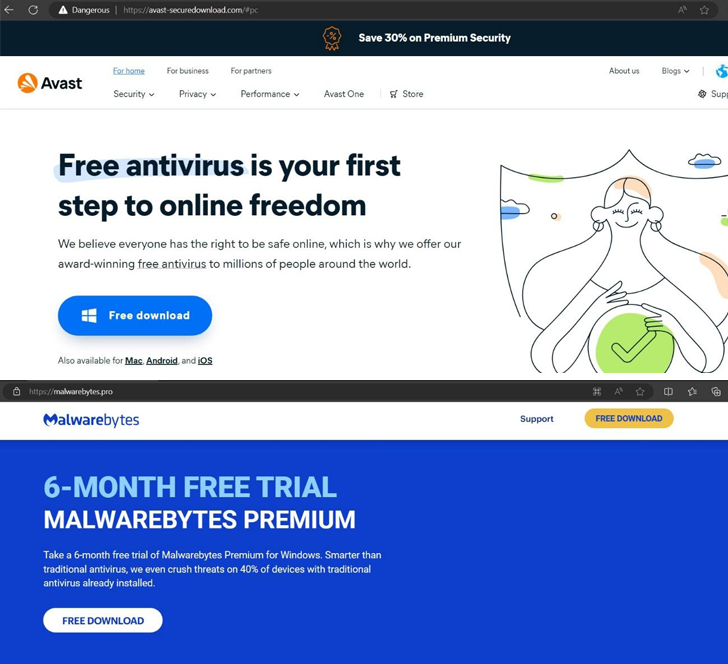
Risk actors have been noticed making use of pretend web sites masquerading as legit antivirus options from Avast, Bitdefender, and Malwarebytes to propagate malware able to stealing delicate info from Android and Home windows gadgets.
“Hosting malicious software through sites which look legitimate is predatory to general consumers, especially those who look to protect their devices from cyber attacks,” Trellix safety researcher Gurumoorthi Ramanathan mentioned.
The listing of internet sites is under –
- avast-securedownload[.]com, which is used to ship the SpyNote trojan within the type of an Android bundle file (“Avast.apk”) that, as soon as put in, requests for intrusive permissions to learn SMS messages and name logs, set up and delete apps, take screenshot, observe location, and even mine cryptocurrency
- bitdefender-app[.]com, which is used to ship a ZIP archive file (“setup-win-x86-x64.exe.zip”) that deploys the Lumma info stealer malware
- malwarebytes[.]professional, which is used to ship a RAR archive file (“MBSetup.rar”) that deploys the StealC info stealer malware
The cybersecurity agency mentioned it additionally uncovered a rogue Trellix binary named “AMCoreDat.exe” that serves as a conduit to drop a stealer malware able to harvesting sufferer info, together with browser information, and exfiltrating it to a distant server.
It is at the moment not clear how these bogus web sites are distributed, however comparable campaigns up to now have employed methods reminiscent of malvertising and search engine marketing (website positioning) poisoning.
Stealer malware have more and more turn out to be a typical menace, with cybercriminals promoting quite a few customized variants with various ranges of complexity. This consists of new stealers like Acrid, SamsStealer, ScarletStealer, and Waltuhium Grabber, in addition to updates to current ones reminiscent of SYS01stealer (aka Album Stealer or S1deload Stealer).
“The fact that new stealers appear every now and then, combined with the fact that their functionality and sophistication varies greatly, indicates that there is a criminal market demand for stealers,” Kaspersky mentioned in a latest report.
The event comes as researchers have found a brand new Android banking trojan referred to as Antidot that disguises itself as a Google Play replace to facilitate info theft by abusing Android’s accessibility and MediaProjection APIs.
“Functionality-wise Antidot is capable of keylogging, overlay attacks, SMS exfiltration, screen captures, credentials theft, device control, and execution of commands received from the attackers,” Broadcom-owned Symantec mentioned in a bulletin.