Disruptive applied sciences have a studying curve within the tempo of adoption and implementation. Coaching and schooling are likely to observe a slower schedule and may have a tough time maintaining with discoveries occurring on the bleeding edge. That is a part of what led to the present cloud safety talent hole.
The cloud reworked software program growth, accelerating innovation and the tempo of human creativity. However, we now know that it additionally fashioned new safety challenges. The cloud is complicated and gives malicious actors with many alternatives. Nevertheless, one out of each 4 IT and safety specialists battle to get the coaching essential to defend correctly.
Safety professionals want to maneuver quick to remain on prime of evolving threats. With cloud adoption nonetheless ongoing, smaller groups can battle to maintain monitor of what’s occurring of their environments. Not everybody has a completely stocked SOC in home!
That is why Sysdig Sage™, our AI-driven cloud safety analyst, was constructed to assist safety professionals of all ranges speed up evaluation and investigation, permitting them to prioritize what issues. However, is it really beginner-friendly?
On this article, we discover Sysdig Sage from a non-technical perspective. Most cybersecurity professionals can have higher coaching than two entrepreneurs on a product walkthrough, however can it assist two relative newbies navigate a fancy cloud safety setting?
250 occasions in a single occasion – the very first thing one notices when a safety occasions log is the sheer quantity of information. We hear quite a bit about alert fatigue working within the cloud safety business, however nothing can put together you for that lengthy doom scroll. All the pieces on the display screen paperwork issues occurring in your setting, which is extremely useful, however not understanding what’s innocuous and what’s a menace – and the way a lot of a menace – makes a giant distinction.
The thought that instantly involves thoughts is “Where do I even start”?— KZ
What’s Sysdig Sage?
Sysdig Sage makes use of an autonomous brokers method, leveraging a number of specialised AI brokers that work collaboratively with a typical aim: to simplify and speed up safety and allow a quicker, better-informed human response.
With the assistance of multi-step reasoning and contextual consciousness, Sysdig Sage understands precisely the place the person is within the UI and gives direct, easy-to-understand explanations of all runtime occasions. It additionally suggests remediation methods and prevention greatest practices and enhancements.
This makes it splendid for safety groups with numerous talent ranges – everybody on the staff can get the assistance they should handle extra and escalate much less.
Dive deeper into Sysdig Sage right here.
As quickly as I leap right into a safety platform, it’s data overload. There’s clearly tons of worthwhile information right here, all telling a narrative about what’s occurring in my setting, however not in any language I communicate. Which data truly issues? Which occasions signify actual threats I must deal with? Even once I deliver up a particular occasion, it’s not clear what I ought to truly be doing. If I’m going to make any sense of all of the wealthy data at my fingertips, I’m positively going to want some assist.
— MR
A newbie’s information to Sysdig Sage
The place do I begin – prioritization and technique
At a look, it turns into clear that Sysdig Sage is instrumental for anybody seeking to achieve a extra in-depth understanding of the phrases and ideas of cloud safety. This is without doubt one of the advantages of multi-step reasoning. Sysdig Sage understands the query, gives easy solutions, and – like several good conversationalist – remembers what we talked about earlier and lets it inform future queries.
As an entire newbie, I would want some really foundational components defined. Being new to runtime safety, my understanding of what precisely constitutes a runtime occasion could be slightly hazy.
So, I requested Sysdig Sage to clarify.
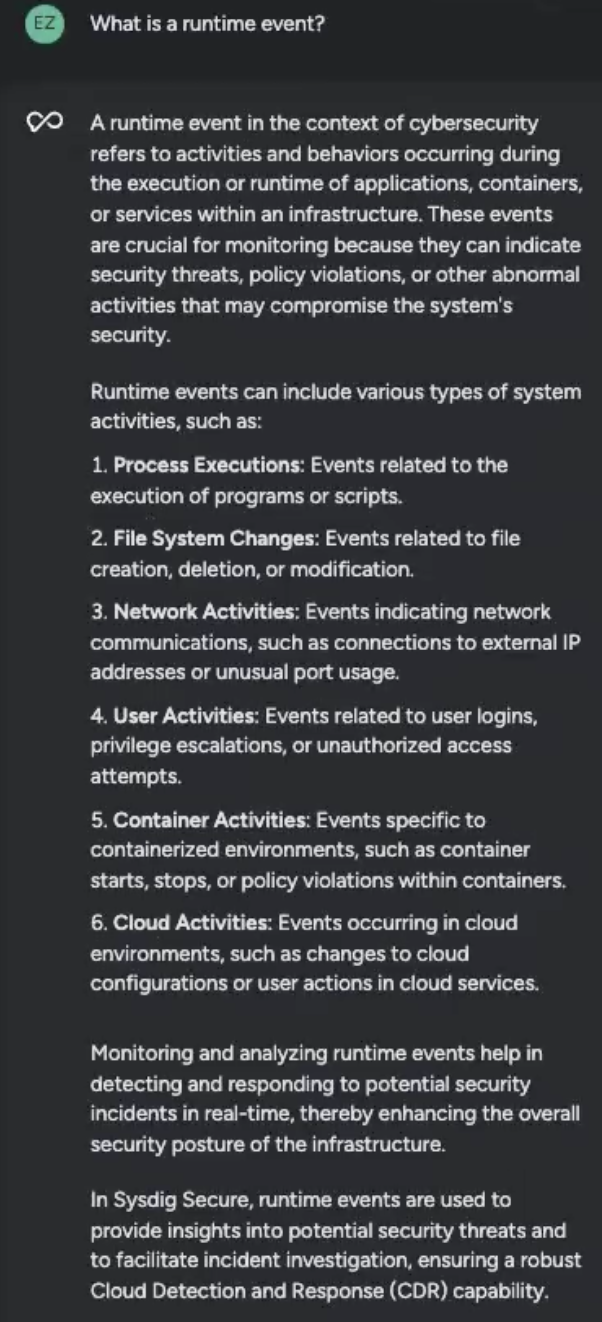
What’s nice concerning the response is that it does what it’s imagined to: outline the time period I requested about in addition to craftily counsel recommendations on the areas I must pay common consideration to. It’s already serving to me prioritize, even at this early stage.
As a result of it’s context-aware, Sysdig Sage is aware of the place I’m inside the UI and works as my associate as I attempt to perceive the runtime occasions in entrance of me. Clicking into any occasion reveals the Sysdig Safe detailed overview:
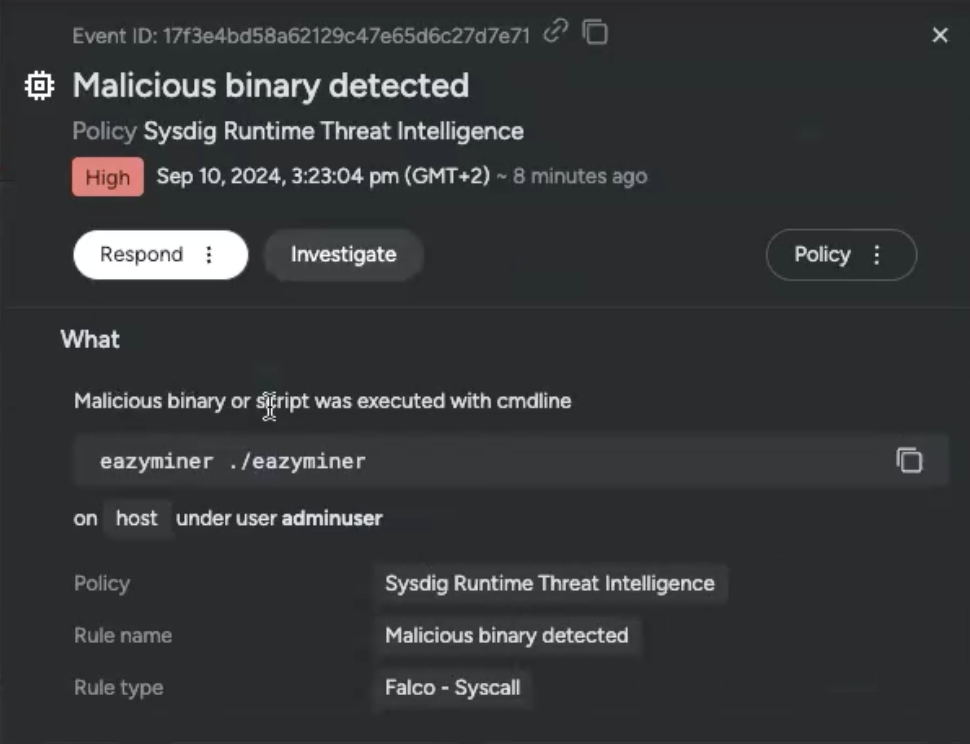
This overview is helpful for fast response – immediately, I can see the occasion was high-severity and it occurred lately, which suggests I ought to prioritize it. I additionally had the Reply and Examine toggles prepared to make use of. However, as a much less skilled person, I instantly had many questions:
- How huge of a menace is that this?
- That eazyminer line doesn’t encourage confidence. How can I perceive it higher?
- Ought to I droop the id entry that adminuser person is clearly exploiting?
- Is that this all part of a broader safety incident?
Earlier than I might panic additional, I requested Sysdig Sage for particulars:
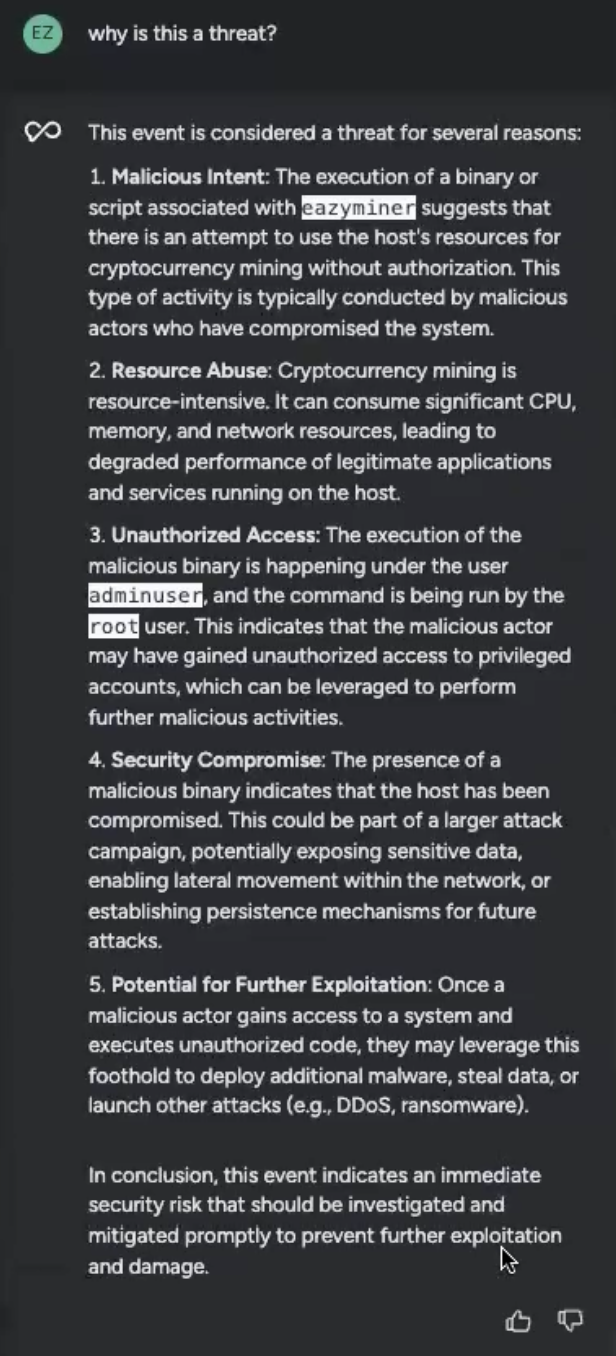
In keeping with Sysdig Sage, this was positively a cryptoming occasion. My setting’s sources had been being abused, and whoever it was had admin entry and was operating the command as root person. It was additionally prone to be part of a wider safety occasion. I knew immediately I wanted to behave. Utilizing Sysdig Sage’s remediation choices, I proceeded with subsequent steps.
After taking part in round with the instrument for a couple of minutes, it was clear that Sysdig Sage might assist me perceive runtime occasions. However, that was just one occasion.
My Occasions log confirmed I had a variety of occasions.
Lots of them latest, a lot of them excessive severity.
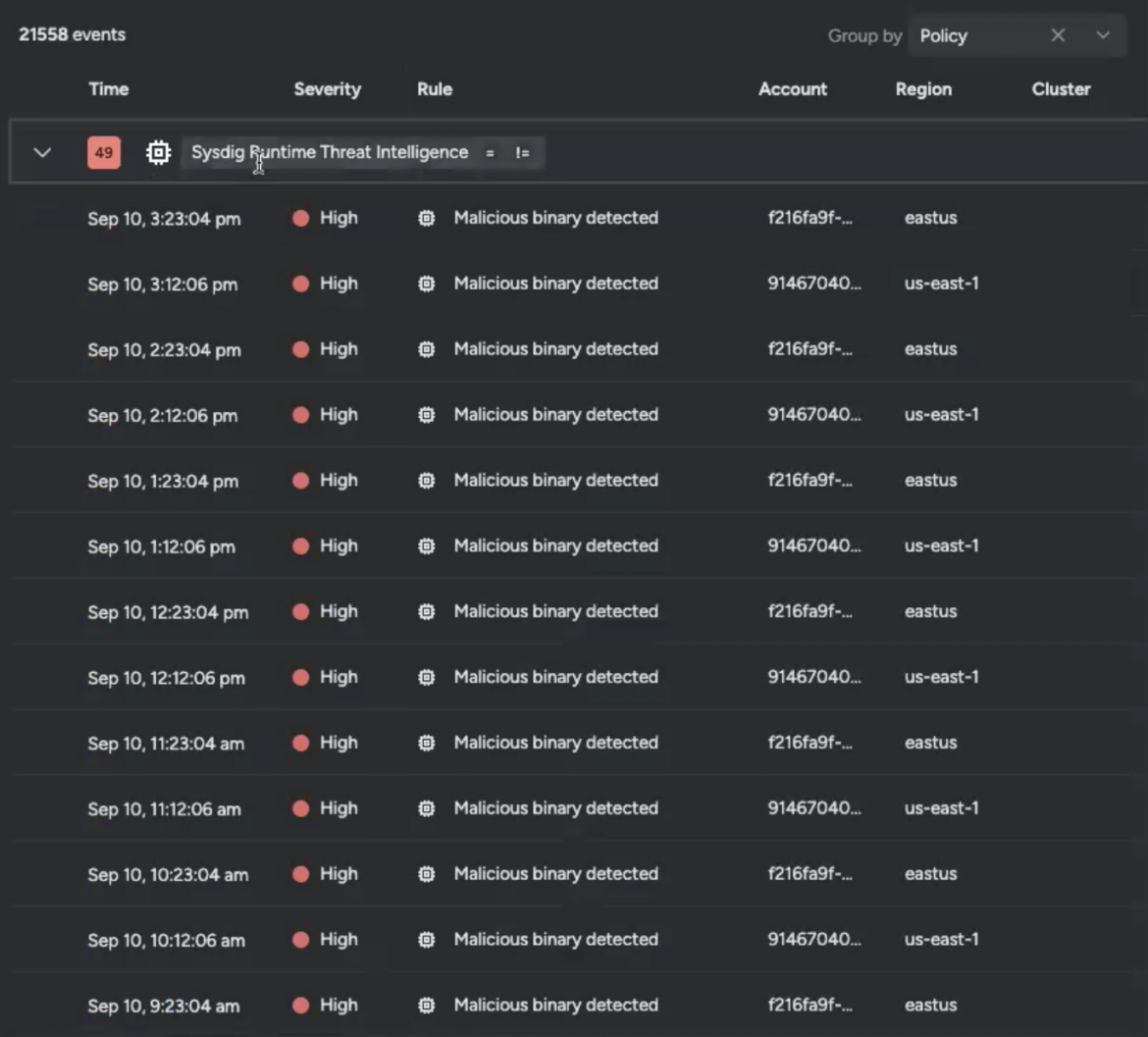
Trying to deal with all of them can be not possible. I would miss one thing vital if I attempted going by way of all of them directly.A extra skilled safety skilled might need been capable of inform what issues at a look and plan her day accordingly, however that wasn’t me. I knew I wanted assist.
So, I requested Sysdig Sage concerning the occasions I wanted to deal with first.
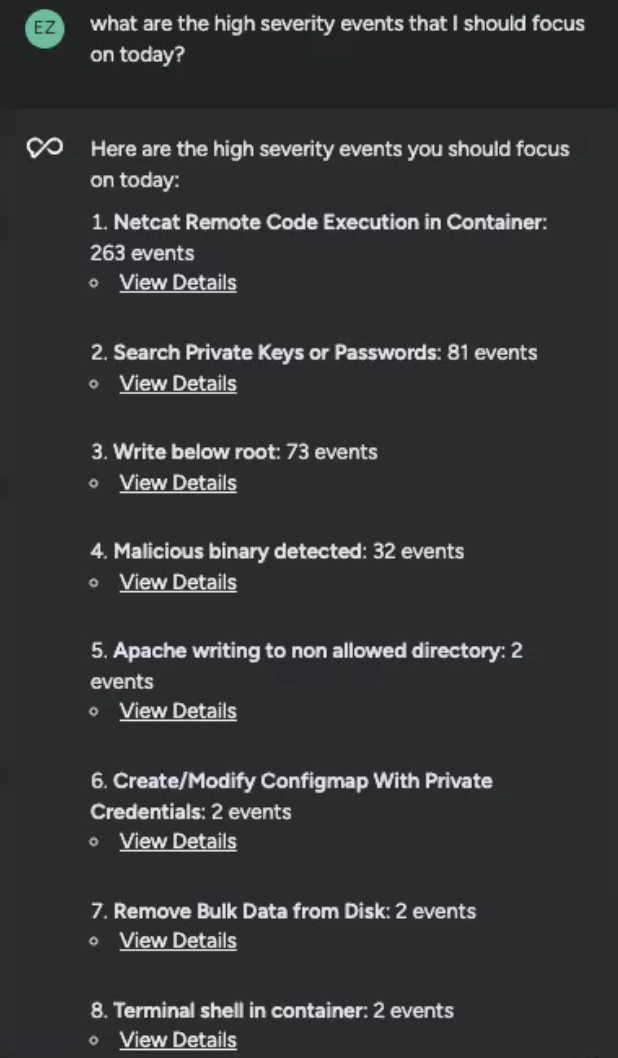
Sysdig Sage displayed an itemized checklist of the very best severity occasions. I might have gotten this checklist in different methods – Sysdig presents sturdy danger prioritization – however right here I had them multi function place, damaged down by precedence, variety of particular person occasions, and direct hyperlinks to extra particulars.
Nevertheless, taking care of additional inspecting the checklist, I seen that the primary occasion nonetheless had 263 occasions. It was a lot better than 21558, nevertheless it was nonetheless a big quantity. If I solely had eight hours in a day, I wanted to grasp methods to get all the pieces finished within the time I had.
I requested Sysdig Sage to assist set up my calendar.
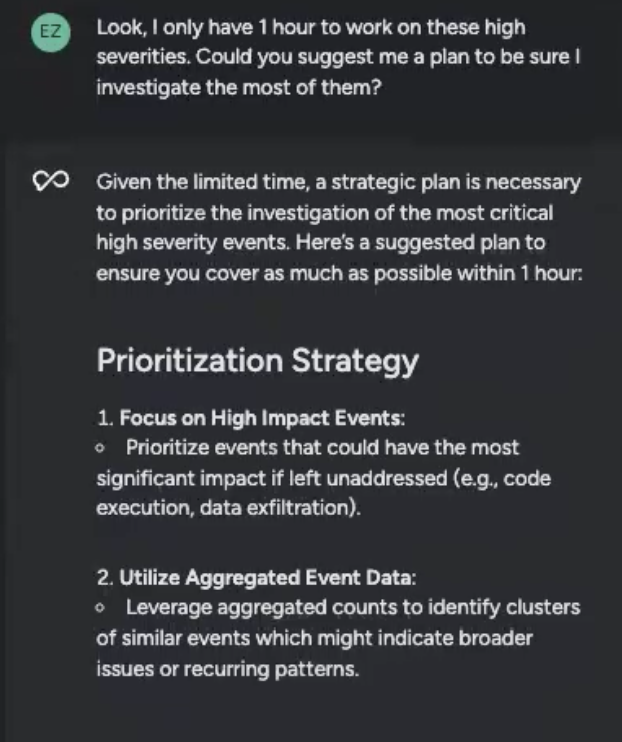
Within the output, I received a prioritization technique that outlined my duties damaged down by time estimates. Wanting on the time estimates, I would must slim down my focus, however having a plan in place makes me really feel extra assured as I begin my investigation.
Alert fatigue is without doubt one of the most difficult elements of a safety skilled’s day-to-day life. For smaller organizations with fewer sources, this may simply go from difficult to grueling. Having a instrument that helps the human defenders prioritize and speed up investigation and response is a groundbreaking subsequent step closing the cloud safety information hole.
Guided Remediation
Leaping into Sysdig Safe, my targets had been to discover a potential menace, and discover ways to remediate it. However I wasn’t positive if I might obtain them, given my lack of hands-on expertise and restricted information.
I made a decision to begin with the identical occasion we mentioned above:

This was clearly a high-severity occasion, and with the assistance of Sysdig Sage, I used to be capable of higher perceive why. However that information alone wasn’t going to make my setting any safer. What I actually wanted to know was what to do about this menace. So I turned to Sysdig Sage:
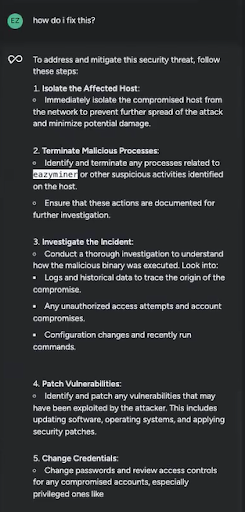
Even once I didn’t have the phrases to explain what I used to be , Sysdig Sage knew precisely the place within the UI I used to be and what I wished to repair.
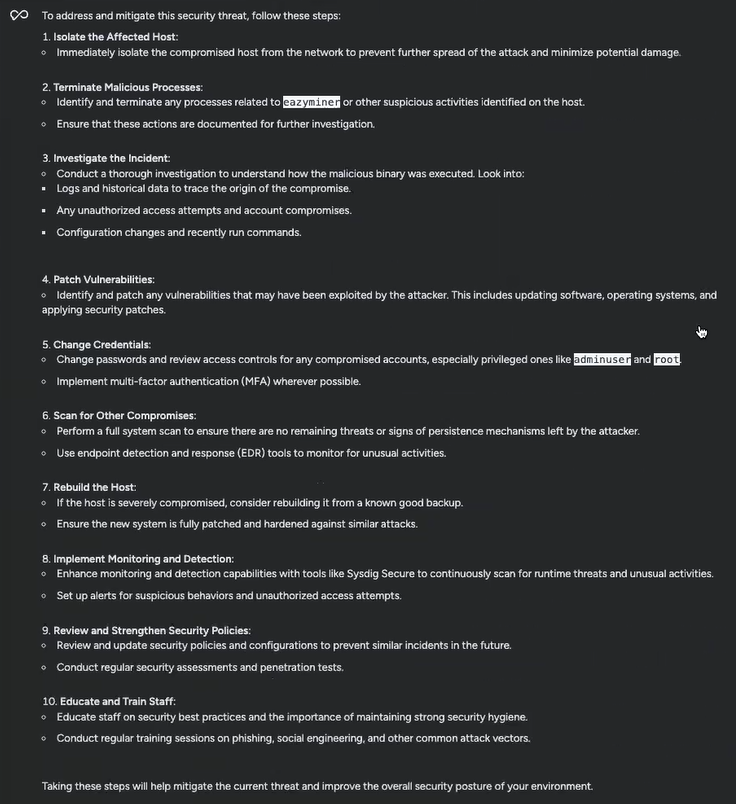
Sysdig Sage had a complete checklist of really useful remediation methods to attempt, together with isolating the host in query, terminating any processes or actions associated to the suspicious eazyminer, altering passwords, and performing a full scan for different indicators of compromise. Sysdig Sage even had some long-term solutions to forestall comparable threats from popping up sooner or later, like conducting common safety coaching with workers. For every of those solutions, it broke issues down additional into clear steps I might take.
I wished to see if Sysdig Sage might give me extra steering on methods to isolate a number.
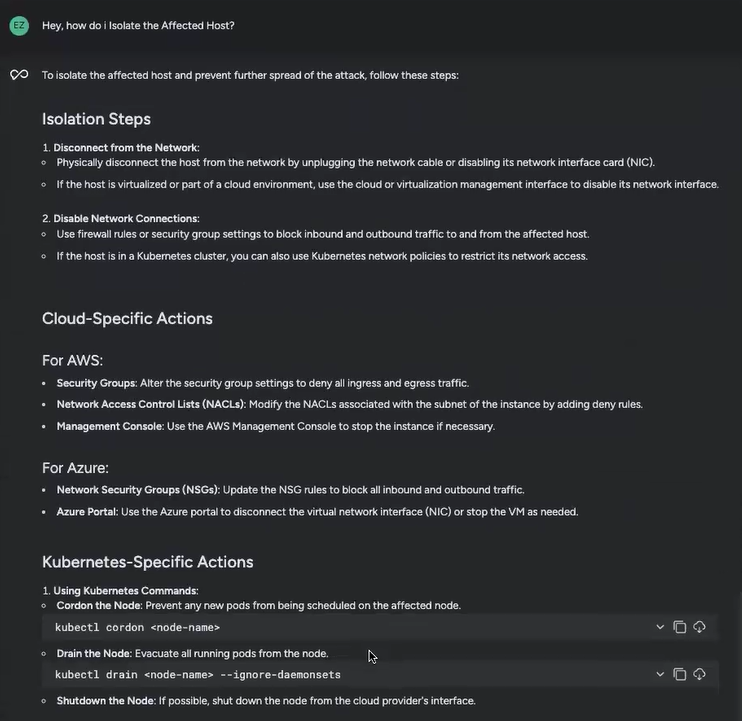
With its multi-step reasoning capabilities, Sysdig Sage remembered what we’d been speaking about and easily continued the dialog, as naturally as a human information would.
Similar to that, I had a extra detailed breakdown, with clear instructions to observe. Sysdig Sage began with broad instructions, like disconnecting from the community and disabling community connections, plus extra particular steps relying on the particular setting. It additionally instructed me what do to subsequent after isolating the host:
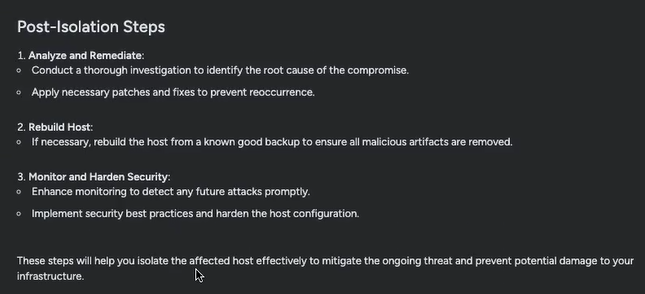
However what if it wasn’t that straightforward? What if this wasn’t simply an remoted incident of, say, somebody setting their password as 12345, however an indication of a much bigger menace to my setting? How would I even know?
I took my worries to Sysdig Sage:
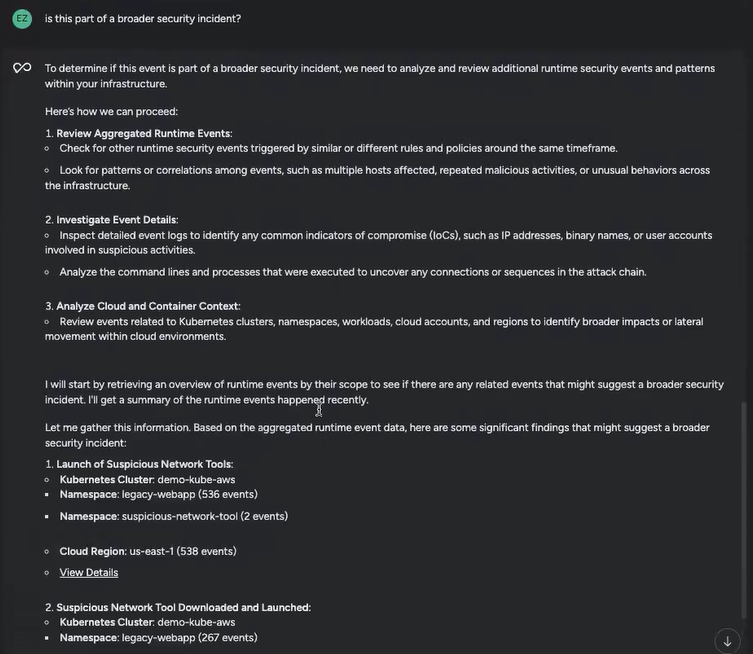
Sysdig Sage steered reviewing different occasions occurring across the identical timeframe and looking for patterns or similarities. It additionally really useful occasions occurring in different elements of my infrastructure to test for lateral motion.
Now, I knew the steps I might take to see if a broader safety incident was occurring. Combing by way of all the opposite latest occasions and attempting to determine what would possibly represent a sample would nonetheless have been a frightening prospect, however Sysdig Sage instantly began wanting into that information for me.
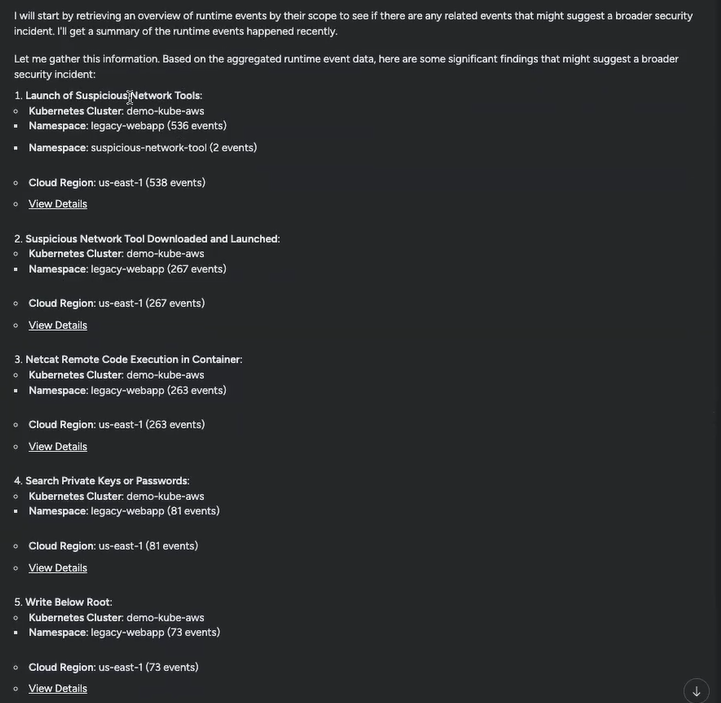
Sysdig Sage discovered a number of teams of occasions that seemed much like the malicious binary one, cataloged their primary particulars for me, and included hyperlinks to evaluation the total lists of occasions. After the final group of occasions, it got here to a conclusion:
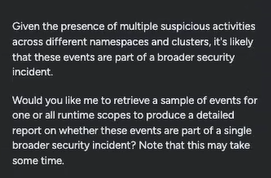
I began this train looking at a important runtime occasion, with no thought methods to proceed. However inside minutes, I had been capable of study precisely what I wanted to do to deal with the person menace in phrases I understood or I might ask extra questions if I wanted extra data. I’d confirmed the probability of a broader incident and was now able to kickstart a full investigation.
Sysdig Sage is for everybody
The cloud strikes quick. Skilled safety professionals in addition to freshmen must sustain. Sysdig Sage bridges the cloud safety talent hole, in order that groups of all talent ranges can shortly perceive what’s occurring of their setting and reply to threats. It serves as the perfect cloud safety analyst – permitting them to maneuver quicker and deal with what really issues.
Sysdig Sage gives context, helps to prioritize occasions, and recommends actionable steps. By guiding customers by way of complicated investigations and offering real-time remediation solutions, Sysdig Sage vastly improves decision-making and empowers everybody to take management of their setting, no matter their experience.
To study extra about how Sysdig Sage can improve your safety operations, try this weblog put up. See it in motion and expertise the ability of AI-driven investigation firsthand right here.