Web intelligence agency GreyNoise experiences that it has been monitoring giant waves of “Noise Storms” containing spoofed web visitors since January 2020. Nonetheless, regardless of intensive evaluation, it has not concluded its origin and goal.
These Noise Storms are suspected to be covert communications, DDoS assault coordination indicators, clandestine command and management (C2) channels of malware operations, or the results of a misconfiguration.
A curious facet is the presence of a “LOVE” ASCII string within the generated ICMP packets, which provides additional hypothesis as to their goal and makes the case extra intriguing.
GreyNoise printed this data hoping the cybersecurity researchers neighborhood will help resolve the thriller and uncover what’s inflicting these unusual noise storms.
Traits of the noise storms
GreyNoise observes giant waves of spoofed web visitors coming from thousands and thousands of spoofed IP addresses from varied sources resembling QQ, WeChat, and WePay.
The “storms” create huge visitors directed to particular web service suppliers like Cogent, Lumen, and Hurricane Electrical however keep away from others, most notably Amazon Net Providers (AWS).
The visitors primarily focuses on TCP connections, notably concentrating on port 443, however there’s additionally an abundance of ICMP packets, recently together with an embedded ASCII string “LOVE” inside them, as proven beneath.
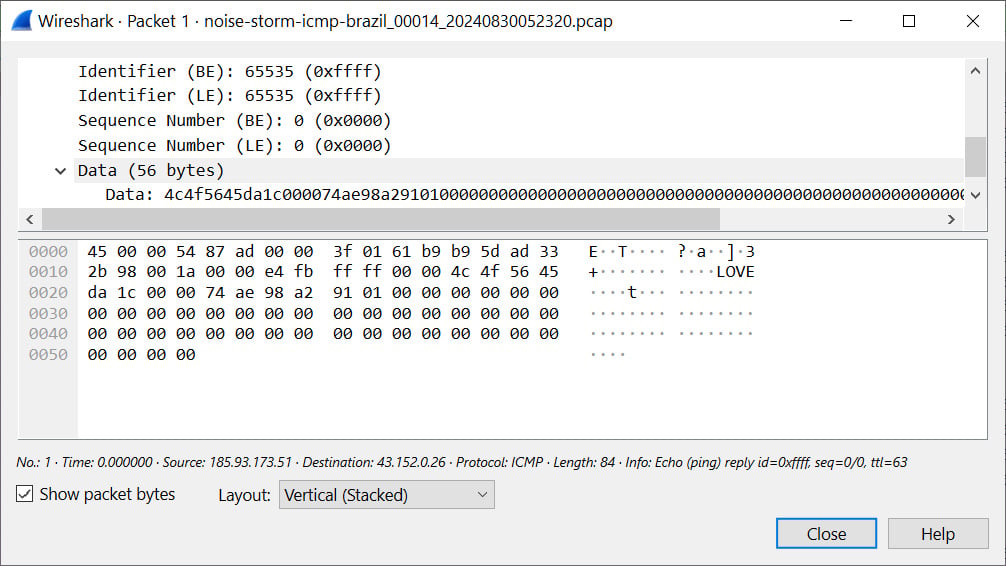
Supply: BleepingComputer
The TCP visitors additionally adjusts parameters resembling window sizes to emulate completely different working programs, conserving the exercise stealthy and tough to pinpoint.
The Time to Stay (TTL) values, which dictate how lengthy a packet stays on the community earlier than it is discarded, are set between 120 and 200 to resemble sensible community hops.
All in all, the shape and traits of those “noise storms” point out a deliberate effort by a educated actor reasonably than a large-scale aspect impact of a misconfiguration.
GreyNoise requires assist
This unusual visitors mimics official information streams, and whereas it is not identified if it is malicious, its true goal stays a thriller.
GreyNoise printed packet captures (PCAPs) for 2 latest noise storm occasions on GitHub, inviting cybersecurity researchers to be a part of within the investigation and contribute their insights or impartial discoveries that can assist resolve this thriller.
“Noise Storms are a reminder that threats can manifest in unusual and bizarre ways, highlighting the need for adaptive strategies and tools that go beyond traditional security measures,” underlines GreyNoise.
You’ll be able to be taught extra about these Noise Storms in GreyNoise’s latest Storm Watch video, proven beneath.
