The financially motivated risk actor often called FIN7 has been noticed leveraging malicious Google adverts spoofing reliable manufacturers as a method to ship MSIX installers that culminate within the deployment of NetSupport RAT.
“The threat actors used malicious websites to impersonate well-known brands, including AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Street Journal, Workable, and Google Meet,” cybersecurity agency eSentire mentioned in a report revealed earlier this week.
FIN7 (aka Carbon Spider and Sangria Tempest) is a persistent e-crime group that is been lively since 2013, initially dabbling in assaults focusing on point-of-sale (PoS) gadgets to steal fee knowledge, earlier than pivoting to breaching giant companies through ransomware campaigns.
Through the years, the risk actor has refined its ways and malware arsenal, adopting varied customized malware households akin to BIRDWATCH, Carbanak, DICELOADER (aka Lizar and Tirion), POWERPLANT, POWERTRASH, and TERMITE, amongst others.
FIN7 malware is usually deployed by spear-phishing campaigns as an entry to the goal community or host, though in current months the group has utilized malvertising methods to provoke the assault chains.
In December 2023, Microsoft mentioned it noticed the attackers counting on Google adverts to lure customers into downloading malicious MSIX software packages, which finally led to the execution of POWERTRASH, a PowerShell-based in-memory dropper that is used to load NetSupport RAT and Gracewire.
“Sangria Tempest […] is a financially motivated cybercriminal group currently focusing on conducting intrusions that often lead to data theft, followed by targeted extortion or ransomware deployment such as Clop ransomware,” the tech big famous on the time.
The abuse of MSIX as a malware distribution vector by a number of risk actors — doubtless owing to its capacity to bypass safety mechanisms like Microsoft Defender SmartScreen — has since prompted Microsoft to disable the protocol handler by default.
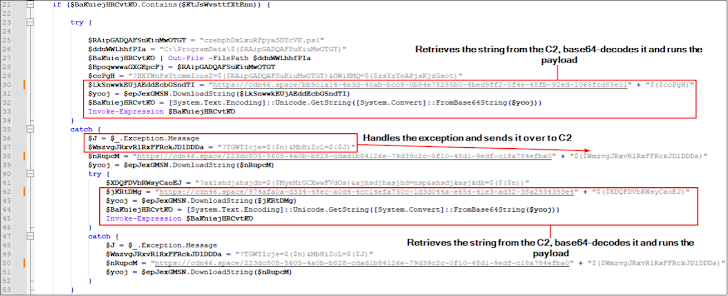
Within the assaults noticed by eSentire in April 2024, customers who go to the bogus websites through Google adverts are displayed a pop-up message urging them to obtain a phony browser extension, which is an MSIX file containing a PowerShell script that, in flip, gathers system info and contacts a distant server to fetch one other encoded PowerShell script.
The second PowerShell payload is used to obtain and execute the NetSupport RAT from an actor-controlled server.
The Canadian cybersecurity firm mentioned it additionally detected the distant entry trojan getting used to ship further malware, which incorporates DICELOADER by the use of a Python script.
“The incidents of FIN7 exploiting trusted brand names and using deceptive web ads to distribute NetSupport RAT followed by DICELOADER highlight the ongoing threat, particularly with the abuse of signed MSIX files by these actors, which has proven effective in their schemes,” eSentire mentioned.
Comparable findings have been independently reported by Malwarebytes, which characterised the exercise as singling out company customers through malicious adverts and modals by mimicking high-profile manufacturers like Asana, BlackRock, CNN, Google Meet, SAP, and The Wall Road Journal. It, nevertheless, didn’t attribute the marketing campaign to FIN7.
Information of FIN7’s malvertising schemes coincides with a SocGholish (aka FakeUpdates) an infection wave that is designed to focus on enterprise companions.
“Attackers used living-off-the-land techniques to collect sensitive credentials, and notably, configured web beacons in both email signatures and network shares to map out local and business-to-business relationships,” eSentire mentioned. “This behavior would suggest an interest in exploiting these relationships to target business peers of interest.”
It additionally follows the invention of a malware marketing campaign focusing on Home windows and Microsoft Workplace customers to propagate RATs and cryptocurrency miners through cracks for in style software program.
“The malware, once installed, often registers commands in the task scheduler to maintain persistence, enabling continuous installation of new malware even after removal,” Broadcom-owned Symantec mentioned.