Key Factors
- Widespread Malware Distribution on GitHub: Current discoveries, together with Apiiro’s report on over 100,000 contaminated GitHub repositories, spotlight a rising pattern of utilizing GitHub for malicious functions.
- Various Assault Strategies: GitHub-based cyber threats make use of varied refined methods, together with assaults on legit repos, social engineering, and exploiting GitHub actions. This selection in assault vectors signifies the adaptability and ingenuity of cyber attackers in exploiting GitHub’s functionalities.
- Crucial Function of Steady Monitoring in Cybersecurity: The evolving nature of threats on platforms like GitHub underscores the crucial for strong, steady monitoring options.
- Checkmarx’s Proactive Protection In opposition to Provide Chain Cyber Threats: Checkmarx’s Provide Chain Safety resolution vigilantly screens malicious actions, swiftly figuring out and alerting on suspicious actions within the open supply ecosystem to successfully counteract these cyber threats.
Malicious Repo Confusion Marketing campaign
In mild of a current weblog launched by Apiiro, the cybersecurity panorama is but once more reminded of the modern methods attackers exploit platforms like GitHub to host and unfold malware. Apiiro’s findings reveal a large-scale malicious repo confusion marketing campaign impacting over 100,000 GitHub repositories, shedding mild on the evolving ways of cybercriminals. Curiously, a part of the attackers’ technique concerned creating faux forks to make their repositories appear legit, a tactic we’ve mentioned extensively in relation to repository spoofing.
The attacker took the next steps: they first cloned current repos and contaminated them with malware loaders. Subsequent, they uploaded them again to GitHub below equivalent names, robotically forking every one hundreds of instances. Lastly, they covertly promoted them throughout the online by way of boards, discord, and so on.
This isn’t an remoted case. The usage of GitHub for malicious functions has been a recurring theme, as evidenced by a number of incidents up to now.
Assaults on Respectable Repos
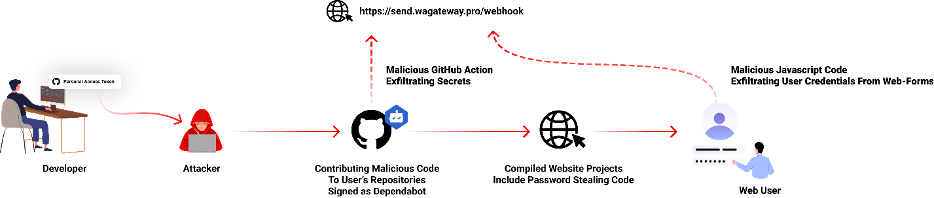
A notable technique of exploiting GitHub entails attacking legit repos. A primary instance is an incident in mid-2023the place attackers, leveraging stolen GitHub private entry tokens, impersonated Dependabot, a widely known dependency replace helper device. These tokens bypassed two-factor authentication, permitting malicious code to be dedicated below the guise of Dependabot. This code aimed to extract delicate info and inject malware into JavaScript information.
Nation-State Social Engineering Utilizing GitHub
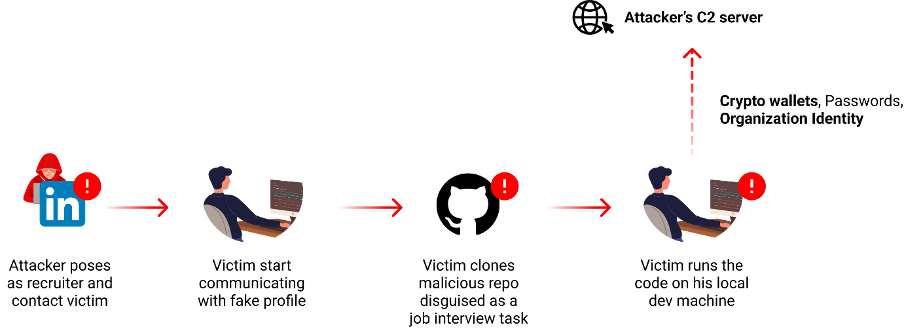
One other tactic is using social engineering. In distinction to the scrutiny sometimes given to public open-source repositories, GitHub’s non-public repositories present a extra hid avenue for attackers. A current discoveryrevealed how North Korean state actors have been utilizing these malicious repos to then combine into software program by way of social engineering, focusing on particular organizations or people.
Attacking GitHub Actions for Public Repos
In mid-2023, GitHub person account, pastramahodu, forked almost 2,000 repositories, with 319,191 whole stars mixed, as a part of a widespread bug bounty hunt try for locating misconfigurations in well-liked undertaking’s CI pipelines. The process was most certainly automated and created Pull Requests which in some tasks triggered the undertaking’s CI pipeline and executed the customized instructions. This highlighted the growing deal with pipeline safety as an entry level for provide chain assaults.
Conclusion
The recurring theme throughout these examples is evident: GitHub, a platform integral to the event group, has develop into a focus for cybercriminals trying to exploit the software program provide chain. The sophistication and number of these assaults show the evolving and protracted nature of those threats. As a part of the Checkmarx Provide Chain Safety resolution, we repeatedly monitor and detect suspicious actions within the open-source software program ecosystem, resembling these. We monitor and flag “signals” that will point out foul play and promptly alert our prospects to assist shield them. Within the face of those refined assaults, it’s extra vital than ever for builders and organizations to remain alert, frequently evaluate code sources, even from trusted platforms like GitHub, and implement strong safety measures.