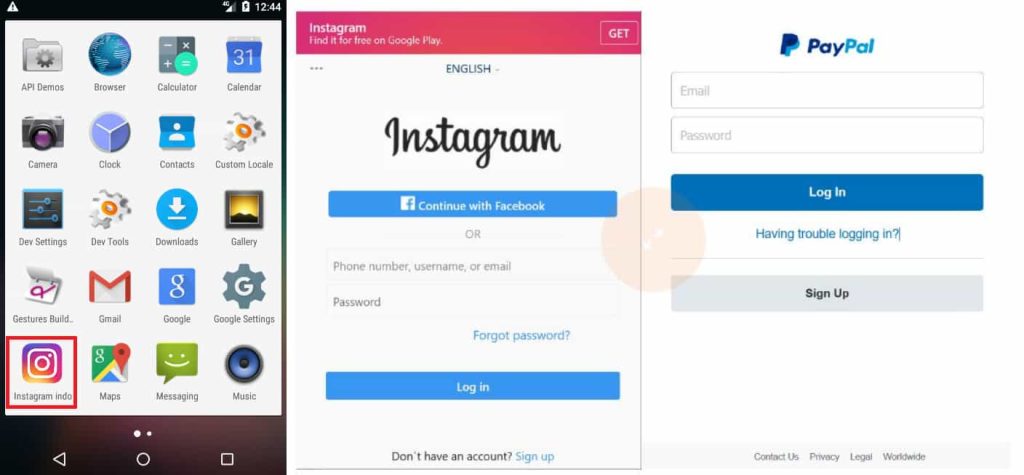
Think about opening your favourite social media app, solely to unknowingly hand over your login particulars to a sneaky hacker. That’s what is occurring with Android customers focused by a malicious new malware marketing campaign.
The SonicWall Seize Labs risk analysis group studies that risk actors are utilizing malicious Android apps to impersonate well-liked on-line companies like Google, Instagram, Snapchat, WhatsApp, and X. These apps goal to steal delicate knowledge from susceptible Android telephones, together with contacts, textual content messages, name logs, and passwords.
These apps look respectable because of utilizing acquainted logos and names to trick unsuspecting customers and conceal in plain sight. When opened, the app requests entry to 2 permissions: Android Accessibility Service and Machine Admin Permission. If the sufferer grants these permissions, the app can achieve full management of the system.
“By requesting these permissions, the malicious app aims to gain control over the victim’s device, potentially allowing it to carry out harmful actions or steal sensitive information without the user’s awareness or consent,” SonicWall’s weblog put up learn.
The malicious app then establishes a reference to a hacker-controlled C2 server, receiving further directions. It may learn messages, name logs, entry notification knowledge, ship messages, set up malware, and open malicious web sites for phishing functions.
Furthermore, the app redirects victims to faux login pages of well-liked companies like Fb, GitHub, Instagram, Netflix, PayPal, LinkedIn, Microsoft, X, WordPress, and Yahoo, and many others., prompting them to enter their username and password.
This data is shared with hackers, who can steal accounts, commit fraud, and even identification theft if delicate private data, together with driver’s license or Social Safety quantity, is saved on companies like OneDrive.
Researchers are, nevertheless, not sure about how these apps find yourself on the most effective Android telephones, however they think they’re distributed by phishing websites, emails, textual content messages, or bundled with pirated software program.
This growth follows safety corporations Symantec and Cyfirma’s latest warning of a social engineering marketing campaign utilizing WhatsApp to unfold a brand new Android malware, posing as a defence-related software.
To keep away from falling sufferer to misleading malware, keep vigilant and obtain apps from the official Google Play Retailer, guaranteeing they’re respectable and never from third-party shops or suspicious web sites. Be cautious of apps requesting extreme permissions, particularly these unrelated to the app’s core perform.
RELATED TOPICS
- New iOS Trojan “GoldPickaxe” Steals Facial Recognition Knowledge
- Pretend Skype, Zoom Apps Infecting Gadgets with A number of RATs
- Pretend Chrome Updates Unfold Android Brokewell Banking Malware
- SpyNote Android Spy ware Poses as Legit Crypto Wallets, Steals Funds
- Android Banking Malware FjordPhantom Steals Funds Through Virtualization