The investigation, which concerned analyzing a number of victims, primarily army and authorities targets, revealed a stealthy operation involving numerous generations of customized malware and phishing ways.
A current investigation by Bitdefender Labs has uncovered the actions of a beforehand unknown cyber menace group, dubbed “Unfading Sea Haze.” This group has been actively focusing on high-level organizations, notably army and authorities entities, in nations surrounding the South China Sea. The scope and nature of their assaults recommend a possible alignment with Chinese language pursuits within the area.
It’s value noting that the South China Sea nations sometimes seek advice from nations that border the South China Sea. These embody China, Taiwan, the Philippines, Malaysia, Brunei, Indonesia, and Vietnam.
A Journey By way of Time: Unraveling the Previous Actions
The investigation spanned at the least eight victims and traced the group’s actions again to 2018, revealing a fancy digital archaeology. Unfading Sea Haze has repeatedly gained entry to compromised programs, exploiting poor credential hygiene and insufficient patching practices. Their means to stay invisible for over 5 years signifies a complicated and affected person menace actor, probably backed by nation-state assets.
Attribution: Clues Pointing to Chinese language Cyber Ecosystem
Whereas a definitive attribution stays difficult, Bitdefender’s analysis offers suggestive clues. The group’s give attention to South China Sea nations and the usage of instruments fashionable with Chinese language actors, corresponding to Gh0st RAT variants, trace at a connection to the Chinese language cyber ecosystem.
Moreover, a selected approach resembling a characteristic discovered within the “funnyswitch” backdoor, linked to APT41, additional strengthens this speculation.
Anatomy of an Assault: Preliminary Compromise and Techniques
Unfading Sea Haze’s ways embody spear-phishing emails with malicious archives, containing LNK recordsdata disguised as common paperwork. These recordsdata execute malicious instructions, offering the group with entry to sufferer programs. They’ve additionally included Distant Monitoring and Administration (RMM) instruments, corresponding to ITarian RMM, into their arsenal, a deviation from typical nation-state actor ways.
Execution: A Refined Malware Arsenal
Unfading Sea Haze has developed a complicated and evolving malware arsenal. Initially, they relied on SilentGh0st, TranslucentGh0st, and SharpJSHandler, supported by Ps2dllLoader.
Nevertheless, in 2023, they started deploying new parts, corresponding to msbuild.exe and C# payloads saved on distant SMB shares. They’ve additionally adopted modular and plugin-based variants, like FluffyGh0st, InsidiousGh0st, and EtherealGh0st, for improved evasion capabilities.
Knowledge Assortment: Customized Instruments and Handbook Strategies
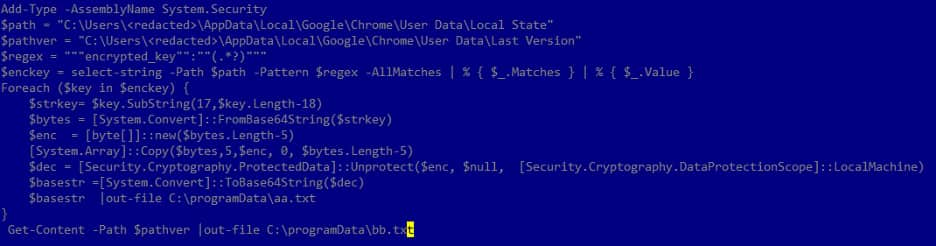
The group’s major goal seems to be espionage, as evidenced by their use of customized and off-the-shelf instruments for knowledge assortment. They make use of a customized keylogger, xkeylog, and a browser knowledge stealer to seize delicate info.
Moreover, they use handbook methods, corresponding to archiving knowledge with rar.exe and focusing on messaging app knowledge, demonstrating a focused and versatile strategy to knowledge extraction.
Unfading Sea Haze initially used a customized instrument, DustyExfilTool, for knowledge exfiltration. Nevertheless, they switched to the curl utility and FTP protocol in 2022. Their exfiltration ways have advanced, with dynamic and randomly generated credentials, indicating a give attention to enhancing operational safety.
Conclusion and Suggestions: A Layered Protection Technique
Unfading Sea Haze has showcased a complicated and versatile strategy to cyberattacks. To mitigate the dangers posed by this group and comparable menace actors, organizations ought to undertake a multilayered protection technique.
This contains sturdy vulnerability administration, robust authentication, correct community segmentation, efficient logging, and collaboration throughout the cybersecurity neighborhood. By staying vigilant and proactive, organizations can improve their resilience towards such subtle cyber threats.
For a complete understanding of Unfading Sea Haze’s ways and malware arsenal, seek advice from the full analysis paper (PDF) by Bitdefender Labs.
RELATED TOPICS
- China-Linked Spy ware Present in Play Retailer Apps, 2m Downloads
- China’s insidious surveillance towards Uyghurs with Android malware
- Muddling Meerkat Suspected of Espionage through Nice Firewall of China
- Chinese language Blackwood APT Deploys NSPX30 Backdoor in Cyberespionage
- Cyberattacks Surge 325% in Philippines Amid South China Sea Standoff