Within the final decade, there was a rising disconnect between front-line analysts and senior administration in IT and Cybersecurity. Nicely-documented challenges going through fashionable analysts revolve round a excessive quantity of alerts, false positives, poor visibility of technical environments, and analysts spending an excessive amount of time on handbook duties.
The Affect of Alert Fatigue and False Positives
Analysts are overwhelmed with alerts. The knock-on impact of that is that fatigued analysts are prone to lacking key particulars in incidents, and infrequently conduct time-consuming triaging duties manually solely to finish up copying and pasting a generic closing remark right into a false constructive alert.
It’s possible that there’ll at all times be false positives. And plenty of would argue {that a} false constructive is healthier than a false unfavorable. However for proactive actions to be made, we should transfer nearer to the center of an incident. That requires diving into how analysts conduct the triage and investigation course of.
SHQ Response Platform for Triage and Investigation
A typical triage course of is commonly handbook, and leverages analysts to carry out particular person log searches for contextual data. From this data, they start to piece collectively a narrative of what has occurred and supply an concept of the general threat scale.
The SHQ Response Platform makes use of Synthetic Intelligence (AI) for log correlation, pulling data from completely different sources and visualizing it in a single incident web page. From this, crucial information is offered throughout a transparent timeline, and artifacts are up to date on the portal mechanically.
By having crucial information offered in a single place, an investigating analyst can minimize by the noise and keep in a single interface. They not have to pivot throughout a number of log sources or conduct handbook SIEM searches to assemble the related logs to then perceive the story of a safety incident.
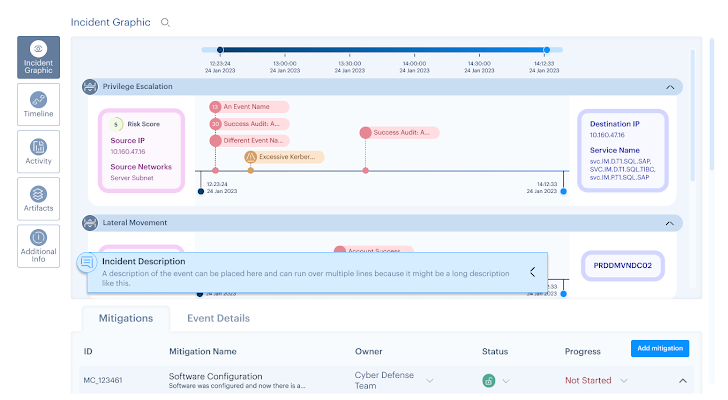 |
| Determine 1: Incident Graphic, SHQ Response Platform ©2024 SecurityHQ |
The timeline perform additionally permits an analyst to analyze the logic behind an alert or use case set off. That is proven with the related Indicators of Compromise (IoCs), which may be mechanically blocked utilizing back-end built-in instruments.
Incident Response Platform for Senior Stakeholders
Overwhelmed analysts swamped by false positives is endemic. Head of World SOC operations at SecurityHQ, Deodatta Wandhekar, put it finest by explaining that:
One should think about the best way to bridge this hole, with each a transparent deal with enterprise aims and threat urge for food, whereas retaining a degree of technical element.
Danger Register for Collaboration & Technique
SecurityHQ’s built-in Danger Register permits analysts and enterprise leaders to work collectively to drive mitigation actions, utilizing the technical acumen of operational employees to tell strategic enterprise choices.
This allows analysts to play a task in steering a cybersecurity program. By having a degree of technical possession, a extra collaborative strategy is fostered between operational analysts and administration employees. It additionally permits once-overworked analysts to obviously see the fruits of their labor mirrored in wider enterprise practices.
Subsequent Steps
SecurityHQ as each a consultative associate, and because the proprietor of such a platform, contributes to creating a greater relationship between administration and analysts by offering an intuitive, and executive-friendly, threat register.
From right here, the deal with proactive approaches and roadmaps over merely ‘firefighting’ and shutting incidents inside a Service Stage Settlement (SLA) creates the chance for significant change in an organization.
For extra data, communicate to an skilled right here. When you suspect a safety incident, report an incident right here.
Notice: This text was expertly written by Tim Chambers, Senior Cyber Security Supervisor at SecurityHQ
