A brand new ransomware operation named ‘Fog’ launched in early Could 2024, utilizing compromised VPN credentials to breach the networks of instructional organizations within the U.S.
Fog was found by Arctic Wolf Labs, which reported that the ransomware operation has not arrange an extortion portal but and was not noticed stealing knowledge.
Nevertheless, BleepingComputer can affirm the ransomware gang steals knowledge for double-extortion assaults, utilizing the information as leverage to scare victims into paying.
VPNs for preliminary entry
Fog’s operators accessed sufferer environments utilizing compromised VPN credentials from no less than two completely different VPN gateway distributors.
“In each of the cases investigated, forensic evidence indicated that threat actors were able to access victim environments by leveraging compromised VPN credentials,” explains Artic Wolf Labs.
“Notably, the remote access occurred through two separate VPN gateway vendors. The last documented threat activity in our cases occurred on May 23, 2024.”
As soon as they acquire entry to the inner community, the attackers carry out “pass-the-hash” assaults on administrator accounts, that are used to determine RDP connections to Home windows servers operating Hyper-V.
Alternatively, credential stuffing is used to hijack beneficial accounts, adopted by PsExec deployment on a number of hosts.
On Home windows servers, Fog operators disable Home windows Defender to forestall notifications alerting the sufferer earlier than the execution of the encrypter.
When the ransomware is deployed, it performs Home windows API calls to collect details about the system, such because the variety of accessible logical processors to allocate threads for a multi-threaded encryption routine.
Earlier than beginning the encryption, the ransomware terminates a listing of processes and providers primarily based on a hardcoded listing in its configuration.
The ransomware encrypts VMDK recordsdata in Digital Machine (VM) storage and deletes backups from object storage in Veeam and Home windows quantity shadow copies to forestall simple restoration.
Encrypted recordsdata are appended the ‘.FOG‘ or ‘.FLOCKED‘ extension, although this may be set from the JSON-based configuration block to something the operator needs.
Lastly, a ransom word is created and dropped on impacted directories, offering directions to the victims on paying for a decryption key that can assist them get their recordsdata again.
From an assault seen by BleepingComputer, the ransom word is known as readme.txt and accommodates a hyperlink to a Tor darkish web site used for negotiation. This web site is a primary chat interface permitting the ransomware sufferer to barter a ransom demand with the menace actors and get a listing of stolen recordsdata.
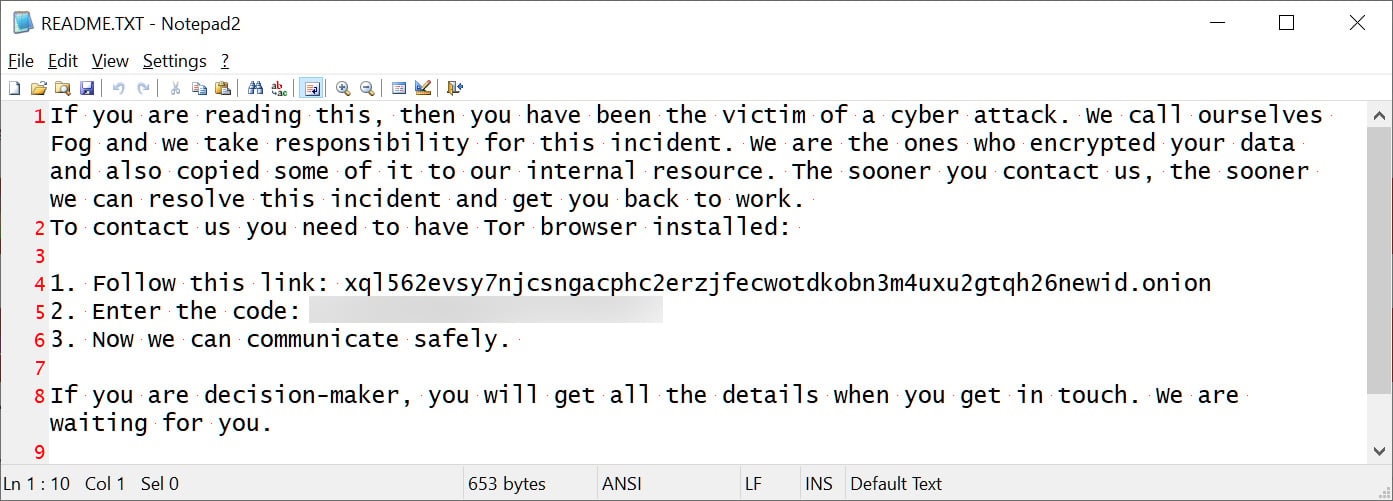
Supply: BleepingComputer
BleepingComputer also can affirm that the Tor negotiation web site is identical for each the .FOG and .FLOCKED extensions, with ongoing assaults utilizing both extension.
In an assault seen by BleepingComputer, the ransomware gang demanded a whole bunch of 1000’s to obtain a decryptor and delete the stolen knowledge. Nevertheless, it’s seemingly extra for bigger corporations.
Arctic Wolf Labs says it’s presently unclear if Fog operates as an open ransomware-as-a-service (RaaS) that accepts associates or if a small personal circle of cybercriminals is behind it.
