Belarusian-Ukrainian nationwide Maksim Silnikau was arrested in Spain and is now extradited to the USA to face expenses for creating the Ransom Cartel ransomware operation in 2021 and working a malvertising operation from 2013 to 2022.
The risk actor operated underneath the aliases “J.P. Morgan,” “xxx,” and “lansky” on Russian-speaking hacking boards, the place he allegedly promoted the cybercrime operations.
The authorities unsealed two separate indictments: one for the District of New Jersey concerning the malvertising operation and one for the Japanese District of Virginia concerning the Ransom Cartel operation.
Co-conspirators Volodymyr Kadariya, a Belarussian and Ukrainian nationwide, 38, and Andrei Tarasov, a Russian nationwide, 33, have been additionally charged for his or her position within the malvertising operation.
“These conspirators are alleged to have operated a multiyear scheme to distribute malware onto the computers of millions of unsuspecting internet users around the globe,” mentioned US Legal professional Philip R. Sellinger for the District of New Jersey. “To carry out the scheme, they used malicious advertising, or ‘malvertising’, to trick victims into clicking on legitimate-seeming internet ads.”
The UK’s Nationwide Crime Company introduced right now that Silnikau was arrested in Spain on July 18, 2023.
A world operation coordinated by the NCA has resulted within the arrest and extradition of a person believed to be one of many world’s most prolific Russian-speaking cybercrime actors.
A world operation coordinated by the NCA has resulted within the arrest and extradition of a person believed to be one of many world’s most prolific Russian-speaking cybercrime actors.
FULL STORY https://t.co/kgPdMAwqPZ pic.twitter.com/MVjRLco55R
— Nationwide Crime Company (NCA) (@NCA_UK) August 13, 2024
The Ransom Cartel operation
Ransom Cartel is a ransomware operation that launched in December 2021, sharing in depth code similarities with the REvil household.
The shortage of sturdy obfuscation prompted analysts to imagine that it was the creation of a core member who was lacking the obfuscation engine present in REvil quite than a reboot/rebrand from the identical staff of cyber criminals.
In accordance with the indictment, Silnikau created and administrated Ransom Cartel, managing the “ransomware-as-a-service” operation and recruiting different cybercriminals from Russian-speaking boards to take part in assaults.
He additionally negotiated with “initial access brokers” (IABs) who offered entry to compromised company networks, managed communications with victims, and dealt with ransom funds.
Silnikau additionally transferred ransom funds by way of cryptocurrency mixers to obscure the cash path and complicate legislation enforcement efforts, clearly holding a central position within the operation.
.png)
Supply: BleepingComputer
Reveton ransomware
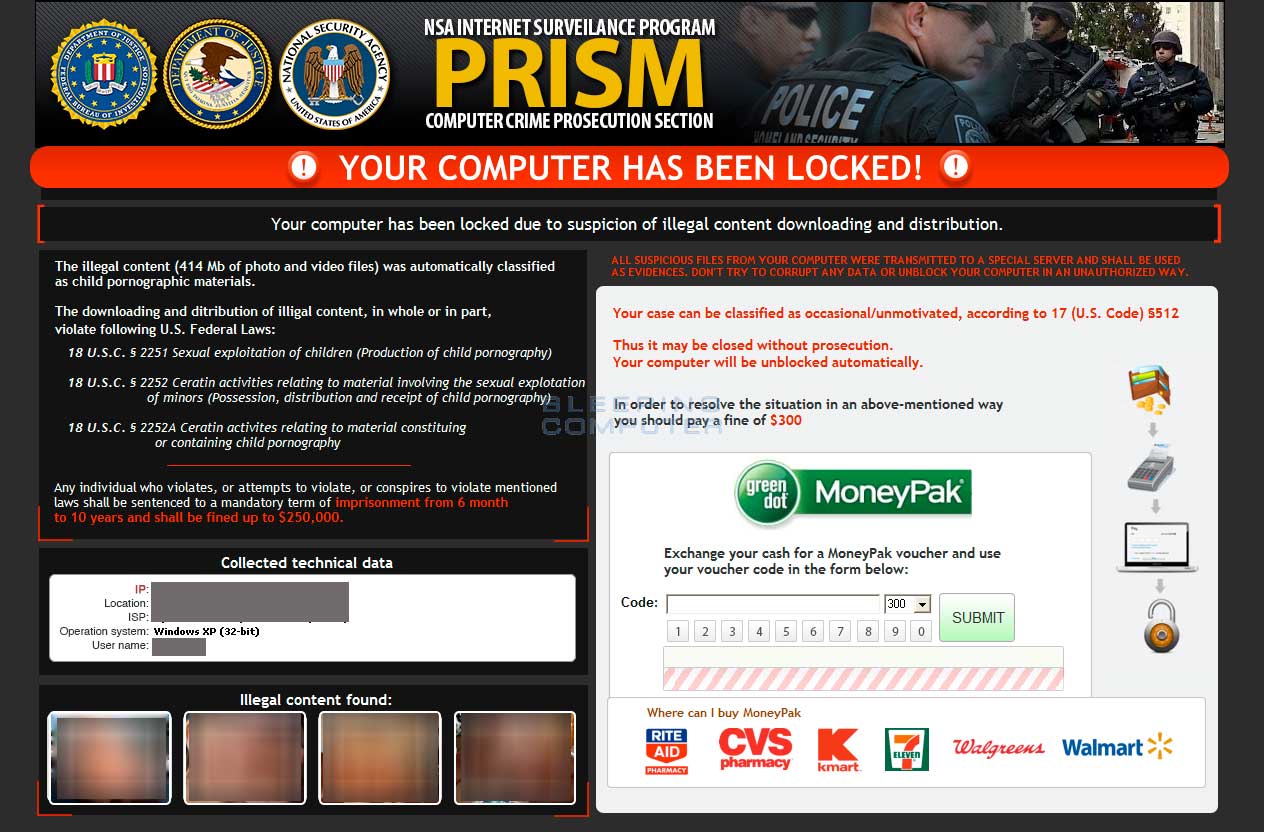
The NCA additionally states that Silnikau was behind the infamous Reveton trojan, a Home windows malware that locked customers out of the working system till a ransom was paid.
The malware launched in 2011 and pretended to be legislation enforcement locking a pc as a result of detection of kid pornography and copyrighted materials.
To realize entry to the pc, victims have been required to ship a ransom by way of MoneyPak, PaySafeCard, or different on-line funds.
Supply: BleepingComputer
The malware predominantly impersonated legislation enforcement companies from the UK and the USA.
Between 2012 and 2014, Reveton was bought to different cybercriminals who closely distributed it by way of websites compromised with exploit kits.
The NCA studies that the Reveton operation generated $400,000 each day.
The operation’s success additionally spurred different cybercriminals to launch related lockers, comparable to the Urausy and Harasom Ransomware households, which have been, in lots of instances, indistinguishable from Reveton.
Malvertising operation
The defendant can be suspected of orchestrating and executing a large-scale malvertising scheme from October 2013 to March 2022.
His major duties included creating and distributing malicious commercials that appeared reliable however redirected customers to websites containing Web Explorer exploit kits, malware, scareware, and on-line scams.
Particularly, the operation distributed the next:
- Angler Exploit Equipment (AEK): Designed to take advantage of flaws in internet browsers and plugins to ship extra payloads on the compromised units.
- Locker malware: A sort of ‘lite’ ransomware device that forestalls the sufferer from accessing their information, typically demanding a fee to revive entry.
- Scareware: Deception instruments that alleged infections on the victims’ computer systems by way of solid alerts, prompting them to obtain dangerous software program or present private info to the cybercriminals.
Silnikau used varied on-line aliases and pretend corporations to deceive the abused promoting platforms and was instantly concerned in promoting entry to units compromised by way of this scheme.
Moreover, he collaborated on creating and sustaining technical infrastructure, comparable to Visitors Distribution Methods (TDSes), to handle and goal their malicious campaigns extra successfully.
“At its peak, Angler represented 40% of all exploit kit infections, having targeted around 100,000 devices and with an estimated annual turnover of around $34 million.” – NCA
Maksim Silnikau faces important authorized penalties based mostly on the fees in each indictments, together with imprisonment sentences for wire fraud, laptop fraud, laptop fraud and abuse, aggravated id theft, and entry system fraud.
Silnikau might doubtlessly face a sentence exceeding 100 years in jail if convicted on all expenses, although the sentencing time is usually a lot shorter as a result of sentences being served concurrently.
