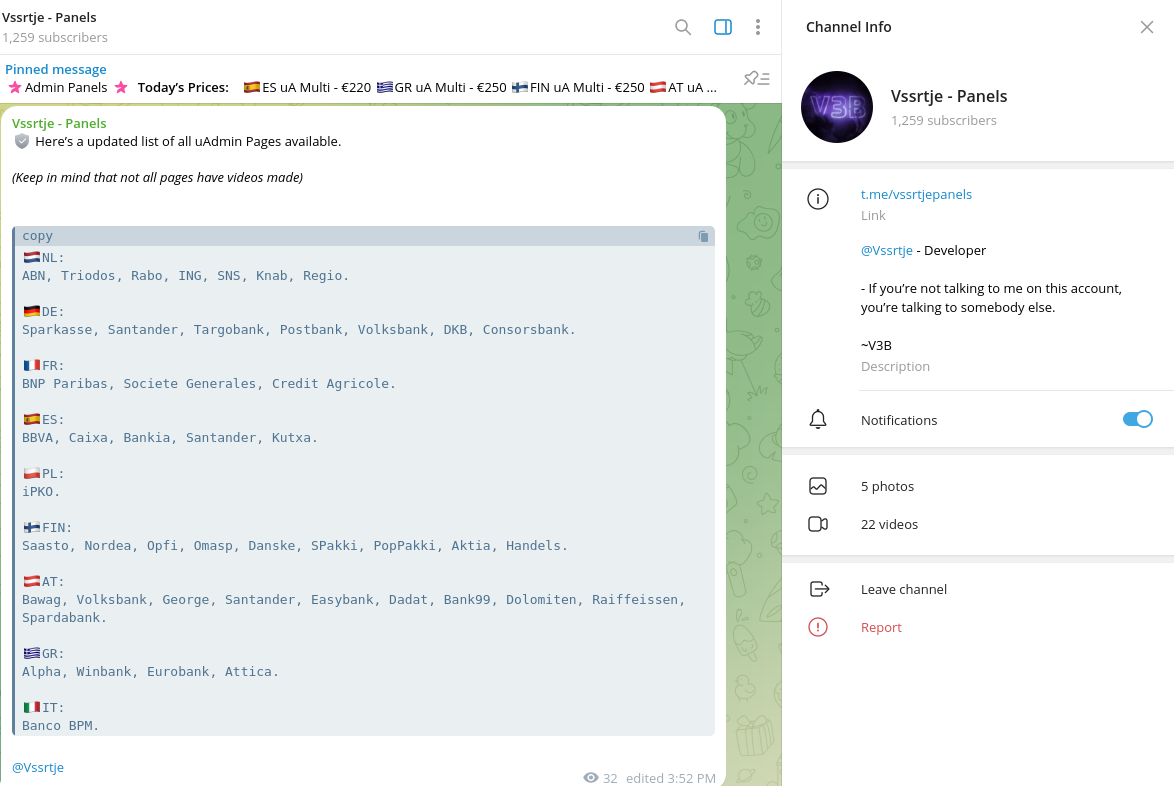
Cybercriminals are selling a brand new phishing equipment named ‘V3B’ on Telegram, which at present targets clients of 54 main monetary institutes in Eire, the Netherlands, Finland, Austria, Germany, France, Belgium, Greece, Luxembourg, and Italy.
The phishing equipment, priced between $130-$450 per 30 days relying on what’s bought, options superior obfuscation, localization choices, OTP/TAN/2FA assist, stay chat with victims, and numerous evasion mechanisms.
In line with Resecurity researchers who found V3B, its Telegram channel already counts over 1,250 members, indicating the brand new phishing-as-a-service (PhaaS) platform is rapidly gaining traction within the cybercrime house.
Supply: Resecurity
V3B options
V3B makes use of closely obfuscated JavaScript code on high of a customized CMS to evade detection by anti-phishing and search engine bots and shield from researchers.
It consists of professionally translated pages in a number of languages like Finnish, French, Italian, Polish, and German to boost the effectiveness of the phishing assaults, permitting risk actors to run multi-country campaigns.
The equipment, which is designed to work on each cell and desktop platforms, can intercept banking account credentials and data, in addition to bank card particulars.
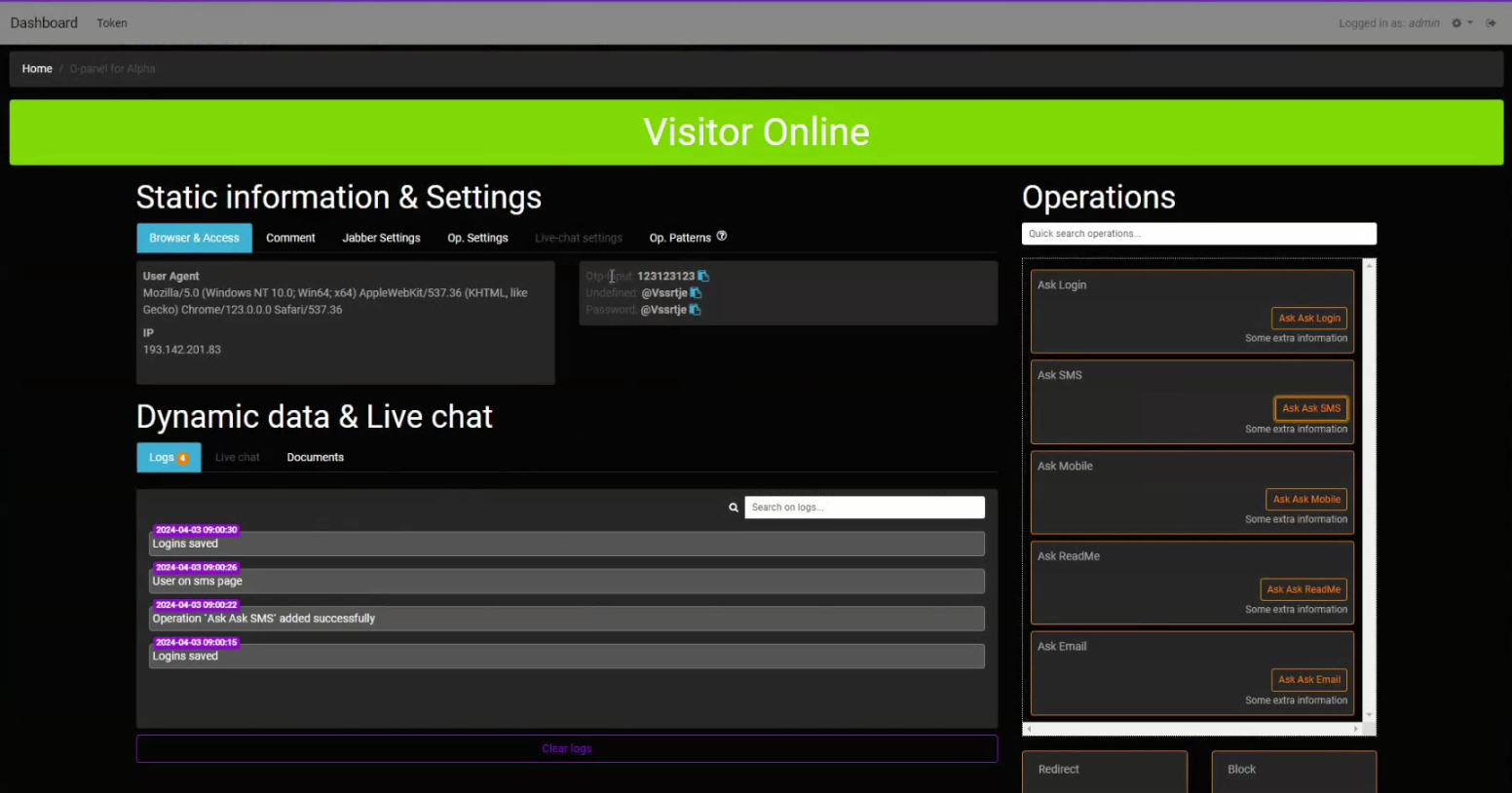
Moreover, the admin panel (uPanel) permits fraudsters to work together with victims in actual time through a chat system to acquire one-time passwords (OTPs) by sending customized notifications.
Supply: Resecurity
Stolen data is transmitted again to the cybercriminals by way of the Telegram API.
Among the many real-time interplay set off choices, there’s a QR code login jacking function that allows cybercriminals to generate QR codes for phishing pages, making the most of a false sense of legitimacy stemming from the sufferer’s familiarity with trusted companies utilizing that technique.
One other notable function of the V3B equipment is assist for PhotoTAN and Sensible ID to bypass superior authentication applied sciences that German and Swiss banks broadly use.
“Technologies used for customer authentication by banks may vary,” explains Resecurity.
“However, the fact that fraudsters have started to implement support of alternative OTP/TAN validation mechanisms, rather than relying solely on traditional SMS-based methods, may confirm the challenges that fraud prevention teams will face in combating account takeover for both private and corporate customers.”
Phishing kits are key enablers of cybercrime, permitting low-skilled risk actors to launch extremely damaging assaults in opposition to unsuspecting financial institution clients.
One of many largest PhaaS operations on the market, LabHost, which focused primarily U.S. and Canadian banks, was just lately taken down by regulation enforcement authorities.
Thirty-seven individuals, together with the unique developer, have been arrested within the regulation enforcement operation.
On the time of its bust, LabHost had 10,000 customers worldwide, launching phishing assaults by way of 40,000 domains.
