DragonForce ransomware is increasing its RaaS operation and changing into a world cybersecurity risk in opposition to companies. Corporations should implement robust cybersecurity methods to defend in opposition to this rising ransomware assault and keep away from changing into victims.
Ransomware assaults are rising, leaving organizations susceptible to new and extra refined threats. In line with Group-IB’s Hello-Tech Crime Developments 2023/2024 report, ransomware incidents might trigger even better injury in 2024.
One of the crucial vital rising threats is the DragonForce ransomware group, which leverages a Ransomware-as-a-Service (RaaS) associates program, using variants of well-known ransomware households to wreak havoc on focused industries.
DragonForce: A Twin-Ransomware Menace
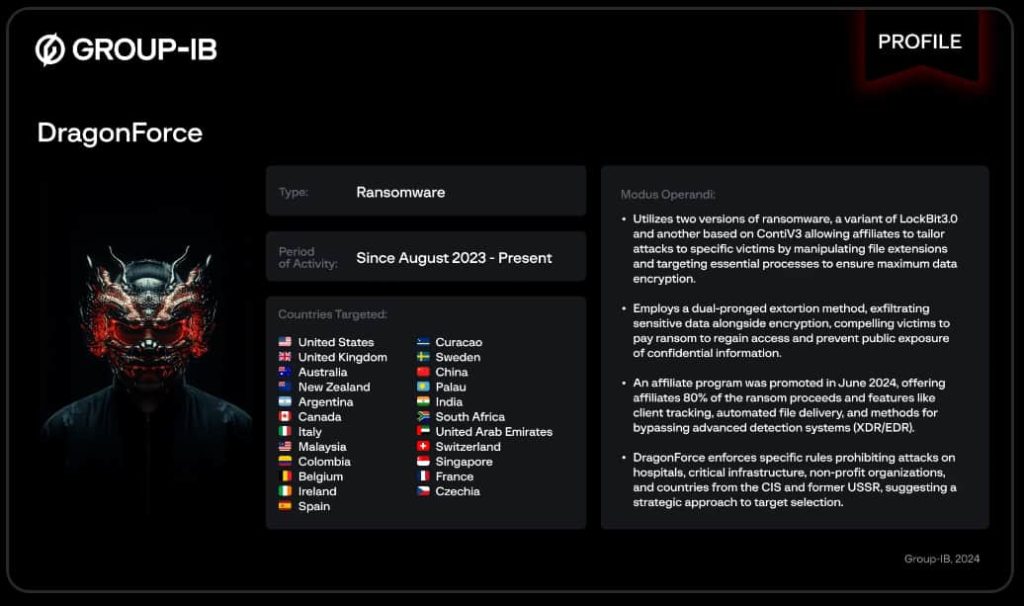
The DragonForce ransomware group emerged in August 2023, deploying a variant based mostly on LockBit 3.0, a infamous ransomware pressure. Nevertheless, by July 2024, the group launched a second variant, initially claimed to be their unique creation however later discovered to be a fork of ContiV3 ransomware. These twin ransomware variations are used to use vulnerabilities in corporations, significantly in sectors like manufacturing, actual property, and transportation.
DragonForce’s assault technique revolves round double extortion—encrypting knowledge and threatening to leak it except a ransom is paid. This provides immense stress on victims to conform, fearing not solely operational disruption but in addition the reputational injury that would come up from uncovered delicate info.
Superior Ways for Most Injury
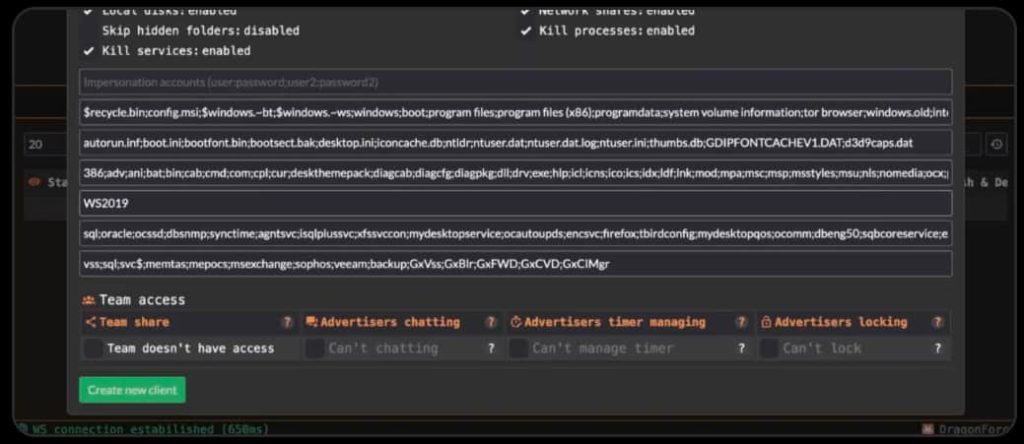
In line with Group-IB’s analysis shared with Hackread.com forward of publication on Wednesday, the DragonForce ransomware gang’s operations are extremely customizable, permitting associates to configure assaults based mostly on the kind of sufferer.
With its RaaS associates program, launched on June 26, 2024, DragonForce ransomware presents attackers the flexibility to personalize ransomware payloads. Associates can disable security measures, set encryption parameters, and even customise ransom notes. In return, associates obtain 80% of any ransom collected.
DragonForce employs quite a lot of superior strategies for evasion and persistence. Certainly one of their key ways is “Bring Your Own Vulnerable Driver” (BYOVD), the place associates use susceptible drivers to disable safety processes and evade detection. Moreover, they clear Home windows Occasion Logs after encryption to hinder forensic investigations.
For lateral motion, the group makes use of instruments like Cobalt Strike and SystemBC, each of which permit them to reap credentials and persist in networks. In addition they use community scanning instruments like SoftPerfect Community Scanner to map out networks, serving to unfold the ransomware to as many units as doable.
Focused Assaults and World Attain
Between August 2023 and August 2024, DragonForce listed 82 victims on its darkish internet leak website. Most assaults had been concentrated within the U.S. (52.4%), adopted by the U.Ok. and Australia. The manufacturing sector suffered the best variety of assaults, with actual property and transportation industries shut behind.
Along with their use of ContiV3 and LockBit variants, DragonForce’s potential to adapt to new affiliate calls for makes them a quickly rising risk. By focusing on high-revenue corporations and important sectors, they proceed to extend their foothold within the cybercrime infrastructure.
What Can Companies Do?
To fight these refined assaults, companies must undertake extra proactive and layered safety measures. Listed here are some crucial steps:
- Multi-Issue Authentication (MFA): Including extra authentication layers makes it more durable for attackers to compromise credentials.
- Early Detection: Use behavioural detection instruments corresponding to Endpoint Detection and Response (EDR) to determine suspicious exercise early.
- Backup Technique: Common backups scale back the influence of ransomware by guaranteeing knowledge might be recovered with out paying ransom.
- Patch Vulnerabilities: Usually patching identified vulnerabilities prevents ransomware from exploiting outdated techniques.
- Worker Coaching: Coaching staff to acknowledge phishing and different malicious ways can forestall preliminary infiltration.
- Keep away from Paying the Ransom: Paying ransom usually results in extra assaults, because it alerts vulnerability to different cybercriminals.
Whereas DragonForce ransomware expands its RaaS operation, companies should stay alert and implement correct cybersecurity methods to keep away from changing into victims of this and different harmful threats.