cluster safety group as a mitigation technique, whereas the staff begins the investigation.
Now, think about that this was an actual assault, like an SSH-Snake, and the incident responders had been utilizing conventional EDR instruments. They’d have had no community telemetry and the shortage of forensic element would make the response extraordinarily gradual and laborious — particularly because it pertains to monitoring the exercise inside the compromised workloads.
Leveraging easy-to-implement workflows like this one, Sysdig and TORQ customers will not be solely capable of detect advanced assaults like SSH-Snake, but additionally routinely cease threats in only some seconds! Different response actions like step-up monitoring of suspicious processes or terminating compromised containers are additionally attainable relying on the danger urge for food of the group.
Integration setup
Search for the Sysdig integration inside the Torq hyper-automation UI:
As soon as discovered, you’ll be able to implement your individual workflow utilizing the predefined Sysdig steps, or choose the under workflow playbook from the catalog:
Conclusion
It’s essential for corporations to implement an investigation and response technique that takes lower than 10 minutes to be able to safeguard their cloud environments from malicious menace actors. Cloud safety from Sysdig might be turbocharged with the facility of undertaking administration instruments like Jira, CRMs like Salesforce, messaging apps like Slack, and way more by leveraging Torq workflows. Sysdig and Torq have come collectively to assist our prospects detect, triage, and reply to essentially the most subtle cloud assault methods. We assist prospects unlock the facility of superior SOAR workflows – enabling on the spot detection, automated investigation, knowledge enrichment, correlation, and response.