An enormous QR code phishing marketing campaign abused Microsoft Sway, a cloud-based instrument for creating on-line displays, to host touchdown pages to trick Microsoft 365 customers into handing over their credentials.
The assaults have been noticed by Netskope Risk Labs in July 2024 after detecting a dramatic 2,000-fold improve in assaults exploiting Microsoft Sway to host phishing pages that steal Microsoft 365 credentials. This surge sharply contrasts the minimal exercise reported throughout the yr’s first half, displaying the massive scale of this marketing campaign.
They primarily focused customers in Asia and North America, with the expertise, manufacturing, and finance sectors being essentially the most sought-after targets.
The emails redirected potential victims to phishing touchdown pages hosted on the sway.cloud.microsoft area, pages that inspired the targets to scan QR codes that may ship them to different malicious web sites.
Attackers usually encourage victims to scan QR codes utilizing their cellular gadgets, which generally include weaker safety measures, thus growing the probabilities of bypassing safety controls and permitting them to entry phishing websites with out restrictions.
“Since the URL is embedded inside an image, email scanners that can only scan text-based content can get bypassed. Additionally, when a user gets sent a QR code, they may use another device, such as their mobile phone, to scan the code,” the safety researchers defined.
“Since the security measures implemented on mobile devices, particularly personal cell phones, are typically not as stringent as laptops and desktops, victims are then often more vulnerable to abuse.”
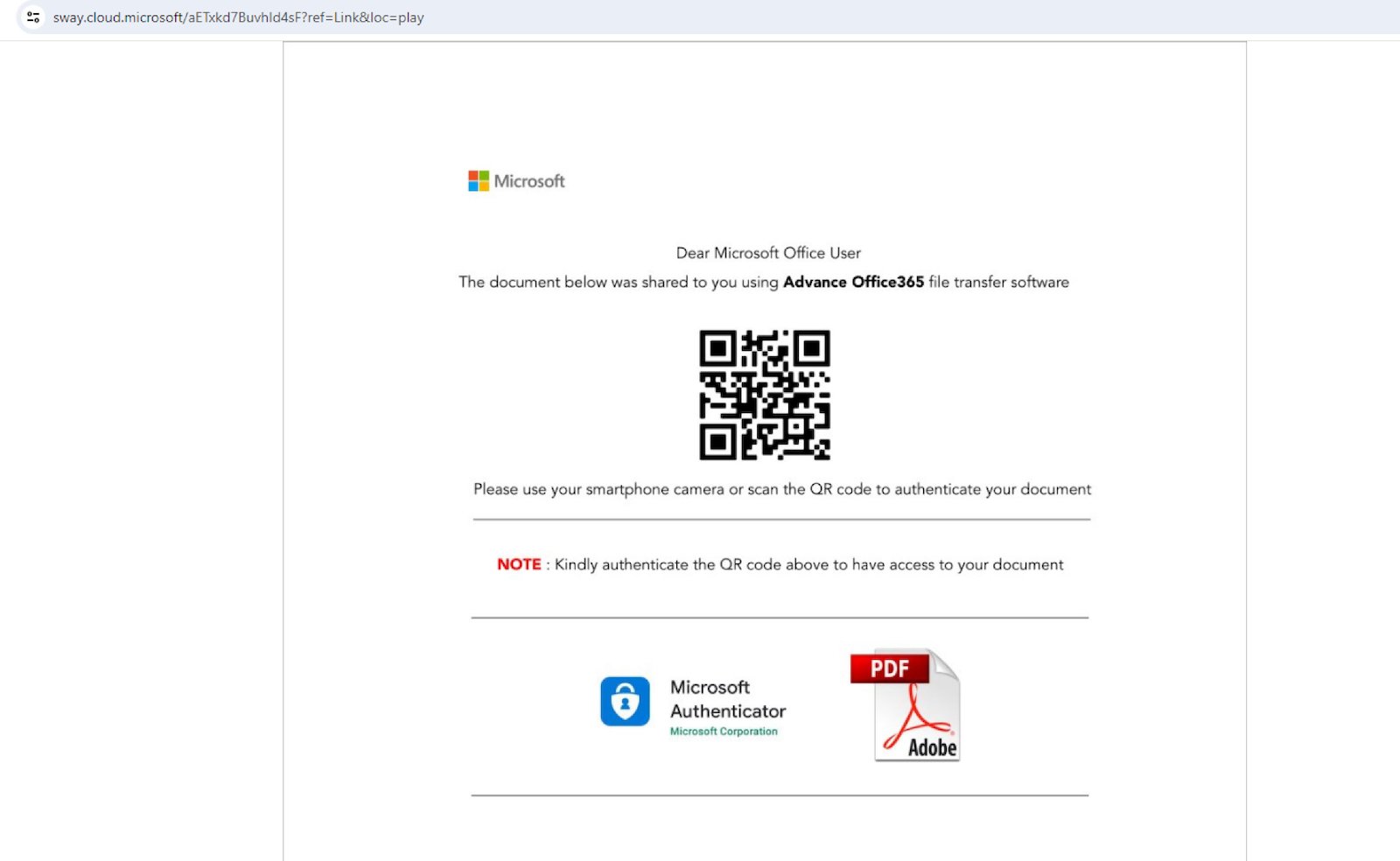
The attackers employed a number of ways to additional increase their marketing campaign’s effectiveness, like clear phishing, the place they stole the credentials and multi-factor authentication codes and used them to signal the victims into their Microsoft accounts whereas displaying them the authentic login web page.
In addition they used Cloudflare Turnstile, a instrument supposed to guard web sites from bots, to cover their touchdown pages’ phishing content material from static scanners, serving to to keep up the phishing area’s good popularity and keep away from getting blocked by net filtering companies like Google Secure Searching.
Microsoft Sway was additionally abused within the PerSwaysion phishing marketing campaign, which focused Workplace 365 login credentials 5 years in the past utilizing a phishing package provided in a malware-as-a-service (MaaS) operation.
As Group-IB safety researchers revealed on the time, these assaults tricked at the very least 156 high-ranking people at small and medium monetary companies firms, legislation companies, and actual property teams.
Group-IB stated that over 20 of all harvested Workplace 365 accounts belong to executives, presidents, and managing administrators at organizations within the U.S., Canada, Germany, the U.Ok., the Netherlands, Hong Kong, and Singapore.
