The RansomHub ransomware gang has been utilizing TDSSKiller, a reliable device from Kaspersky, to disable endpoint detection and response (EDR) companies on course programs.
After taking down the defenses, RansomHub deployed the LaZagne credential-harvesting device to extract logins from numerous utility databases that might assist transfer laterally on the community.
TDSSKiller abused in ransomware assaults
Kaspersky created TDSSKiller as a device that may scan the system for the presence of rootkits and bootkits, two kinds of malware which can be notably tough to detect and might evade normal safety instruments.
EDR brokers are extra superior options that function, at the least partially, on the kernel degree, as they should monitor and management low-level system actions equivalent to file entry, course of creation, and community connections, all offering real-time safety towards threats like ransomware.
Cybersecurity firm Malwarebytes studies that they lately noticed RansomHub abusing TDSSKiller to work together with kernel-level companies utilizing a command line script or batch file that disabled the Malwarebytes Anti-Malware Service (MBAMService) operating on the machine.
Supply: Malwarebytes
The reliable device was employed following the reconnaissance and privilege escalation section, and executed from a short lived listing (‘C:Users<User>AppDataLocalTemp’) utilizing a dynamically generated filename (‘{89BCFDFB-BBAF-4631-9E8C-P98AB539AC}.exe’).
Being a reliable device signed with a legitimate certificates, TDSSKiller doesn’t danger RansomHub’s assault getting flagged or stopped by safety options.
Subsequent, RansomHub used the LaZagne device in an try to extract credentials saved in databases utilizing LaZagne. Within the assault that Malwarebytes investigated, the device generated 60 file writes that have been doubtless logs of the stolen credentials.
The motion to delete a file might be the results of the attacker making an attempt to cowl their exercise on the system.
Defending towards TDSSKiller
Detecting LaZagne is easy as most safety instruments flag it as malicious. Nonetheless, its exercise can change into invisible if TDSSKiller is used to deactivate the defenses.
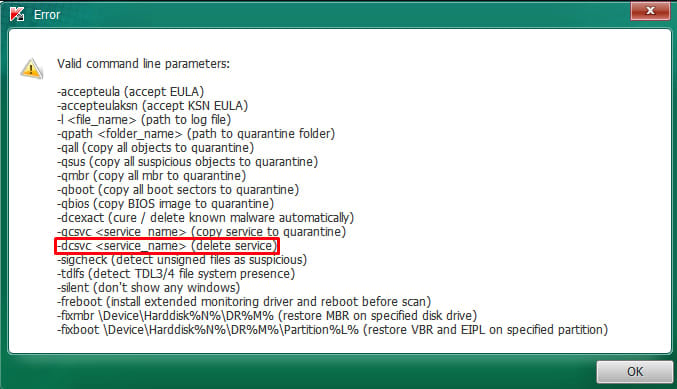
TDSSKiller is in a grey space, as some safety instruments, together with Malwarebytes’ ThreatDown, label it as ‘RiskWare’, which may be a purple flag to customers.
The safety agency suggests activating the tamper safety characteristic on the EDR resolution, to ensure that attackers cannot disable them with instruments like TDSSKiller.
Moreover, monitoring for the ‘-dcsvc’ flag, the parameter that disables or deletes companies, and for the execution of TDSSKiller itself will help detect and block the malicious exercise.
