CISA has added a important Jenkins vulnerability that may be exploited to realize distant code execution to its catalog of safety bugs, warning that it is actively exploited in assaults.
Jenkins is a broadly used open-source automation server that helps builders automate the method of constructing, testing, and deploying software program by steady integration (CI) and steady supply (CD).
Tracked as CVE-2024-23897, this flaw is attributable to a weak point within the args4j command parser that unauthenticated attackers can exploit to learn arbitrary recordsdata on the Jenkins controller file system by the built-in command line interface (CLI).
“This command parser has a feature that replaces an @ character followed by a file path in an argument with the file’s contents (expandAtFiles),” the Jenkins workforce defined. “This feature is enabled by default and Jenkins 2.441 and earlier, LTS 2.426.2 and earlier does not disable it.”
A number of proof-of-concept (PoC) exploits had been revealed on-line days after Jenkins devs launched safety updates on January 24, with some honeypots reportedly catching exploitation makes an attempt simply sooner or later later.
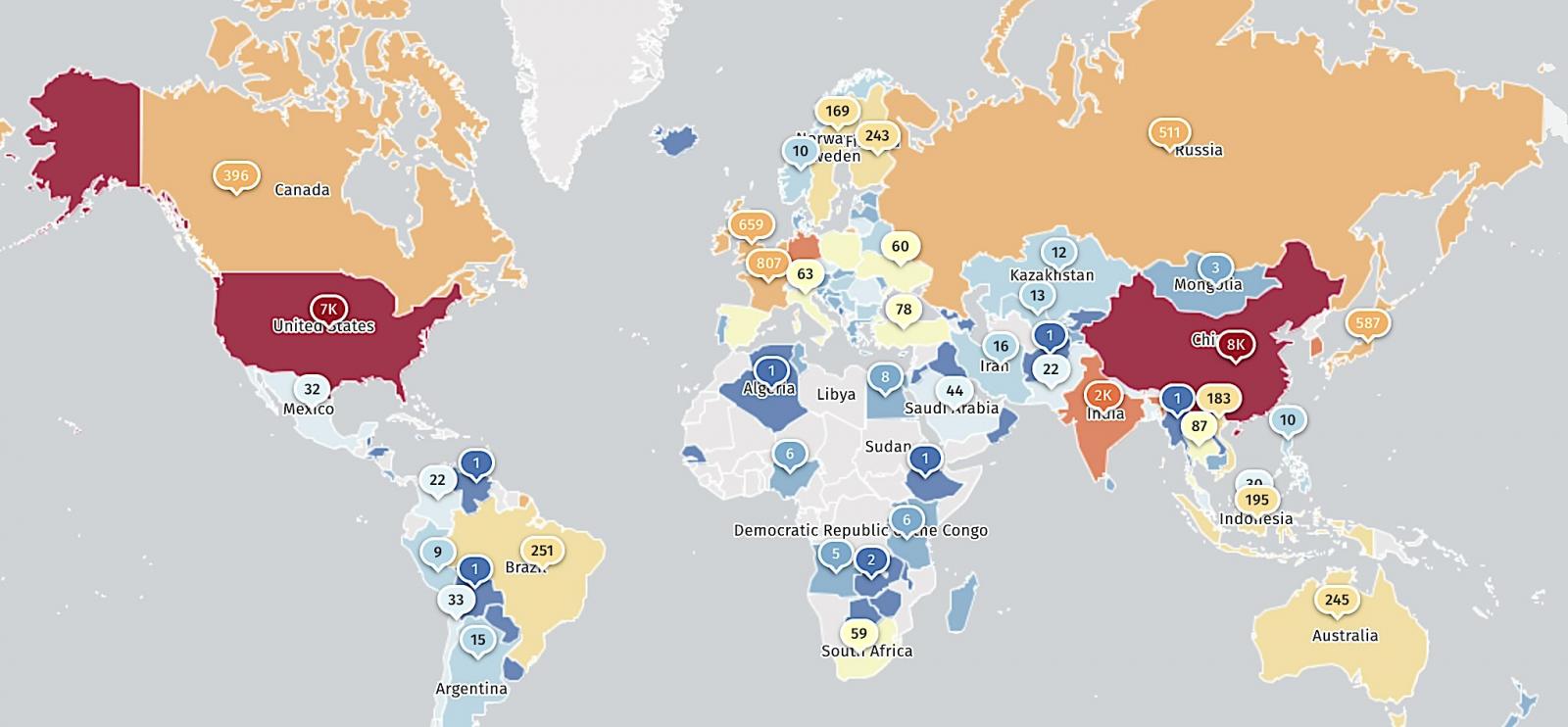
Menace monitoring service Shadowserver presently tracks over 28,000 Jenkins cases uncovered to CVE-2024-23897—most of them from China (7,700) and the USA (7,368)—indicating an enormous assault floor that has slowly decreased from greater than 45,000 unpatched servers present in January.
In response to a Pattern Micro report, CVE-2024-23897 within the wild exploitation began in March, whereas CloudSEK claimed earlier this month {that a} risk actor often known as IntelBroker had exploited it to breach IT service supplier BORN Group.
Extra not too long ago, Juniper Networks stated final week the RansomEXX gang exploited the vulnerability to breach the programs of Brontoo Expertise Options, which supplies expertise companies to Indian banks, in late July. This ransomware assault brought about widespread disruptions to retail cost programs all through the nation.
Following these experiences, CISA added the safety vulnerability to its Identified Exploited Vulnerabilities catalog on Monday, warning that risk actors are actively exploiting it in assaults.
As mandated by the binding operational directive (BOD 22-01) issued in November 2021, Federal Civilian Govt Department Companies (FCEB) companies now have three weeks till September 9 to safe Jenkins servers on their networks in opposition to ongoing CVE-2024-23897 exploitation,
Although BOD 22-01 solely applies to federal companies, CISA strongly urged all organizations to prioritize fixing this flaw and thwart potential ransomware assaults that would goal their programs.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the cybersecurity company warned as we speak.
