Amazon Net Companies (AWS) S3, or Easy Storage Service, is a extremely scalable object storage service that permits companies to retailer and retrieve any quantity of information. S3 permissions are the specific guidelines inside insurance policies that decide who can entry the service completely and extra particularly the objects inside it. Let’s dive into why managing entry is essential.
The Position of IAM Insurance policies in S3
Managing id and entry to the S3 service is significant. As a result of S3 is a storage service, it hosts delicate and business-critical information for many enterprises utilizing AWS – suppose enterprise secrets and techniques, worker data, buyer particulars, and extra.
This data is a fascinating goal in malicious cloud assaults and might probably be additional weaponized in attacker recon and lateral motion. All this being mentioned, it’s obvious how essential controlling who and what can entry this service and imposing inflexible IAM protocol is.
Moreover, AWS operates on a shared duty mannequin. Whereas AWS manages the safety of the cloud, clients are answerable for securing the companies they use, together with information safety in S3.
There are a number of IAM insurance policies (on the id, useful resource, and organizational degree) you should use to guard S3. Beneath we are going to break down the S3 service, IAM insurance policies to safe it, and customary “risky” permissions.
How one can Outline Entry to Objects in Amazon S3 Buckets
There are completely different configuration choices when wanting to regulate entry to S3 buckets and particular person objects. Let’s outline completely different entities to know:
S3 Object
An S3 object is any file or information saved in S3. Every object has related metadata and might be uniquely recognized inside a bucket –a bucket is a container for a group of objects (recordsdata). Particular person objects are what comprise delicate information and what you are attempting to regulate entry to.
Consumer Coverage
Consumer insurance policies are connected to IAM customers or teams and outline permissions for S3 operations. They’re identity-based insurance policies that element how an id can work together with S3 buckets and S3 objects.
S3 Bucket Coverage
Bucket insurance policies are connected on to an S3 bucket. They’re used to grant or deny entry to the objects throughout the bucket from completely different AWS accounts. They’re resource-based insurance policies.
S3 Entry Management Listing (ACL)
ACLs present one other layer of management over entry to buckets and objects. Each bucket and object has an ACL connected to it defining what entities can entry it and what actions they will carry out.
S3 permissions and entry might be managed utilizing ACLs or bucket and person insurance policies.
Key Components of an S3 Coverage
S3 insurance policies whether or not on the bucket or id degree have the next parts in JSON format:
Impact:
The impact defines whether or not the actions are allowed (“Effect”: “Allow”) or denied (“Effect”: “Deny”). Instance beneath exhibits an specific permit.
Principal:
The principal specifies the person, account, service, or different entity that’s allowed or denied entry to the useful resource. See instance beneath for principal being person JohnDoe.
Actions:
Actions decide what operations are allowed or denied. The instance beneath exhibits s3:GetObject and s3:GetObjectVersioning as allowed permissions.
Useful resource:
Instance: “Resource”: “arn:aws:s3:::bucket_name”. This factor specifies the S3 useful resource to which the coverage applies. Instance beneath calls out an instance bucket.
Situation:
Circumstances specify the circumstances below which the coverage grants or denies permission. For instance, you may limit entry primarily based on IP deal with or time of day. Be aware: that is elective.
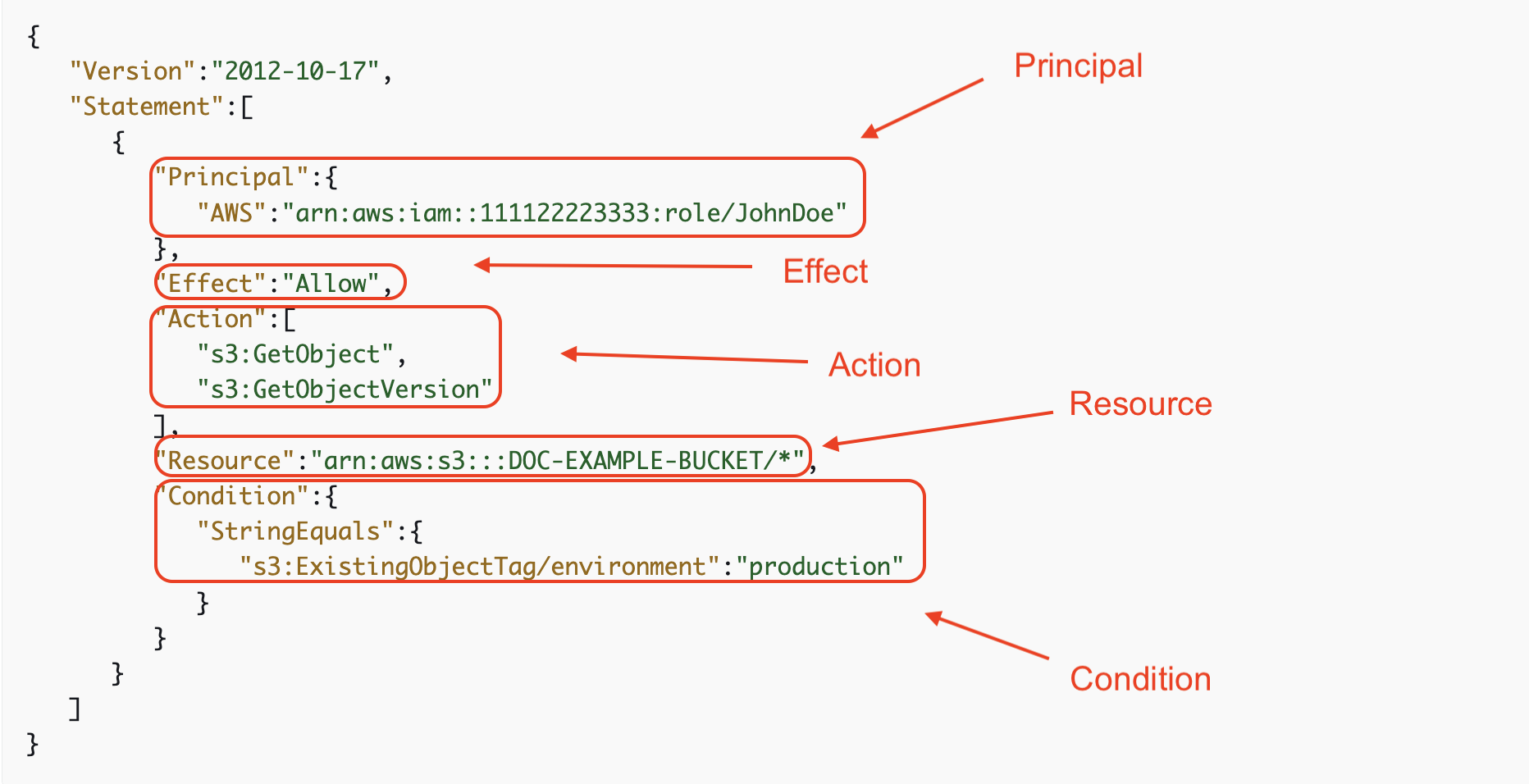
Identification coverage permitting JohnDoe GetObject and GetObjectVersioning permissions to solely objects with the outlined tag key and worth: ‘production.’
How one can Configure S3 Bucket Insurance policies
Navigate to the S3 Console
Navigate to the S3 Administration Console. Choose ‘buckets’ and select the bucket identify you need to create a coverage for. Then choose the permissions tab and below ‘bucket policy’ select ‘edit’. Right here you should use AWS coverage examples or navigate to AWS Coverage Generator.
Use AWS Coverage Generator
The AWS Coverage Generator is a great tool for creating bucket insurance policies. To make use of it, navigate to the AWS Coverage Generator webpage, choose the coverage kind as “S3 Bucket Policy,” and fill within the required assertion – extra data beneath.
Configure Statements
When constructing bucket insurance policies, configuring an announcement is essential. A press release contains the weather like Sid (assertion ID), Impact (Enable or Deny), Principal, Motion, and Useful resource. You have to rigorously configure these components to make sure the correct degree of entry. As soon as your assertion is completed, choose ‘generate policy.’ Return to the S3 console to stick it into the edit area.
Grant Permissions
Granting permissions by bucket insurance policies includes specifying the allowed or denied actions and associating them with the correct customers or person teams. This could embrace a variety of permissions, from learn and write entry to administrative permissions. For instance, to grant learn entry to a public group, you would come with “Effect”: “Allow”, “Principal”: “*”, and actions like [s3 Get Object.]
Further: Managing Buckets Utilizing ACLs
Entry Management Lists (ACLs) supply one other method to handle entry to your S3 buckets. An ACL lets you grant primary learn/write permissions to different AWS accounts. To arrange an ACL, go to the S3 Administration Console, choose the bucket, and navigate to the Permissions tab. Right here, you may add or take away accounts and specify the sorts of permissions (like learn, write, or full management) for every account. It’s essential to keep in mind that ACLs are much less granular than bucket insurance policies and are greatest used for easier entry management eventualities.
AWS S3 Actions and Permission Examples
Let’s assessment some examples of widespread s3 permissions and their related motion.
s3:GetObject | Grants permission to retrieve objects from Amazon S3.
s3:ListBucket | Grants permission to record some or the entire objects in an Amazon S3 bucket.
s3:PutAccessPointPolicy | Grants permission to affiliate an entry coverage with a specified entry level.
s3:PutAccessPointPolicyForObjectLambda | Grants permission to affiliate an entry coverage with a specified object lambda enabled entry level.
s3:PutBucketPolicy | Grants permission so as to add or exchange a bucket coverage on a bucket.
s3:DeleteBucket | Grants permission to delete the bucket named within the URI.
s3:DeleteBucketPolicy | Grants permission to delete the coverage on a specified bucket.
s3:DeleteObject | Grants permission to take away the null model of an object and insert a delete marker, which turns into the present model of the thing.
s3:GetAccessPoint | Grants permission to return configuration details about the desired entry level.
s3:GetBucketLogging | Grants permission to return the logging standing of an Amazon S3 bucket and the permissions customers should view or modify that standing.
s3:GetEncryptionConfiguration | Grants permission to return the default encryption configuration to an Amazon S3 bucket.
s3:GetObjectAcl | Grants permission to return the entry management record (ACL) of an object.
7 Greatest Practices for Managing S3 Permissions
- Securing Entry with Insurance policies and ACLs: Use IAM insurance policies (both connected to a bucket or person) to outline S3 permissions at extra granular ranges. Your groups can leverage Service Management Insurance policies (SCPs) for organization-wide guardrails round accessing S3. ACLs can be utilized to handle entry to particular person buckets and objects.
- Imposing Least Privilege: At all times adhere to the precept of least privilege, granting solely the permissions essential for an id to carry out its supposed duties. Repeatedly assessment permissions to make sure they align with present roles and tasks.
- Guaranteeing No Buckets are Public: Keep away from making S3 buckets public until completely essential. Repeatedly use instruments like AWS Trusted Advisor or S3 bucket insurance policies to audit and make sure that none of your S3 buckets are unintentionally uncovered to the general public.
- Utilizing Position-Based mostly Entry Management (RBAC): Implement RBAC to handle entry to S3 sources. This includes assigning permissions primarily based on roles inside your group and associating these roles with customers, teams, or AWS companies.
- Avoiding Wildcard Permissions: Chorus from utilizing wildcard permissions (resembling ‘*’) in insurance policies, as they will inadvertently grant broader entry than supposed. As a substitute, outline particular permissions for every person or service position.
- Preserving Permissions Granular and Particular: Tailor permissions to the precise wants of every person or service. Keep away from broad permissions and outline them as narrowly as attainable to scale back the chance of unauthorized entry.
- Monitoring Entry: Make the most of AWS CloudTrail, S3 entry logs, or third celebration CIEM options to watch who’s accessing your S3 sources and what actions they’re performing. That is essential for detecting anomalous permission or entry adjustments.
Challenges and Dangers Round S3 Permissions
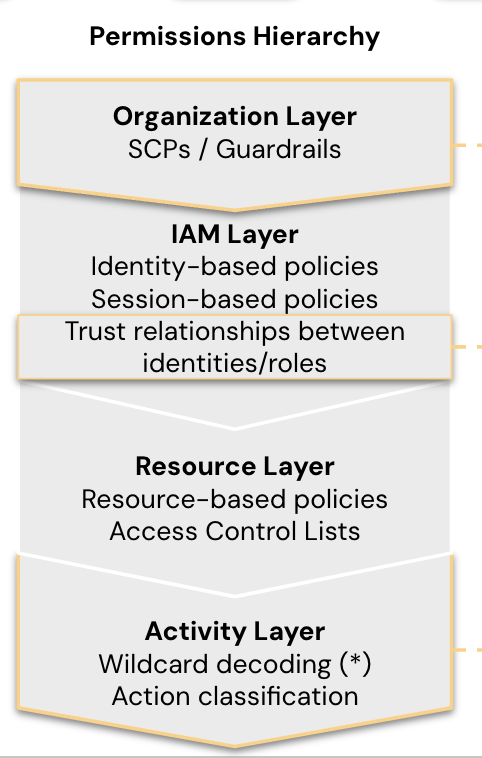
Coverage Complexity
Privilege may be very difficult within the cloud as there are a selection of various insurance policies granting privilege and privilege may even be inherited down line. In AWS alone, there are organizational insurance policies (SCPs, permission boundaries), resource-based insurance policies, and identity-based insurance policies. It’s practically unimaginable to manually see what the online impact of those intersecting insurance policies is. This implies the efficient permissions of identities might be troublesome to see. This interprets into entry your groups can’t all the time monitor, which introduces safety danger.
Troubleshooting Denied Entry
Customers attempting to entry S3 could come throughout error codes like ‘403 Forbidden’ when attempting to see objects. It may be troublesome to troubleshoot this and hint down the origin of the assertion denial in bucket insurance policies, IAM insurance policies, or any SCPs.
Misconfigurations
Configurations permit for personalisation, however additionally they introduce the potential for misconfigurations leaving the service or buckets in danger.This might be a publicly accessible bucket left open to the web, or permitting anybody to add or delete recordsdata from the bucket. Misconfigurations are a number one reason behind attacker entry into cloud environments. From right here, they will transfer laterally to additional disrupt your surroundings.
Cross-Account Entry
You may deliberately grant customers cross-account (and even multi-cloud) entry to S3 objects, however typically this entry is unintentional. Permission inheritance and coverage complexity can result in cross-account entry your groups can’t see. Any privilege your groups can’t see ‘on paper’ is harmful and is liable to being maliciously exploited or used for attacker lateral motion. Leveraging a third-party answer like CIEM gives efficient permissions visibility.
Auditing and Compliance
As per the shared duty mannequin, AWS is answerable for S3 service compliance. Nonetheless, the info saved inside S3 is your duty to make sure it’s compliant with any laws in your trade like HIPAA, PCI, FedRAMP, and many others.
S3 Permissions Administration Made Simple with Sonrai
Sonrai Safety is a CIEM answer with patented permission analytics created to ‘see’ and perceive all privilege insurance policies to compute the efficient permissions of each id. This perception fuels assault path evaluation so groups see any attainable routes to crucial companies like AWS S3 or the delicate information inside them.
Sonrai contains on-demand information entry querying to assist with any audit or compliance course of and clever workflows that assist manage and prioritize your permission remediation efforts.

