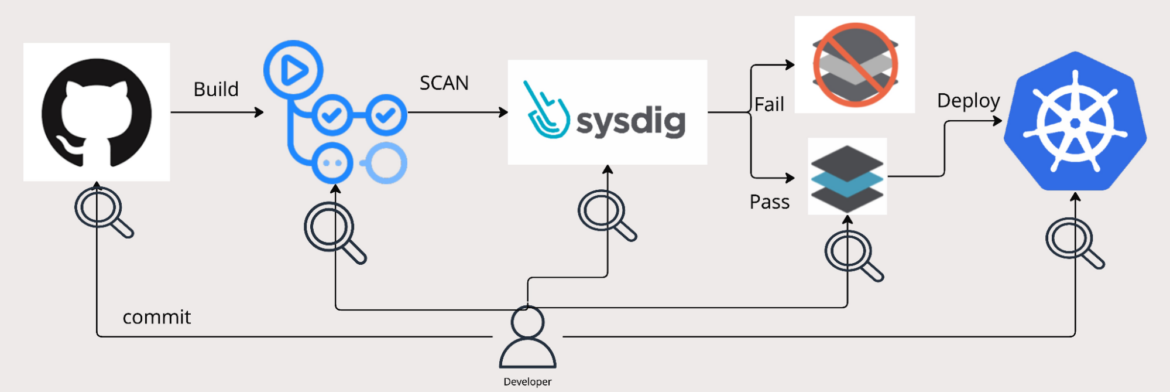
Builders are steadily tasked with working with a number of instruments within the cloud-native period. Every of those instruments performs an important function within the software life cycle, from improvement to deployment and operations. Nonetheless, the sheer selection and variety of those instruments can improve the chance of errors or the unintended inclusion of essential vulnerabilities and misconfigurations.
To deal with this downside Backstage offered a complete developer portal that gives an built-in perspective on all software program sources, documentation, and instruments. It’s a one-stop-shop that helps builders handle, monitor, and doc your entire software program improvement lifecycle (SDLC). In 2023, the Cloud Native Computing Basis (CNCF) declared Backstage because the third most quickly increasing challenge of the 12 months.
Backstage as its personal, already stands out as a strong useful resource for builders and DevOps groups. Nonetheless, its utility is enormously enhanced when built-in with Sysdig, which layers further real-time insights into lively vulnerabilities, misconfigurations, and runtime behaviors.
By embedding Sysdig’s safety insights straight inside Backstage, builders acquire rapid visibility into safety considerations, considerably accelerating the time to detect and reply to points. This integration aligns with the cloud-native ethos of agility and effectivity, bringing essential safety data to the forefront of the event course of.
As we delve deeper into the advantages and workings of the Sysdig-Backstage integration, we’ll discover:
- How the combination accelerates situation detection by consolidating all related data in a single place.
- How runtime insights can help builders in prioritizing susceptible packages which might be presently in use.
- How builders can acquire complete visibility into the whole software program improvement lifecycle (SDLC) utilizing runtime insights.
- How this integration streamlines the method of vulnerability administration, facilitating collaboration between builders and safety groups.
- How the combination empowers builders to take proactive accountability for software safety, minimizing the necessity for safety operations (SecOps) groups to intervene in figuring out and speaking vulnerabilities for remediation.
Let’s get began!
Backstage and Sysdig: Pillars of Trendy Growth
Backstage has emerged as a developer portal, providing a one-stop-shop for builders to entry instruments, companies, and knowledge essential to their every day duties. It was created at Spotify, after which donated to the CNCF.
Earlier than Backstage, builders have been pressured to make use of many various instruments from code repositories, steady integration and supply (CI/CD) pipelines, monitoring and observability platforms, to safety scanning and compliance instruments.
The sheer quantity and number of these instruments complicate the event panorama and result in advanced, steadily handbook processes. This complexity heightens the chance of errors or oversights, considerably growing the probabilities that vulnerabilities or misconfigurations may inadvertently make their approach into manufacturing.
Backstage introduces a single-pane-of-glass that aggregates data and controls from numerous instruments. Nonetheless, the deep safety facet at construct, deploy, and runtime is important to boost its energy.
Sysdig’s Cloud Native Software Safety Platform (CNAPP) is designed to scale back the time it takes to detect and examine dangers, and reply to incidents. By integrating Sysdig with Backstage, builders can acquire entry to Sysdig’s insights on vulnerabilities, misconfigurations, and runtime behaviors straight inside their main workspace. This makes it simpler for builders to establish and deal with potential points of their functions earlier within the devops cycle.
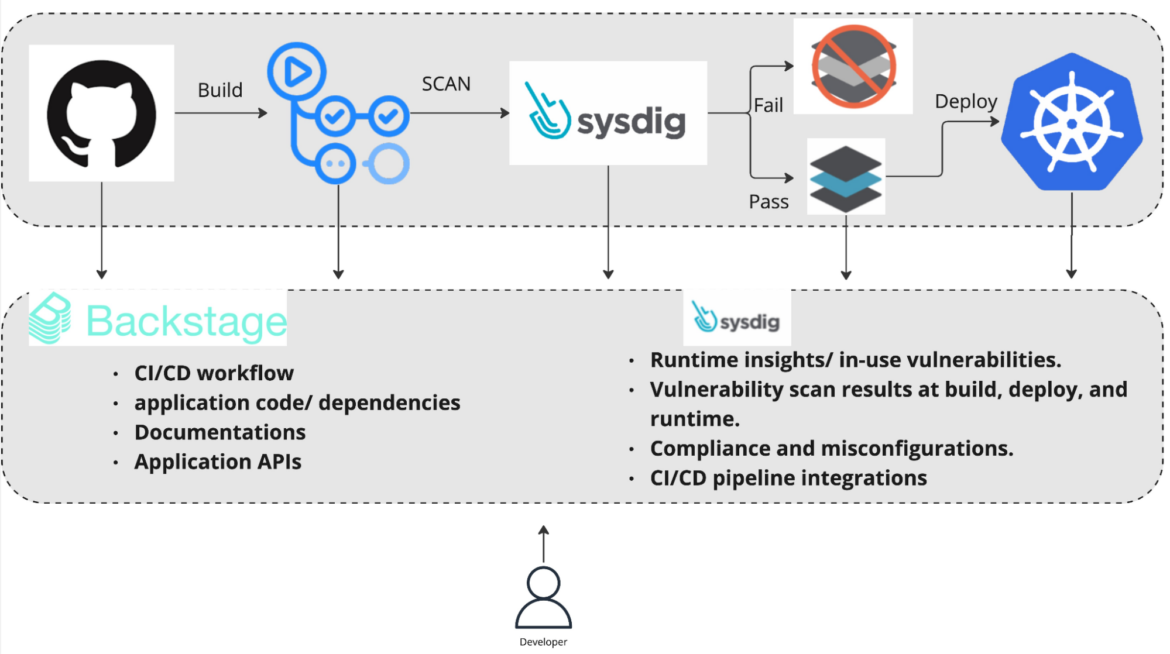
The combination of Sysdig with Backstage considerably enhances this ecosystem by bringing visibility into software habits, safety vulnerabilities, and potential misconfigurations on to the forefront of the developer workspace. Enriching Backstage with Sysdig’s run-time insights improves developer effectivity by permitting them to establish and remediate the very best precedence points whereas avoiding the necessity for a number of instruments, logins, and context adjustments which reduces the probabilities of errors or vulnerabilities being missed.
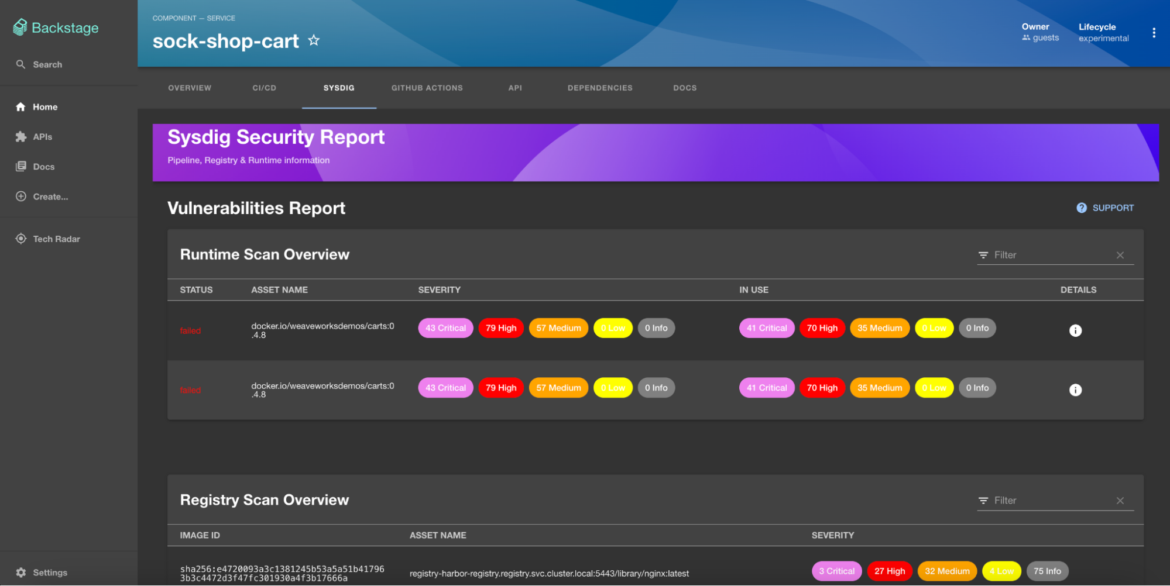
Integrating Sysdig with Backstage
Sysdig launched an official plugin for backstage. The plugin interacts with the Backstage backend and frontend by means of APIs which leverages annotations within the ‘catalog-info.yaml’ information of elements.
APIs: Sysdig plugin extends Backstage’s backend by way of APIs to carry out numerous operations, corresponding to fetching vulnerability scan outcomes from sysdig backend.
Annotation: Annotations are a key idea within the Backstage Catalog, used to connect metadata to entities outlined in ‘catalog-info.yaml’ information, corresponding to hyperlinks to documentation, system dependencies, and integration factors with instruments like Jenkins for CI/CD, or Sysdig for safety insights.
To put in the Sysdig plugin, please comply with the steps on this GitHub web page.
Instance Workflow
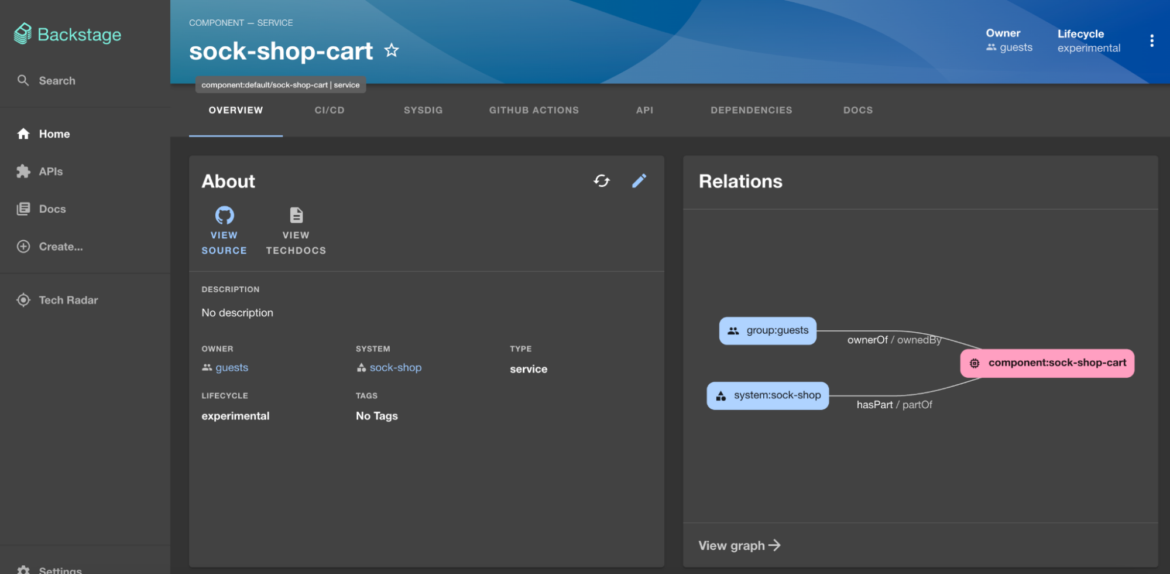
A service is registered within the Backstage Catalog with a catalog-info.yaml file, which incorporates annotations linking to its supply code repository and different integrations.
Including service to backstage
Right here is an instance of a ‘catalog-info.yaml’ for a service referred to as “sock-shop-cart”. It’s linked to the supply code on GitHub repository utilizing annotation “github.com/project-slug”.
apiVersion: backstage.io/v1alpha1
form: Element
metadata:
title: sock-shop-cart
annotations:
github.com/project-slug: JosephYostos/secure-inline-scan-examples
spec:
kind: service
lifecycle: experimental
system: sock-shop
proprietor: visitorsCode language: Perl (perl)As soon as the service is added to the catalog, the sock-shop-cart might be managed from Backstage.
Scanning Pictures with GitHub Actions and Sysdig
Sysdig and Backstage additionally combine with Github Actions. Each time a commit adjustments to the code, a pipeline motion might be triggered. And the picture will then be scanned for vulnerabilities and misconfigurations by Sysdig to make sure its safety earlier than being pushed to the registry or rejected if it doesn’t move the predefined safety coverage. You’ll be able to learn extra about Sysdig and GitHub Actions integration right here.
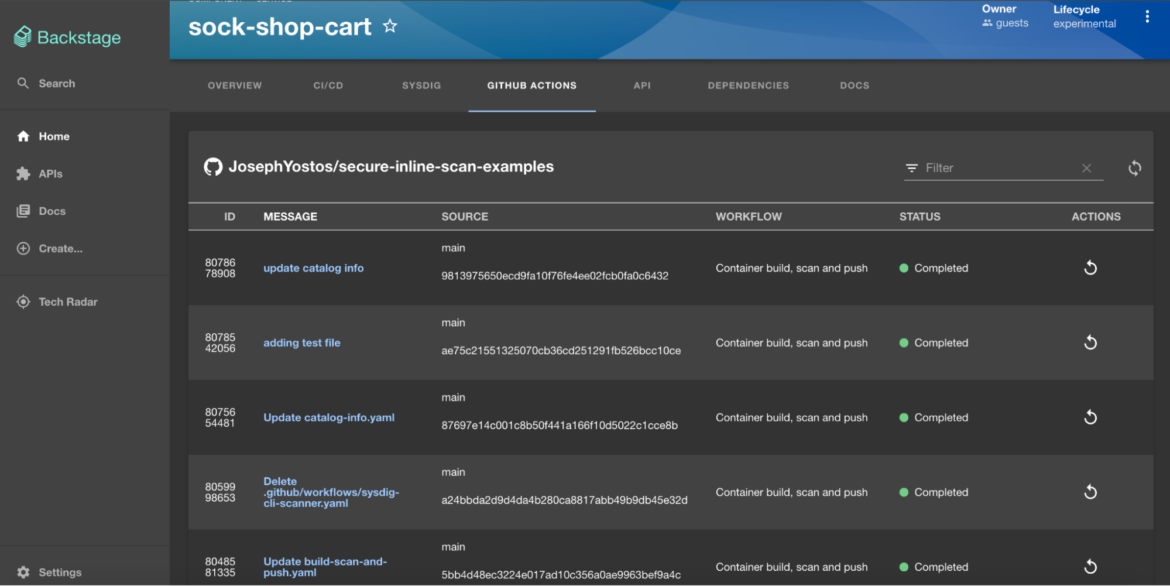
Pipeline scan
Now, after the adjustments have been dedicated and the pipeline workflow outcomes verified, the scanning outcomes have to be checked. To facilitate this, the next annotation is added to the service.
sysdigcloud.com/image-freetext: docker.io/josephyostos/testactionsCode language: Perl (perl)“sysdigcloud.com/image-freetext” is a free textual content question that can be utilized to seek for something within the pipeline scan outcomes. Within the given instance, the registry and picture title are outlined to acquire the picture scan outcomes for vulnerabilities and misconfigurations that has been performed through the picture construct time.
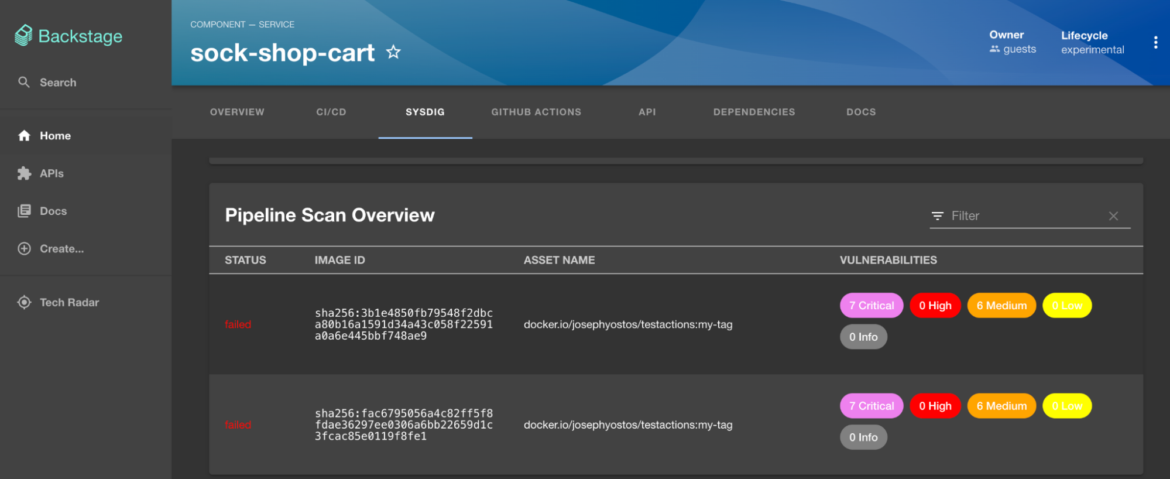
Runtime Insights
As builders now grow to be chargeable for the total software lifecycle, it turned crucial to pay attention to vulnerabilities at runtime and likewise what susceptible packages are in-use. For this objective, the next annotation can be utilized to fetch the runtime scan outcomes of the sock-shop-cart software.
sysdigcloud.com/kubernetes-namespace-name: sock-shop
sysdigcloud.com/kubernetes-workload-name: sock-shop-carts
sysdigcloud.com/kubernetes-workload-type: deploymentCode language: Perl (perl)In-use data helps builders prioritize fixes for packages which might be truly loaded in reminiscence and pose a excessive threat.

Safe extra
Sysdig gives curated annotations permitting builders detailed views into the potential dangers related to their present construct. For instance, along with what we’ve talked about, software house owners can fetch registry scanning outcomes, compliance studies, and extra.
All of the obtainable annotations from Sysdig can be found on this supply file
Right here is an instance of how the ‘catalog-info.yaml’ will appear like on the finish.
apiVersion: backstage.io/v1alpha1
form: Element
metadata:
title: sock-shop-cart
annotations:
github.com/project-slug: JosephYostos/secure-inline-scan-examples
sysdigcloud.com/image-freetext: docker.io/josephyostos/testactions
sysdigcloud.com/kubernetes-namespace-name: sock-shop
sysdigcloud.com/kubernetes-workload-name: sock-shop-carts
sysdigcloud.com/kubernetes-workload-type: deployment
sysdigcloud.com/registry-vendor: harbor
sysdigcloud.com/registry-name: registry-harbor-registry.registry.svc.cluster.native:5443
sysdigcloud.com/resource-name: sock-shop-carts
spec:
kind: service
lifecycle: experimental
system: sock-shop
proprietor: visitorsCode language: Perl (perl)Conclusion
The combination of Sysdig with Backstage marks a pivotal development within the cloud-native improvement panorama. With this integration, software program builders now have a centralized hub to handle, observe, and defend their functions. By making important safety data readily accessible, it empowers builders to proactively handle software safety, lowering the dependency on Safety Operations groups to establish and relay vulnerabilities for decision.
Consequently, this integration not solely enhances developer effectivity but in addition accelerates the identification and mitigation of potential points, reinforcing a tradition of safety and agility in cloud-native software improvement.