A brand new Google Adverts malvertising marketing campaign, coinciding with the launch of the Arc internet browser for Home windows, was tricking folks into downloading trojanized installers that infect them with malware payloads.
The Arc browser is a brand new internet browser that includes an modern consumer interface design that units it aside from conventional browsers.
Launched in July 2023 for macOS and after receiving glowing critiques from tech publications and customers, its latest launch on Home windows was extremely anticipated.
Cybercriminals goal Arc for Home windows launch
In response to a report by Malwarebytes, cybercriminals ready for the product launch, establishing malicious commercials on Google Search to lure customers trying to obtain the brand new internet browser.
Google’s advert platform has a big downside that enables menace actors to take out advertisements displaying authentic URLs, which has been abused to focus on Amazon, Whales Market, WebEx, and Google’s personal video platform, YouTube.
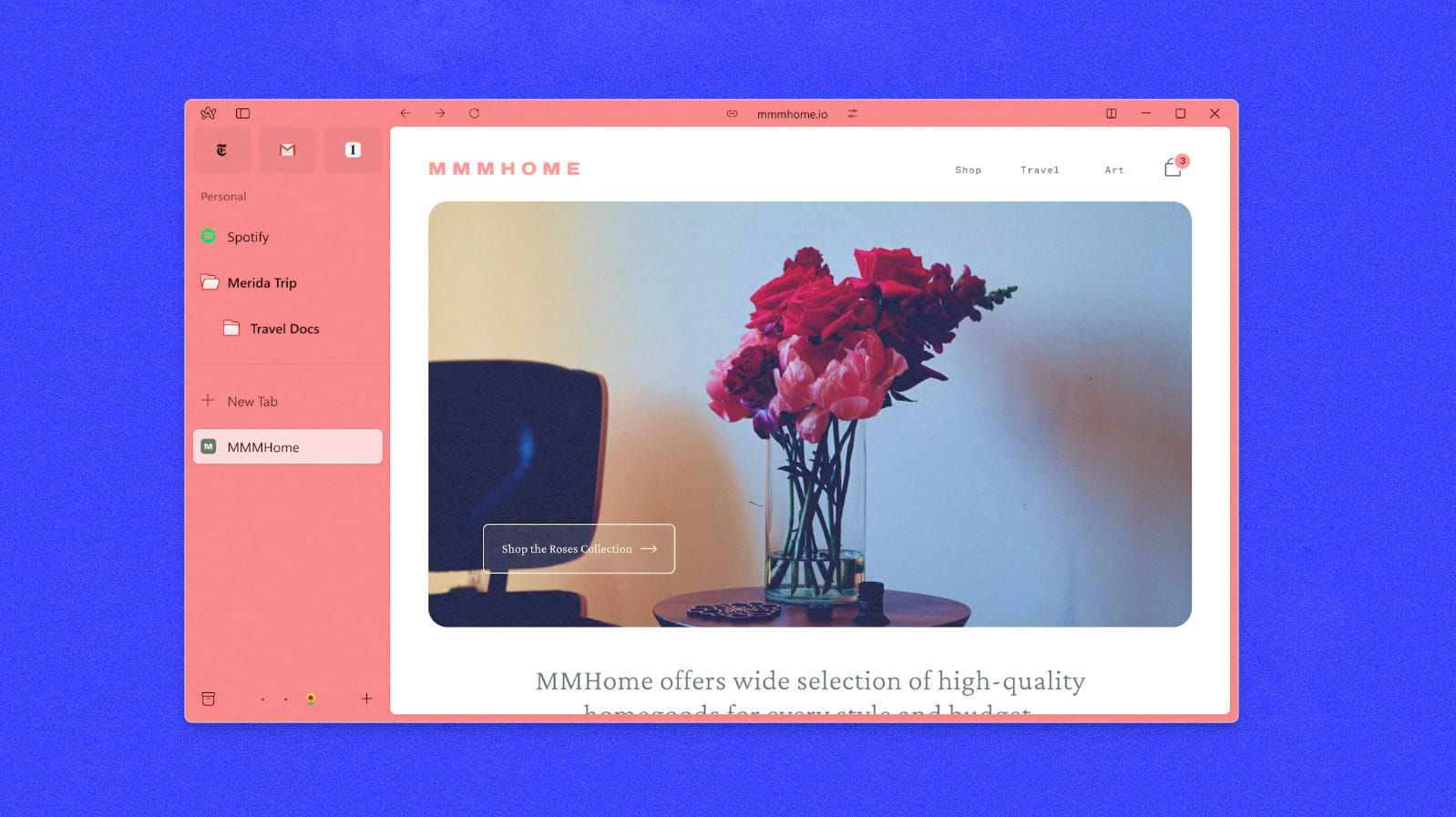
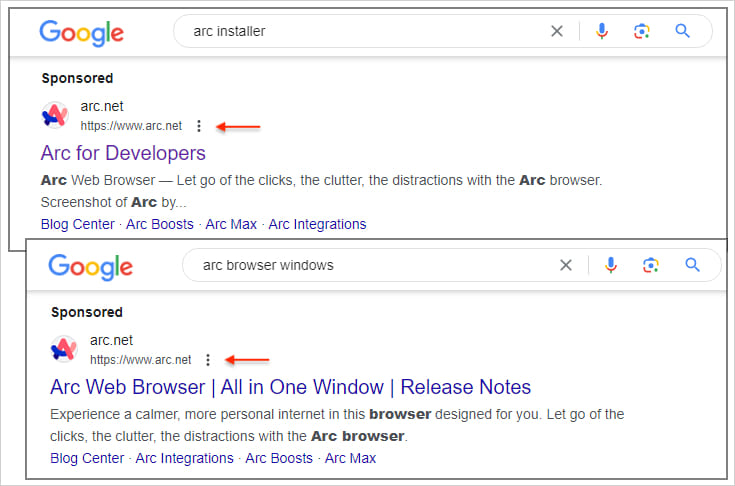
Malwarebytes discovered promoted outcomes for the search phrases “arc installer” and “arc browser windows” displaying the proper URL for Arc.
Supply: Malwarebytes
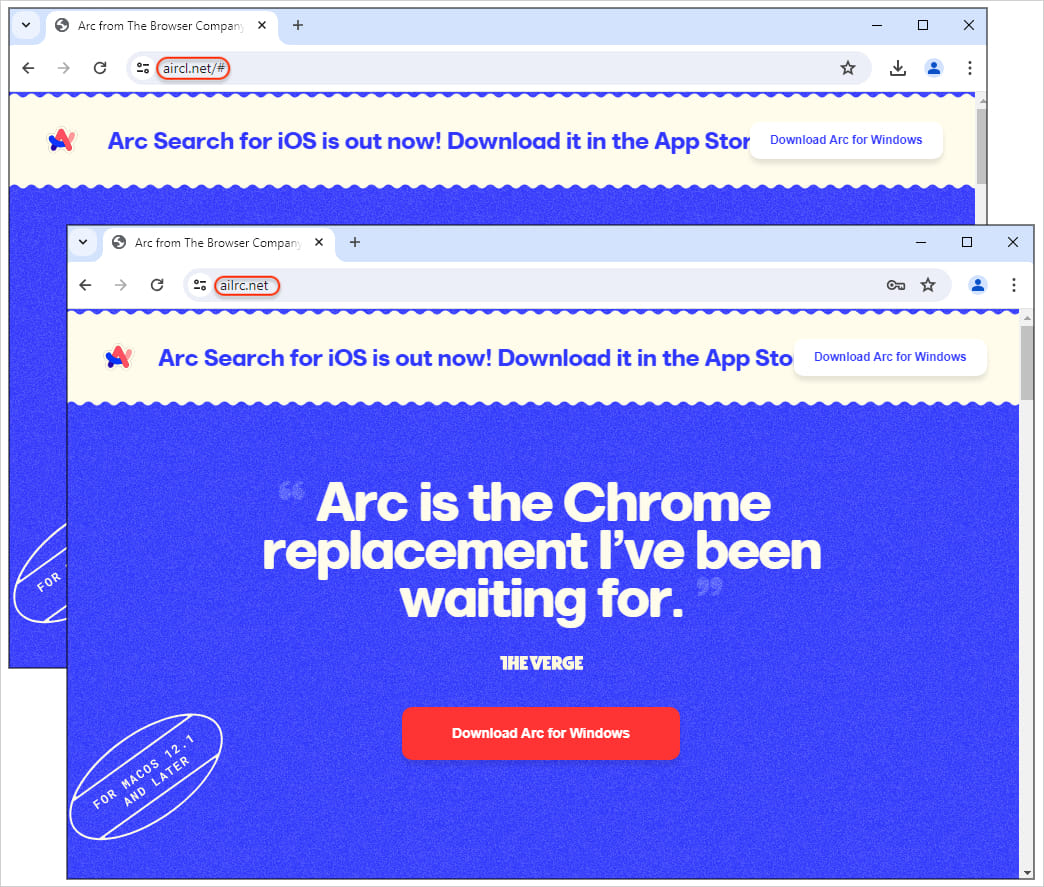
Nevertheless, after clicking the commercial, searchers are redirected to typo-squatted domains that visually resemble the real web site.
Supply: Malwarebytes
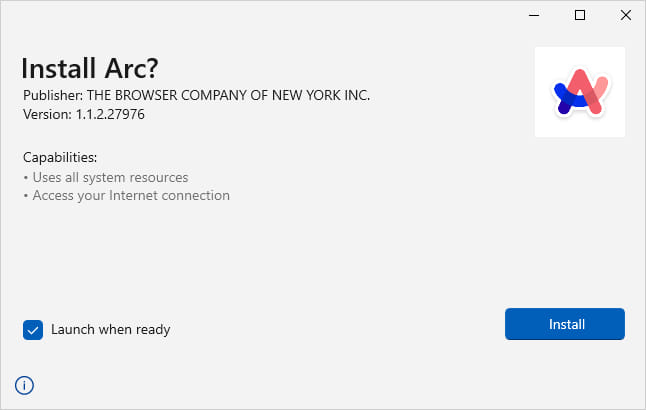
If the “Download” button is clicked, a trojanized installer file is retrieved from the MEGA internet hosting platform, which downloads an extra malicious payload named ‘bootstrap.exe’ from an exterior useful resource.
Supply: Malwarebytes
MEGA’s API is abused for command and management (C2) operations, sending and receiving operational directions and information.
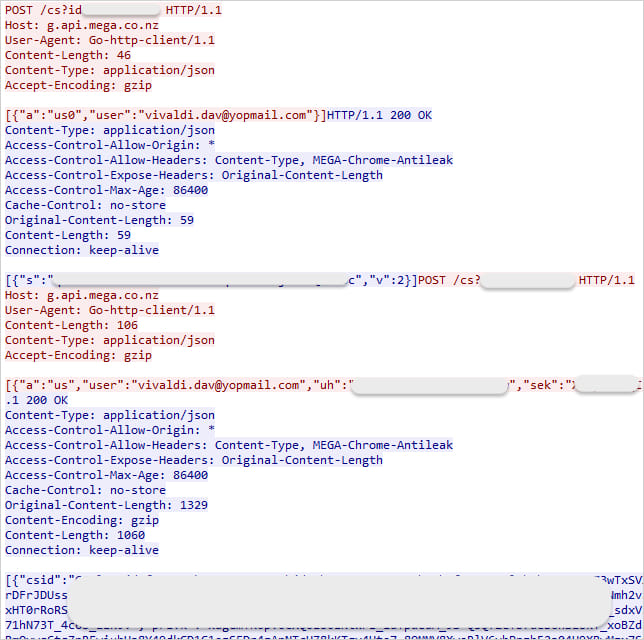
Supply: Malwarebytes
The installer file fetches a PNG file containing malicious code that compiles and drops the ultimate payload, ‘JRWeb.exe,’ onto the sufferer’s disk.
Malwarebytes additionally noticed a separate an infection chain that includes the installer utilizing a Python executable to inject code into msbuild.exe, which queries an exterior website to retrieve instructions for execution.
The analysts recommend that the ultimate payload in these assaults is an info-stealer, although this hasn’t been decided but.
As a result of Arc browser getting put in as anticipated on the sufferer’s machine and the malicious information working stealthily within the background, it is unlikely for the sufferer to understand they’ve now grow to be contaminated with malware.
Risk actors capitalizing on the hype surrounding new software program/sport launches is not new, however continues to be an efficient technique to distribute malware.
Customers trying to obtain software program ought to skip all promoted outcomes on Google Search, use advert blockers that conceal these outcomes, and bookmark official venture web sites for future use.
Moreover, all the time confirm the authenticity of the domains you are about to obtain installers from, and all the time scan downloaded information on an up-to-date AV instrument earlier than executing them.