The Voldemort Malware marketing campaign is spreading globally with over 20,000 phishing emails to greater than 70 organizations, with a peak of 6,000 emails despatched in a single day.
A newly recognized malware marketing campaign, dubbed “Voldemort,” has been spreading stealthily throughout the globe, concentrating on organizations in varied sectors together with insurance coverage, aerospace, transportation, and schooling.
The marketing campaign, which started on August 5, 2024, has already despatched over 20,000 phishing emails to greater than 70 organizations, with a peak of 6,000 emails despatched in a single day. The malicious exercise is considered a part of a classy cyber espionage effort, based on a current report by Proofpoint.
A Subtle Assault Chain
The Voldemort marketing campaign employs a fancy assault chain, combining each frequent and weird strategies. Probably the most notable points is using Google Sheets for command and management (C2) operations—an unusual technique that highlights the creativity of the risk actors.
Assault Overview:
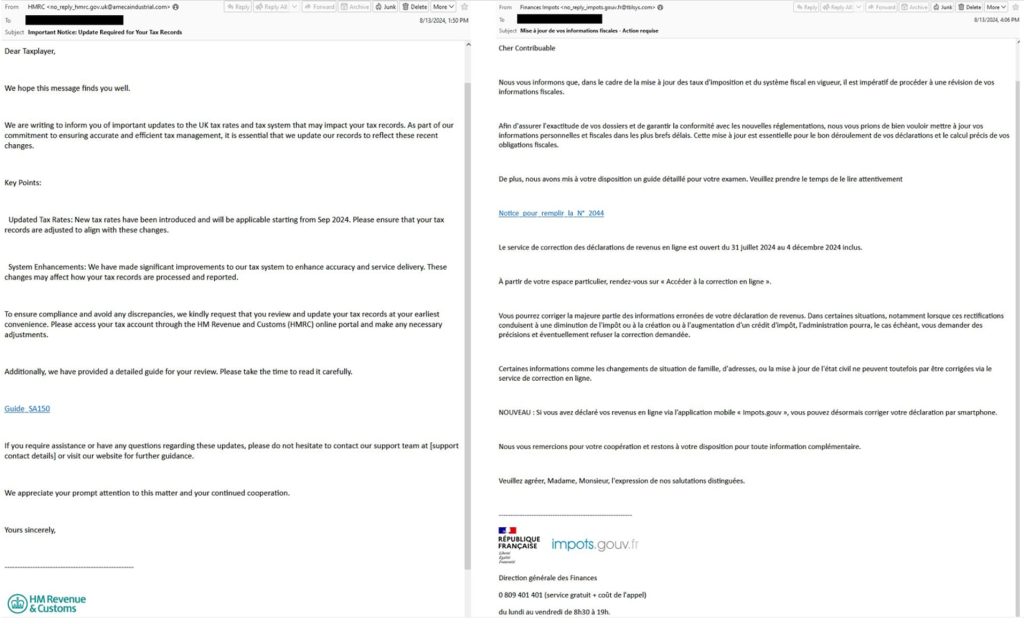
In line with Proofpoint’s technical weblog submit shared with Hackread.com forward of publishing, the assault marketing campaign begins with phishing emails that appear to originate from authentic tax companies. These emails include hyperlinks directing the recipient to a touchdown web page hosted on InfinityFree or on to a malicious file.
When victims click on the “View Document” button on the touchdown web page, the browser’s Person Agent is checked. If the system is recognized as Home windows, the person is redirected to a search-ms URI, which silently prompts Home windows Explorer to show a shortcut (LNK) file or a ZIP file disguised as a PDF.
If the sufferer executes the LNK file, it triggers a sequence of actions resulting in the deployment of the Voldemort malware. This malware is able to amassing system info, importing information, and executing extra instructions from a command-and-control (C2) server.
Uncommon Strategies with Cybercrime Vibes
Whereas the marketing campaign’s traits recommend a give attention to cyber espionage, some ways are extra generally related to cybercriminal exercise. As an illustration, the abuse of Home windows search protocols (search-ms) to deploy distant entry trojans (RATs) is a way more and more seen in cybercrime.
Moreover, the marketing campaign’s use of Cloudflare Tunnels—particularly the TryCloudflare function—permits the risk actors to create one-time tunnels without having an account, including one other layer of anonymity and making detection tougher.
The Voldemort Backdoor
Voldemort is a customized backdoor written in C, that includes superior capabilities for info gathering. It leverages CiscoCollabHost.exe, a authentic executable weak to DLL hijacking, to load the malicious DLL. The malware then communicates with its C2 server utilizing Google Sheets, the place it will probably execute instructions corresponding to downloading information, executing applications, and extra.
The malware additionally employs a singular string decryption technique and dynamically invokes APIs, strategies usually seen in additional refined threats like Cobalt Strike.
Attribution: A Thriller
Up to now, Proofpoint has not been capable of attribute this marketing campaign to any recognized risk actor with excessive confidence. The combination of superior espionage strategies and extra frequent cybercrime ways complicates the attribution course of. The massive scale of the marketing campaign, mixed with the excessive stage of customization within the malware, means that it may very well be the work of a sophisticated persistent risk (APT) group.
Commenting on this, Mr. Mayuresh Dani, Supervisor, Safety Analysis, at Qualys Menace Analysis Unit suggested organisations worldwide to implement correct safety measures to sort out Voldemort malware and different such threats.
“Organizations should take reactive and proactive means of protecting employee data starting with implementing spam filters – with strict settings for certain users at risk. AI and LLMs’ spam and language filters should be employed for first time email senders from unknown/untrusted domain names,” Mayuresh mentioned.
“They should also enforce user education that will help weed out any spurious emails that are eventually delivered. As a reactive means, they should monitor leaks sources for key resources in the company and have them scrubbed,” he suggested.
Why It Issues
The Voldemort malware marketing campaign makes use of blended strategies, making it tough to distinguish between cybercrime and espionage. The marketing campaign’s capability to evade detection utilizing unconventional C2 strategies like Google Sheets, its world attain, and high-profile targets present that cybercriminals will at all times be a step forward except customers grasp the fundamentals of cybersecurity to guard themselves.
RELATED TOPICS
- Unicode QR Code Phishing Rip-off Bypasses Conventional Safety
- Fb, Meta, Apple, Amazon Most Impersonated in Phishing
- Hackers Despatched 927,000 Phishing Emails with Malicious OAuth Apps
- Phishing Assaults Goal East European Financial institution Customers on iOS, Android
- Nespresso Area Hijacked in Phishing, Focusing on Microsoft Logins