Cloud migration and steady innovation present organizations with substantial beneficial properties in velocity, scalability, and price (to call a couple of). Most safety groups don’t have any selection however to make the soar to the cloud, in no less than some capability, to assist and shield this quickly increasing assault floor.
However organizations and safety groups aren’t alone. Menace actors have been readily adapting their craft to reap the benefits of cloud velocity. In consequence, cloud assaults occur quick, quickly weaving by way of a goal’s cloud property and drawing on intensive capabilities to attain their objectives.
A main instance is the SCARLETEEL assault, which may infiltrate a company, execute cryptominers, uncover cloud credentials, pivot to different cloud accounts, and finally exfiltrate proprietary information – all in simply 220 seconds. Investigating cloud assaults like SCARLETEEL has historically been a laborious, error-prone, and guide course of. The chances are stacked towards defenders, and the truth is that safety groups are sometimes unable to analyze threats earlier than the assault completes.
That’s why the 5/5/5 Benchmark for Cloud Detection and Response – the one business normal for cloud safety – establishes that you’ve got simply 5 minutes to carry out cloud investigations to go off assaults earlier than they are often executed.
What’s new: Enhanced investigations capabilities
At the moment, Sysdig is streamlining cloud detection and response (CDR) use instances by automating the gathering and correlation of occasions, posture, and vulnerabilities to identities. The cloud context these capabilities present is unparalleled. An interactive visualization of this info helps analysts immediately conceptualize assaults, unlocking five-minute investigations throughout probably the most superior threats.
The important thing new capabilities enhancing investigations embrace:
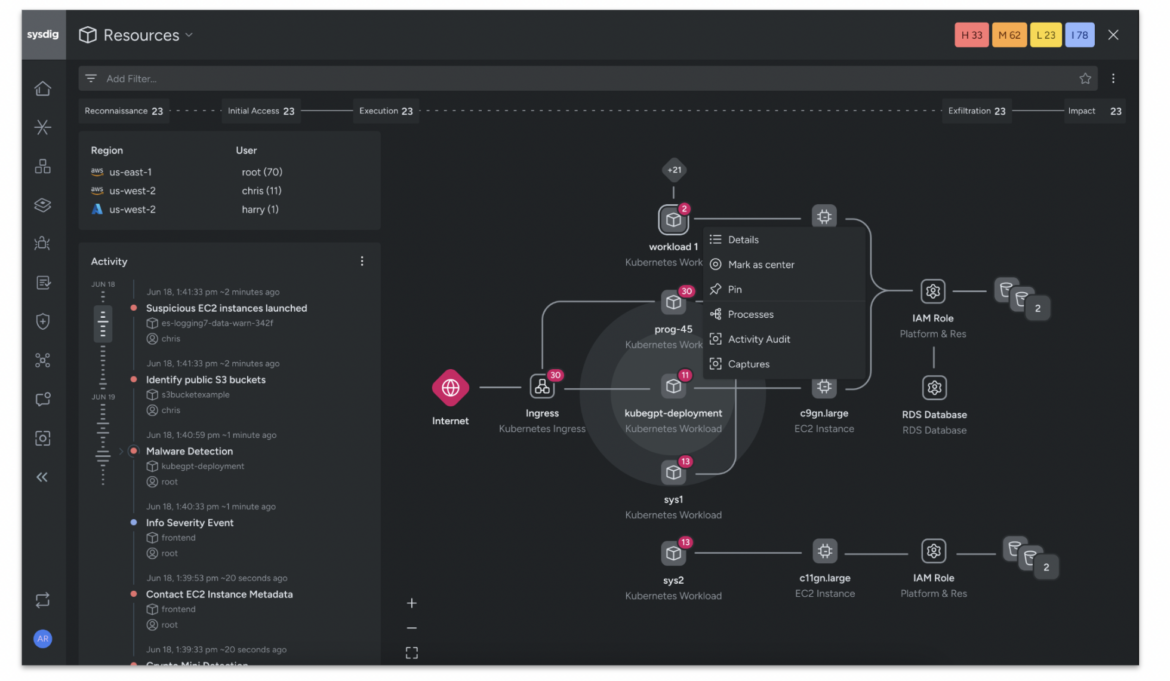
Assault chain visualization
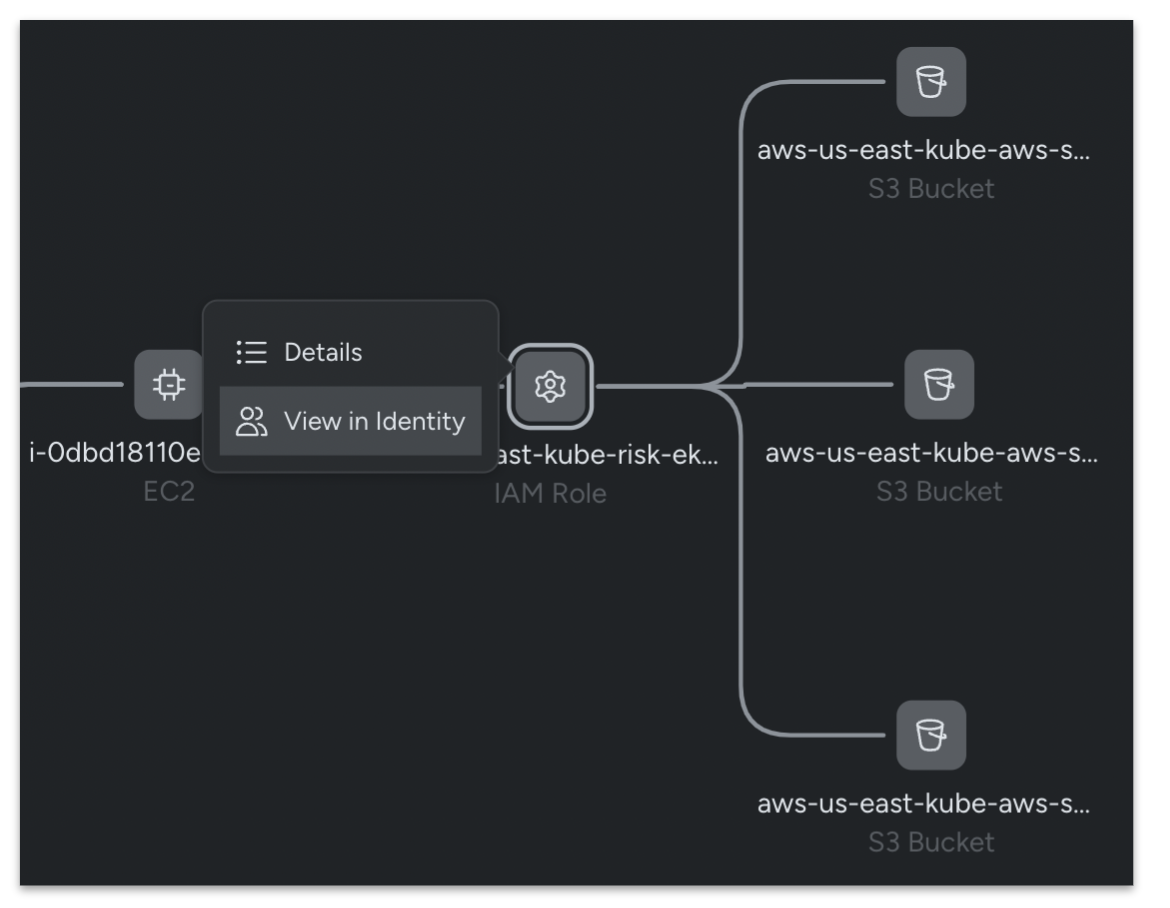
Safety groups can leverage any alert or suspicious discovering as a place to begin to launch an investigation with the Sysdig Cloud Assault Graph. The graph gives assault chain visualization and empowers safety analysts to quickly perceive the relationships between sources, and their implications for the assault chain throughout any cloud surroundings.
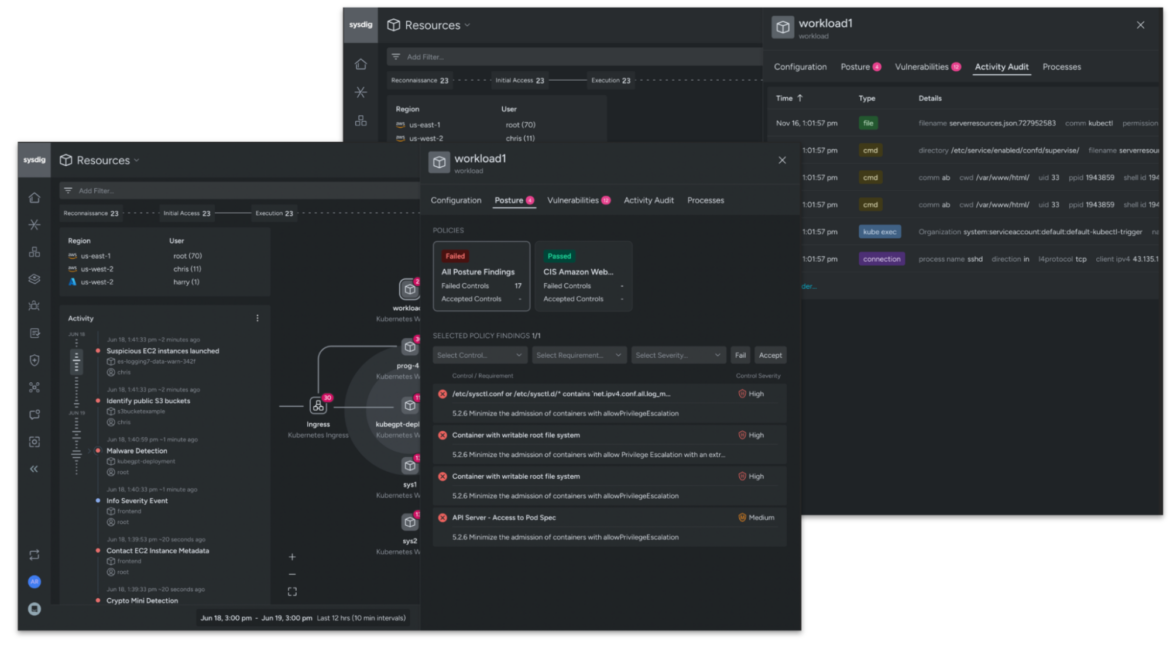
Sysdig’s assault chain visualization accelerates investigations by mechanically correlating cloud and workload occasions to identities. Deep context from command historical past, in addition to community and file exercise, is definitely gleaned from the overlays. Sysdig’s automated captures allow analysts to dig deeper by mechanically tying digital forensic proof to the occasions. Actual-time context is mixed with vulnerabilities and misconfiguration findings to supply a complete and holistic view of a risk. To additional simplify workflows, and slim an investigation window when obligatory, all investigations are MITRE-mapped and filterable.
Actual-time identification correlation
At their core, all cloud assaults revolve round identities. Whether or not it’s human or machine, one or many, analysts want a solution to sew suspicious findings to identities and their related behaviors. Sysdig’s enhanced investigation capabilities mechanically correlate cloud occasions with enriched identification information. Utilizing assault chain visualization, analysts can quickly perceive suspicious identification behaviors comparable to uncommon logins, inconceivable journey situations, and malicious IP addresses. With this context, groups can quickly perceive the who, what, the place, and the way of risk actors of their infrastructure.
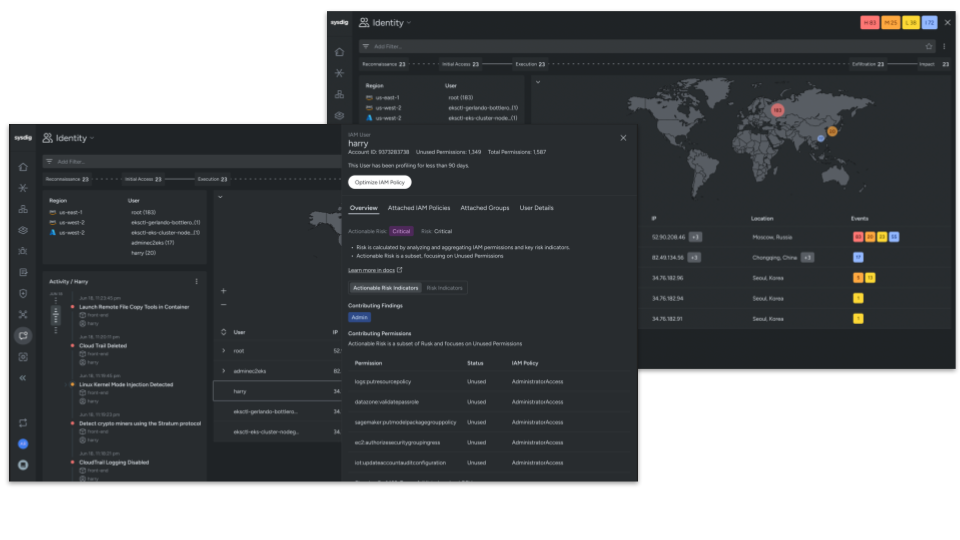
This visibility additionally helps groups to quickly rightsize extreme permissions, comparable to by configuring them to permissions from earlier than they have been compromised by a malicious adversary.
Investigation workflow optimization
A single purpose-built platform can break silos and streamline downstream actions. Safety turns into a crucial and precious enterprise companion by delivering related, high-context steerage throughout key stakeholders. Fast investigation findings allow prescriptive steerage for response actions throughout incident response, platform, developer, and DevSec groups. These accelerated findings permit response groups to provoke a response inside 5 minutes, adhering to the 5 minute response normal outlined within the 5/5/5 Benchmark.
Closing the loop, the improved incident debrief findings these investigations present (comparable to what misconfigurations, permissions, and vulnerabilities have been abused to perpetuate the assault) can then be shared to tune and harden preventive controls. This give attention to perpetual enchancment to preventative controls helps guarantee incidents are non-recurring, lowering organizational cloud danger.
Outpace cloud assaults with Sysdig’s enhanced investigations
The acceleration of cloud detection and response is crucial to fight trendy assaults. The automation-fueled tempo of cloud assaults implies that investigations should transfer even quicker. Sydig’s enhanced investigations unlock safety groups by growing effectivity, lowering ability gaps, and empowering safety and platform groups to make better-informed selections, quicker.
Be part of our upcoming webinar, Cloud Investigations in Simply 5 Minutes, for a dialogue with safety consultants on the evolution of cloud detection and response and its impacts.