Ransomware gangs like BianLian and Rhysida more and more use Microsoft’s Azure Storage Explorer and AzCopy to steal knowledge from breached networks and retailer it in Azure Blob storage.
Storage Explorer is a GUI administration software for Microsoft Azure, whereas AzCopy is a command-line software that may facilitate large-scale knowledge transfers to and from Azure storage.
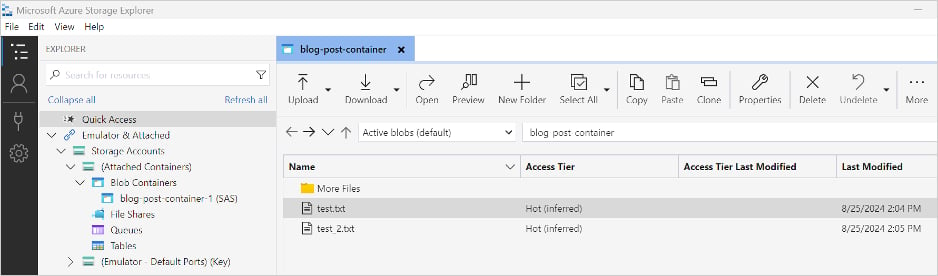
In assaults noticed by cybersecurity agency modePUSH, the stolen knowledge is then saved in an Azure Blob container within the cloud, the place it may possibly later be transferred by the risk actors to their very own storage.
Supply: modePUSH
Nonetheless, the researchers famous that the attackers needed to put in additional work to get Azure Storage Explorer working, together with putting in dependencies and upgrading .NET to model 8.
That is indicative of the rising give attention to knowledge theft in ransomware operations, which is the principle leverage for risk actors within the ensuing extortion part.
Why Azure?
Although every ransomware gang has its personal set of exfiltration instruments, ransomware gangs generally use Rclone for syncing information with numerous cloud suppliers and MEGAsync for syncing with MEGA cloud.
Azure, being a trusted enterprise-grade service that’s typically utilized by firms, is unlikely to be blocked by company firewalls and safety instruments. Subsequently, knowledge switch makes an attempt by it usually tend to undergo and go undetected.
Moreover, Azure’s scalability and efficiency, permitting it to deal with giant volumes of unstructured knowledge, is very helpful when attackers try and exfiltrate giant numbers of information within the shortest potential time.
modePUSH says it noticed ransomware actors utilizing a number of situations of Azure Storage Explorer to add information to a blob container, dashing up the method as a lot as potential.
Detecting ransomware exfiltration
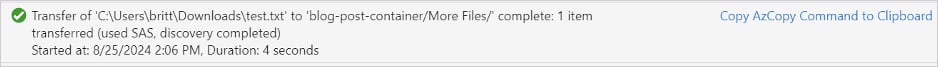
The researchers discovered that the risk actors enabled default ‘Data’ stage logging when utilizing Storage Explorer and AzCopy, which creates a log file at %USERPROFILE%.azcopy.
This log file is of explicit worth to incident responders, because it comprises data on file operations, permitting investigators to shortly decide what knowledge was stolen (UPLOADSUCCESSFUL) and what different payloads had been doubtlessly launched (DOWNLOADSUCCESSFUL).
Supply: modePUSH
Protection measures embrace monitoring for AzCopy execution, outbound community site visitors to Azure Blob Storage endpoints at “.blob.core.windows.net” or Azure IP ranges, and setting alarms for uncommon patterns in file copying or entry on vital servers.
If Azure is already utilized in a company, it is suggested to examine the ‘Logout on Exit’ choice to routinely signal out upon exiting the applying, in order to forestall attackers from utilizing the energetic session for file theft.
