Menace actors had been discovered breaching AWS accounts utilizing authentication secrets and techniques leaked as plaintext in Atlassian Bitbucket artifact objects.
The difficulty was found by Mandiant, who was investigating a current publicity of Amazon Internet Companies (AWS) secrets and techniques that risk actors used to achieve entry to AWS.
Though the problem was found within the context of an investigation, it illustrates how knowledge beforehand considered secured, can be leaked in plaintext to public repositories.
BitBucket’s secured variables
Bitbucket is a Git-compatible web-based model management repository and internet hosting service run by Atlassian, providing builders a code administration and collaboration platform.
Bitbucket Pipelines is an built-in steady supply/deployment (CI/CD) service that automates the construct, take a look at, and deployment processes.
System admins typically hyperlink Pipelines on to AWS for speedy deployment of apps and to entry sources utilizing AWS CLI, SDKs, and different AWS instruments.
To facilitate this automation, Bitbucket permits builders to retailer delicate data, similar to AWS authentication secrets and techniques, in ‘Secured Variables’ to simply use these variables of their code with out exposing the keys to different individuals.
.png)
Supply: Mandiant
When a variable is about as secured in BitBucket, they are saved in encrypted type to forestall public publicity of its values within the Bitbucket atmosphere.
“You can secure a variable, which means it can be used in your scripts but its value will be hidden in the build logs (see example below),” explains the Bitbucket documentation.
“If you want to edit a secure variable, you can only give it a new value or delete it. Secure variables are stored as encrypted values.”
Nevertheless, Mandiant found that artifact objects generated throughout pipeline runs can comprise delicate data, together with secured variables in plaintext. As builders might not bear in mind that these secrets and techniques are uncovered in artifact information, the supply code could also be revealed to public repositories the place risk actors can steal them.
Secrets and techniques in plaintext
Artifacts are outlined within the bitbucket-pipelines.yml config file used to specify a Bitbucket undertaking’s CI/CD processes.
One of many directives in these information is artifacts:, which are used to specify variables, information, and directories which can be exported to artifact objects to be retained and utilized in additional steps of the construct and testing course of.
Mandiant says that it is not uncommon for builders to make use of the printenv command to retailer all atmosphere information in a textual content file, which is then handed to an artifact object for future steps within the construct course of.

Supply: Mandiant
Nevertheless, doing so will trigger “secured variables” to be exported in plaintext to the artifact file reasonably than in its encrypted type.
If these artifact information are then saved in a public location, a risk actor can merely open the textual content file and consider all variables in plaintext, simply stealing authentication secrets and techniques that can be utilized to steal knowledge or carry out different malicious exercise.
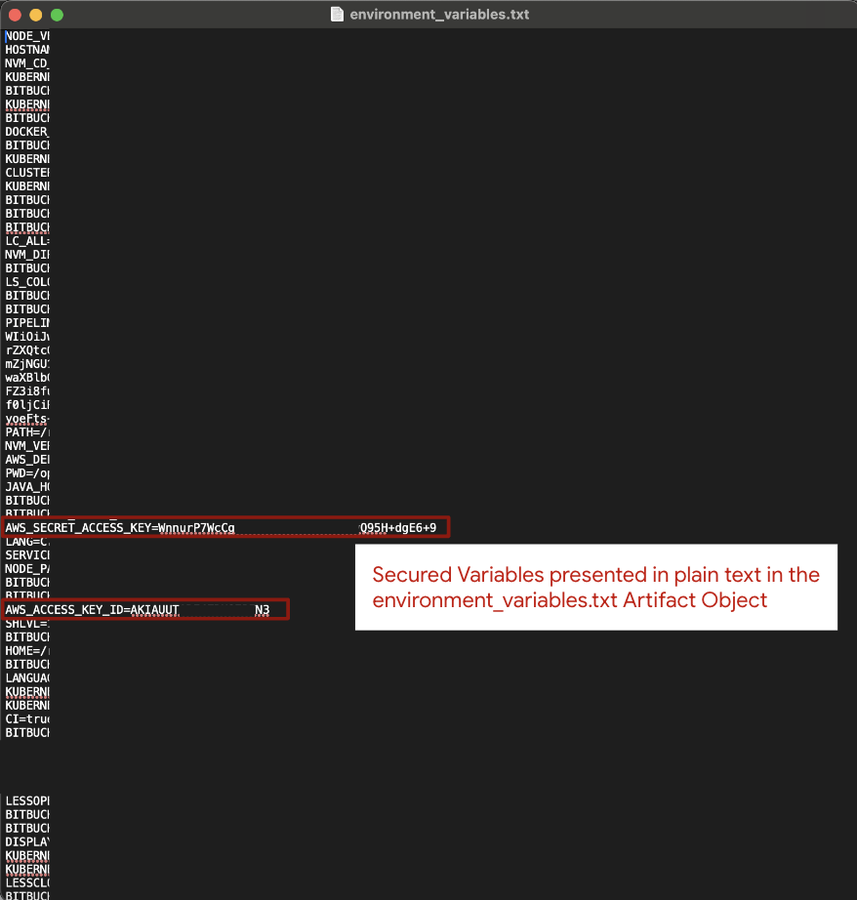
Supply: Mandiant
“Mandiant has seen instances in which development teams used Bitbucket artifacts in web application source code for troubleshooting purposes, but, unbeknownst to the development teams, those artifacts contained plain text values of secret keys,” reads the report.
“This resulted in secret keys being exposed to the public internet where they were located and subsequently leveraged by attackers to gain unauthorized access.”
One other risk in keeping with Mandiant is misconfiguring the ‘bitbucket-pipelines.yml’ file which defines the CI/CD pipeline, to incorporate secured variables in logs or artifacts.
When pipeline scripts log atmosphere variables for debugging functions, they’ll unintentionally log delicate data, and since these logs are sometimes saved in accessible areas, there’s once more a threat of secret publicity.
Mitigation suggestions
Mandiant reminds builders that Bitbucket was not designed to handle secrets and techniques, suggesting {that a} devoted, specialised product is used for that objective as a substitute.
Builders are additionally really helpful to fastidiously overview artifacts to make sure no plain textual content secrets and techniques are contained contained in the generated information.
Lastly, it’s advisable to deploy code scanning over the entire pipeline lifecycle to catch secret publicity occasions and take away them previous to the code reaching manufacturing.
