DragonRank, a Chinese language-speaking hacking group, has compromised 30+ Home windows servers globally. They exploit IIS vulnerabilities to govern search engine optimization rankings, distribute rip-off web sites, and unfold malware like PlugX and BadIIS.
A Chinese language-speaking hacking group, often called “DragonRank,” has been found compromising over 30 Home windows servers throughout the globe, together with in Thailand, India, Korea, Belgium, Netherlands, and China.
The group’s main aim is to govern search engine crawlers and disrupt the Search Engine Optimization (search engine optimization) of affected websites, finally distributing rip-off web sites to unsuspecting customers.
How the Assault Works
The DragonRank hacking group features preliminary entry to Home windows Web Info Companies (IIS) servers by exploiting vulnerabilities in net utility companies, reminiscent of phpMyAdmin, WordPress, or comparable net purposes. As soon as they acquire the flexibility to execute distant code or add recordsdata on the focused website, they deploy an online shell like ASPXspy, granting them management over the compromised server.
Based on Cisco Talos’ lengthy and technical report shared with Hackread.com forward of publishing on Tuesday, the group then makes use of the online shell to gather system info and launch malware, together with PlugX and BadIIS, in addition to credential-harvesting utilities like Mimikatz, PrintNotifyPotato, BadPotato, and GodPotato. Additionally they breach extra Home windows IIS servers within the goal’s community, both via net shell deployment or by exploiting distant desktop logins utilizing acquired credentials.
On your info, PlugX is a widely known RAT (distant entry instrument) outfitted with modular plugins and property configurations, deployed by numerous Chinese language-speaking cyber risk actors for over ten years. The PlugX configuration on this marketing campaign incorporates all vital values and knowledge to correctly run the executable.
Alternatively, BadIIS is a malware used to govern search engine crawlers and hyperlink jumps. The model of BadIIS detected on this marketing campaign shares comparable traits with the one talked about (PDF) at Black Hat USA 2021, together with configuration as an IIS proxy and capabilities for search engine optimization fraud.
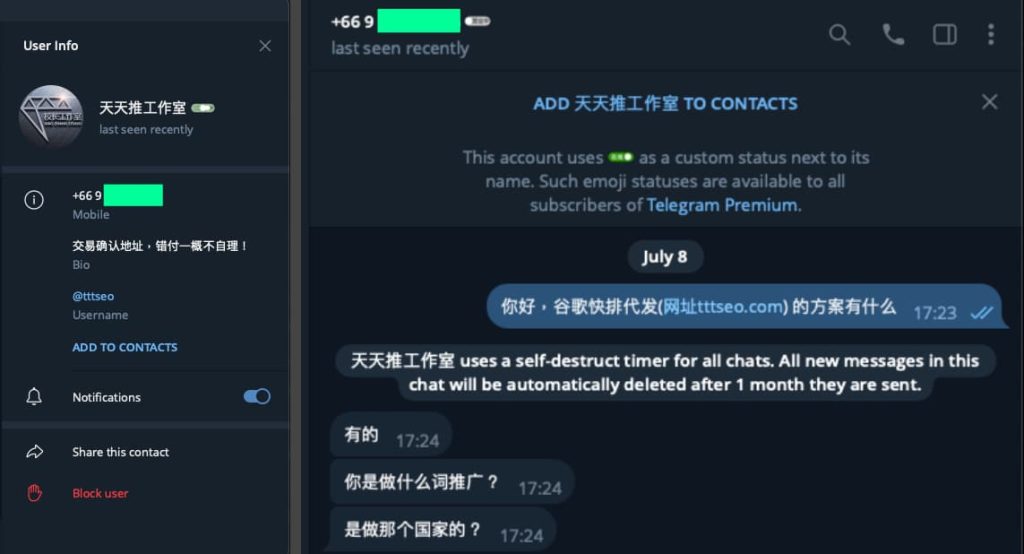
Apparently, researchers additionally famous that DragonRank operates very like a enterprise, with a industrial web site providing their companies in each Chinese language and English. They interact with purchasers via platforms like Telegram and QQ, offering tailor-made search engine optimization fraud companies. Their enterprise mannequin features a cautionary be aware about transaction confirmations, suggesting they function with a stage of professionalism unusual in typical cybercrime teams.
Nonetheless, the DragonRank hacking group’s actions are a risk to on-line safety, as they will drive visitors to malicious websites, enhance the visibility of fraudulent content material, or disrupt rivals by artificially inflating or deflating rankings.
These assaults can hurt an organization’s on-line presence, result in monetary losses, and injury its popularity by associating the model with misleading or dangerous practices. Subsequently, companies and IT departments should:
- Use Superior Menace Detection: Implement options that may detect and reply to classy malware like PlugX.
- Usually Replace Safety Measures: Guarantee all techniques, particularly net servers, are patched in opposition to recognized vulnerabilities.
- Monitor Community Visitors: Search for uncommon outbound connections or modifications in server conduct that may point out malware like BadIIS.
- Educate Workers: Consciousness coaching on cyber threats might help in early detection of phishing or different social engineering makes an attempt.
RELATED TOPICS
- Chinese language SMS Phishing Group Hits iPhone Customers in India Publish Rip-off
- ValleyRAT Malware Targets Chinese language Home windows Customers in New Assault
- Chinese language Velvet Ant APT Goal F5 Units in Years-Lengthy Espionage
- “Unfading Sea Haze” Hackers Hit Army Targets in South China Sea
- Chinese language Blackwood APT Deploys NSPX30 Backdoor in Cyberespionage