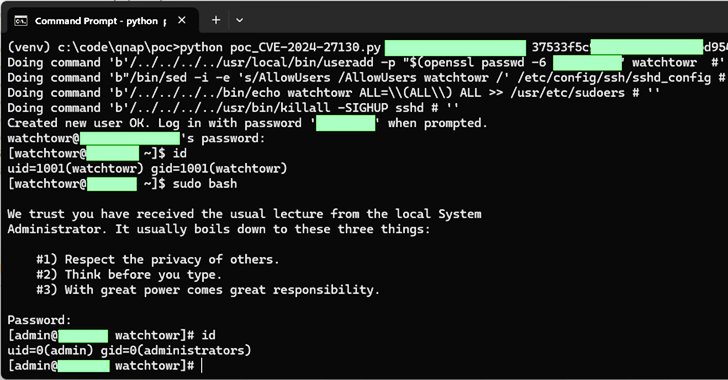
Taiwanese firm QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, a few of which may very well be exploited to realize code execution on its network-attached storage (NAS) home equipment.
The points, which influence QTS 5.1.x and QuTS hero h5.1.x, are listed beneath –
- CVE-2024-21902 – An incorrect permission task for crucial useful resource vulnerability that might enable authenticated customers to learn or modify the useful resource by way of a community
- CVE-2024-27127 – A double free vulnerability that might enable authenticated customers to execute arbitrary code by way of a community
- CVE-2024-27128, CVE-2024-27129, and CVE-2024-27130 – A set of buffer overflow vulnerabilities that might enable authenticated customers to execute arbitrary code by way of a community
All of the shortcomings, that require a sound account on NAS gadgets, have been addressed in QTS 5.1.7.2770 construct 20240520 and QuTS hero h5.1.7.2770 construct 20240520. Aliz Hammond of watchTowr Labs has been credited with discovering and reporting the failings on January 3, 2024.
“The CVE-2024-27130 vulnerability, which has been reported under WatchTowr ID WT-2023-0054, is caused by the unsafe use of the ‘strcpy’ function in the No_Support_ACL function, which is utilized by the get_file_size request in the share.cgi script,” QNAP mentioned.
“This script is used when sharing media with external users. To exploit this vulnerability, an attacker requires a valid ‘ssid’ parameter, which is generated when a NAS user shares a file from their QNAP device.”
It additionally identified that each one QTS 4.x and 5.x variations have Handle House Format Randomization (ASLR) enabled, making it troublesome for an attacker to use the vulnerability.
The patches arrived 4 days after the Singapore-based cybersecurity firm launched particulars a couple of whole of 15 vulnerabilities, together with 4 separate bugs that may very well be weaponized to bypass authentication and execute arbitrary code.
The vulnerabilities – tracked from CVE-2023-50361 by means of CVE-2023-50364 – had been resolved by QNAP on April 25, 2024, following disclosure in December 2023.
It is price noting that the corporate has but to launch fixes for CVE-2024-27131, which has been described by watchTowr as a case of “Log spoofing via x-forwarded-for [that] allows users to cause downloads to be recorded as requested from arbitrary source location.”
QNAP mentioned CVE-2024-27131 just isn’t an precise vulnerability however slightly a design alternative that requires a change within the UI specs throughout the QuLog Heart. That is anticipated to be remediated in QTS 5.2.0.
Particulars about 4 different vulnerabilities reported by watchTowr are at the moment withheld, with three of them at the moment beneath evaluation. The fourth problem has been assigned a CVE ID and will likely be mounted within the upcoming launch.
watchTowr mentioned it was compelled to go public with the failings final week after QNAP failed to deal with them throughout the stipulated 90-day public disclosure interval and that it was beneficiant by giving the corporate “multiple extensions” to present the corporate sufficient time.
In response, QNAP mentioned it regretted the coordination points, stating it is committing to releasing fixes for high- or critical-severity flaws inside 45 days. Fixes for medium-severity vulnerabilities will likely be launched inside 90 days.
“We apologize for any inconvenience this may have caused and are committed to enhancing our security measures continuously,” it added. “Our goal is to work closely with researchers worldwide to ensure the highest quality of security for our products.”
With vulnerabilities in QNAP NAS gadgets exploited up to now by ransomware attackers, customers are really useful to the most recent variations of QTS and QuTS hero as quickly as potential to mitigate potential threats.