In an period the place cloud assaults and threats are occurring very quick and always evolving, the European Union (EU) has stepped up its cybersecurity sport with two new laws: the Digital Operational Resilience Act (DORA) and the revised Directive on Safety of Community and Info Methods (NIS2). With extra strict necessities on compliance controls and breach disclosures, these laws are set to rework how companies handle their cyber dangers in Europe. If you happen to’re feeling overwhelmed by these modifications, you’re not alone. That’s the place Sysdig is available in. As the primary CNAPP to supply out-of-box insurance policies for DORA and NIS2 compliance, we’re right here to information you thru these new necessities, making certain your online business isn’t simply compliant, but in addition safer.
Overview of DORA and NIS2
Prior to now, most laws had been checked periodically for compliance – possibly month-to-month, quarterly, or as much as yearly. Nonetheless, to handle the continued surge of cyberattacks and the velocity at which they transfer, these new laws want to implement stricter controls and, extra importantly, very aggressive necessities round time to disclosure to regulatory authorities within the case of a safety occasion, privateness occasion, or breach. Within the case of DORA, you solely have 4 hours from the second of classification of the incident as main to reveal. With NIS2, you’ve 24 hours.
Digital Operational Resilience Act (DORA) is an implementing act launched by the European Union to handle and improve the safety and resilience of digital operations throughout the monetary sector. It goals to consolidate and standardize the digital operational resilience practices throughout monetary entities, making certain that they’ll face up to, reply to, and recuperate from all sorts of ICT (Info and Communication Know-how) associated disruptions and threats. The Regulation will apply from Jan. 17, 2025, which implies monetary firms have lower than a 12 months to grow to be compliant with DORA.
DORA applies to the overwhelming majority of the monetary companies sector. This contains, however is just not restricted to:
- Banks and credit score establishments
- Funding companies
- Insurance coverage firms
- Asset managers
- Cost service suppliers
- Crypto-asset service suppliers
Moreover, DORA extends its attain to third-party ICT service suppliers, together with cloud companies, that are integral to the operations of economic entities. That is vital because it marks the primary time monetary companies supervisors are given authority to supervise these third-party distributors straight. Because it pertains to cloud, DORA additionally specifies that monetary entities ought to use multi-cloud approaches to enhance resiliency. Multi-cloud methods can not directly create different safety gaps as a result of different expertise. This strategy necessitates that applicable unified controls and monitoring are applied to make sure these safety gaps aren’t exploitable.
Community and Info Methods Directive (NIS2)
Not like laws, that are straight relevant, NIS2 is an EU directive that units normal aims for Member States’ nationwide legal guidelines on cybersecurity and ICT methods and networks, with the goal of strengthening safety throughout the EU.
The principle objective of NIS2 is to considerably increase the extent of cybersecurity throughout the EU by increasing the scope of the unique directive, introducing stricter safety necessities, and growing the accountability of entities inside important sectors.
NIS2 broadens the scope of cybersecurity obligations to incorporate a variety of sectors important to the EU’s financial system and society. It encompasses entities in vitality, transport, banking, monetary markets, healthcare, water provide, digital infrastructure, public administration, and house.
Sysdig’s Position in Facilitating NIS2 and DORA Compliance
Sysdig is the primary Cloud-Native Software Safety Platform (CNAPP) to supply out-of-box compliance insurance policies particularly designed to assist group’s fulfill the technical parts of the European Union’s new regulatory frameworks, DORA and NIS2, as they pertain to cloud sources.
Studying the specs of DORA and NIS2 could possibly be complicated – a greatest observe could be to disassemble this complicated stuff within the elementary constructing blocks. And that’s what we’re going to do within the following part.
DORA
Sysdig facilitates this by offering complete controls protecting numerous features of Linux, Kubernetes, cloud environments, and identification administration.
These are a few of the technical necessities that apply to cloud environments. We are going to clarify these necessities and take a look at some examples of safety controls from Sysdig that guarantee cloud property meet DORA compliance circumstances.
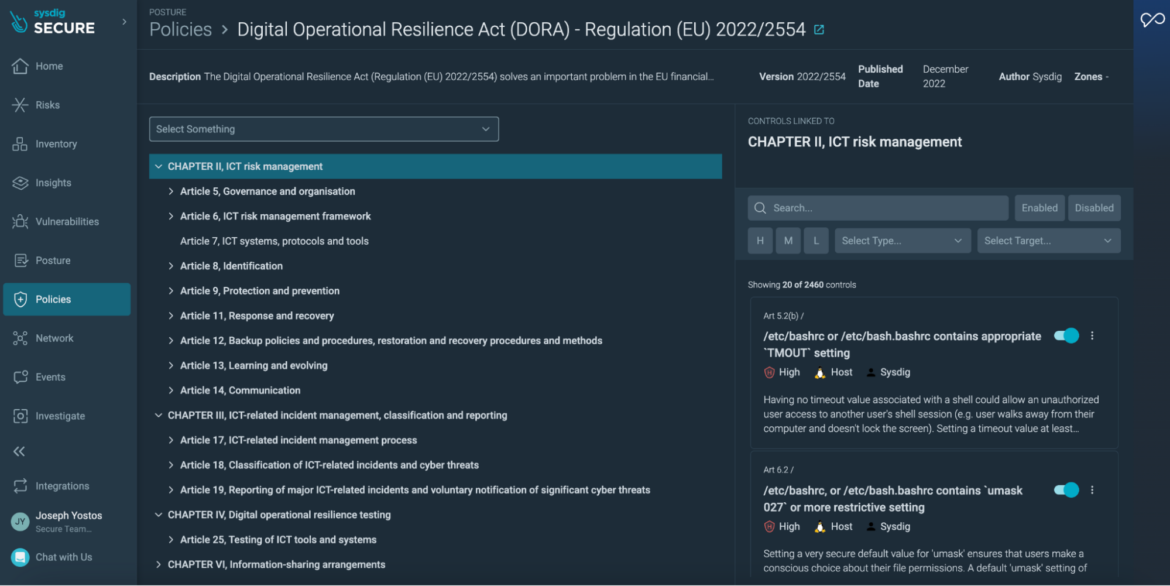
| CHAPTER II, ICT threat administration Article 5, Governance and group Monetary entities shall have in place an inside governance and management framework that ensures an efficient and prudent administration of ICT threat, in accordance with Article 6(4), with a view to obtain a excessive stage of digital operational resilience. The administration physique of the monetary entity shall outline, approve, oversee, and be liable for the implementation of all preparations associated to the ICT threat administration framework referred to in Article 6(1). |
Sysdig gives round 300 controls to make sure availability, authenticity, integrity, and confidentiality of knowledge underneath this text.
Listed here are some examples: API Server: IAM: Storage: Networking: Linux Safety: |
| CHAPTER II, ICT threat administration Article 6, ICT threat administration framework, Artwork 6.2 The ICT threat administration framework shall embrace at the least methods, insurance policies, procedures, ICT protocols, and instruments which are essential to duly and adequately shield all data property and ICT property. This may embrace pc software program, {hardware}, servers in addition to to guard all related bodily parts and infrastructures, reminiscent of premises, knowledge facilities and delicate designated areas. It’s going to additionally make sure that all data property and ICT property are adequately shielded from dangers together with harm and unauthorized entry or utilization. |
The ICT threat administration framework should embody complete methods, insurance policies, procedures, and instruments designed to safeguard all data and ICT property. This contains software program, {hardware}, servers, bodily parts, and extra.
Sysdig helps these necessities by 190 controls and a multi-layered safety strategy that features: Identification safety: Workload safety: |
| CHAPTER II, ICT threat administration Article 7, ICT methods, protocols, and instruments “In order to address and manage ICT risk, financial entities shall use and maintain updated ICT systems, protocols and tools that are: (a) appropriate to the magnitude of operations supporting the conduct of their activities, in accordance with the proportionality principle as referred to in Article 4; |
This part of DORA is all about using and retaining up-to-date ICT methods, protocols, and instruments which are scalable, dependable, resilient, and high-performance.
Sysdig aids monetary entities in assembly these necessities by offering: Workload safety: Kubernetes: Audit Log: |
| CHAPTER II, ICT threat administration Article 9, Safety and preventionArt 9.3 “In order to achieve the objectives referred to in paragraph 2, financial entities shall use ICT solutions and processes that are appropriate in accordance with Article 4. Those ICT solutions and processes shall: (a) ensure the security of the means of transfer of data; |
This Article emphasizes that monetary entities should make use of ICT options and processes that guarantee knowledge switch safety, reduce dangers reminiscent of knowledge corruption, unauthorized entry, and technical points, and stop knowledge availability, authenticity, integrity, confidentiality breaches, and knowledge loss. These measures should additionally shield knowledge from management-related dangers, together with administrative errors, processing hazards, and human errors.
Sysdig achieves this by way of controls like: API Server: Compute: Firewall Configuration: |
These are just a few examples of the technical necessities of DORA. Our complete coverage extends past these examples.
NIS2
NIS2 necessities are similar to DORA however with a distinct scope. NIS2 covers all important infrastructure firms. The scope of important infrastructure is huge, together with the anticipated healthcare suppliers, utilities, and telecom suppliers, but in addition digital service suppliers. Entities fall inside important or vital classes with totally different management necessities, monitoring provisions, and attestation ranges.
Sysdig covers the 14 technical necessities of NIS2, with 2,905 complete variety of controls.
A lot of the technical necessities are underneath Article 21, “Cybersecurity risk-management measures,” of Chapter IV, “Cybersecurity Risk-Management measures and reporting obligations.” Listed here are a few of the technical necessities.
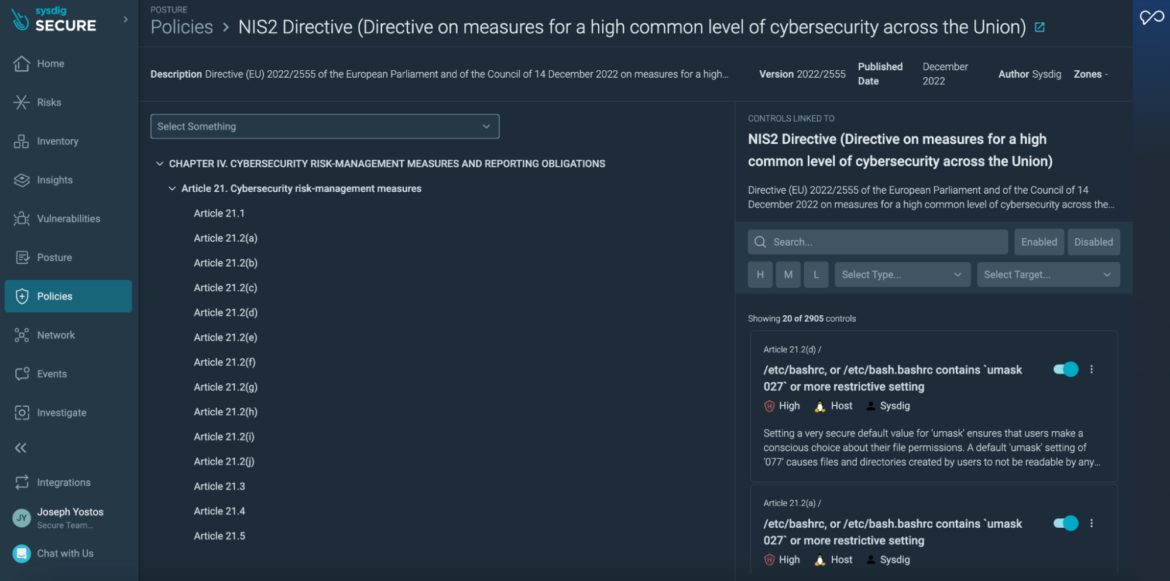
| “Member States shall ensure that essential and important entities take appropriate and proportionate technical, operational and organizational measures to manage the risks posed to the security of network and information systems which those entities use for their operations or for the provision of their services, and to prevent or minimize the impact of incidents on recipients of their services and on other services.
Taking into account the state-of-the-art and, where applicable, relevant European and international standards, as well as the cost of implementation, the measures referred to in the first subparagraph shall ensure a level of security of network and information systems appropriate to the risks posed. When assessing the proportionality of those measures, due account shall be taken of the degree of the entity’s exposure to risks, the entity’s size and the likelihood of occurrence of incidents and their severity, including their societal and economic impact.” |
NIS2 requires entities to undertake appropriate measures throughout technical, operational, and organizational domains to handle safety dangers for his or her community and data methods, aiming to cut back the affect of incidents. These measures ought to align with the newest requirements and be cost-effective, reflecting the entity’s threat publicity, measurement, and potential incident impacts.
Sysdig addresses this by over 200 controls, listed below are some examples: |
| Article 21.2(d)The measures referred to in paragraph 1 shall be based mostly on an all-hazards strategy that goals to guard community and data methods and the bodily atmosphere of these methods from incidents, and shall embrace at the least the next: provide chain safety, together with security-related features regarding the relationships between every entity and its direct suppliers or service suppliers. | key focus is on securing the provision chain, which includes addressing safety features within the relationships between entities and their direct suppliers or service suppliers.
Sysdig can facilitate compliance with this requirement by over 200 controls, and listed below are some examples: Safe SDLC: Logging: Entry management: Secret: |
These are just a few examples of the technical necessities of NIS2. Our complete coverage extends past these examples.
Conclusion
In conclusion, the NIS2 directive and DORA laws mark vital milestones within the European Union’s journey in direction of stronger cybersecurity and operational resilience, significantly inside important sectors and the monetary business. Set to return into impact in January 2025, these complete frameworks necessitate that affected entities — spanning a broad array of sectors — implement sturdy measures to guard their community and data methods towards a variety of cyber threats.
On this pivotal second, Sysdig stands out as the primary Cloud-Native Software Safety Platform (CNAPP) to supply out-of-the-box insurance policies to help in NIS2 and DORA compliance. This unparalleled readiness positions Sysdig not simply as a device, however as a strategic accomplice for companies in search of to navigate the approaching regulatory panorama confidently.
To be taught extra about compliance and laws in cloud-native environments, watch our panel dialog: Delivering Safe, Compliant Monetary Companies within the Cloud.