Again in August 2023, Checkmarx and Sysdig introduced a brand new partnership. This collaboration permits clients of each Checkmarx and Sysdig to leverage the great visibility provided by Sysdig Runtime Insights to get much more worth from the Checkmarx One software safety platform.
These days, an rising variety of corporations are desperate to combine runtime intelligence into their safety instruments. This progressive method yields quite a few advantages, reminiscent of noise discount, and offers builders and safety groups with the mandatory context to focus and deal with probably the most crucial points first. Fixing and prioritizing vulnerabilities within the early phases of the software program lifecycle has turn into considerably simpler because of options like runtime insights.
Checkmarx and Sysdig are working collectively to facilitate this transition. Checkmarx’s One AppSec platform now incorporates Runtime Insights from Sysdig’s Cloud-Native Software Platform (CNAPP), empowering software safety groups to effectively prioritize and resolve safety points at cloud pace.
Advantages of Utilizing Checkmarx with Sysdig Runtime Insights
Sysdig’s Threat Highlight permits builders to handle vulnerabilities posing instant dangers by offering runtime insights context.
Now, let’s discover a number of the benefits of integrating Sysdig’s Threat Highlight into our associate Checkmarx.
Decrease the noise
Sysdig’s distinctive view on how vulnerabilities impression on functions enable joint Checkmarx and Sysdig clients to determine probably the most imminent safety dangers. By way of the mixing of runtime intelligence into Checkmarx’s Software program Composition Evaluation (SCA) instrument, builders can now prioritize addressing probably the most crucial vulnerabilities in use. That is completed successfully by considerably decreasing noise by as much as 95%.
Cut back the vulnerability fatigue
Builders usually discover themselves overwhelmed by the amount of vulnerabilities they encounter day by day, resulting in a flood of safety points. By way of the Checkmarx SCA and Sysdig partnership, an efficient developer suggestions loop is established, providing exact, significant, and actionable insights seamlessly built-in into the software program lifecycle. With this collaboration, Checkmarx customers acquire entry to runtime information, enabling them to make extra knowledgeable choices, decreasing their burden, and enhancing their total software program growth expertise.
Speed up software program supply
Using runtime insights permits builders to prioritize probably the most crucial vulnerabilities for instant decision whereas deferring others that aren’t actively exploited at runtime. This new method streamlines the software program growth and supply course of, facilitating quicker iteration cycles from growth to deployment. Develop, deal with, and ship with higher pace and effectivity.
Easy methods to Allow Runtime Insights Integration Step by Step
Conditions
First, for the sake of simplicity, let’s get proper to the purpose. It’s assumed that you’re acquainted with each safety instruments: Sysdig and Checkmarx. Moreover, it’s essential to have at the least one lively person account on each platforms. That is important as it’s necessary to own a Sysdig Threat Highlight API token to allow the mixing and entry runtime insights inside Checkmarx.
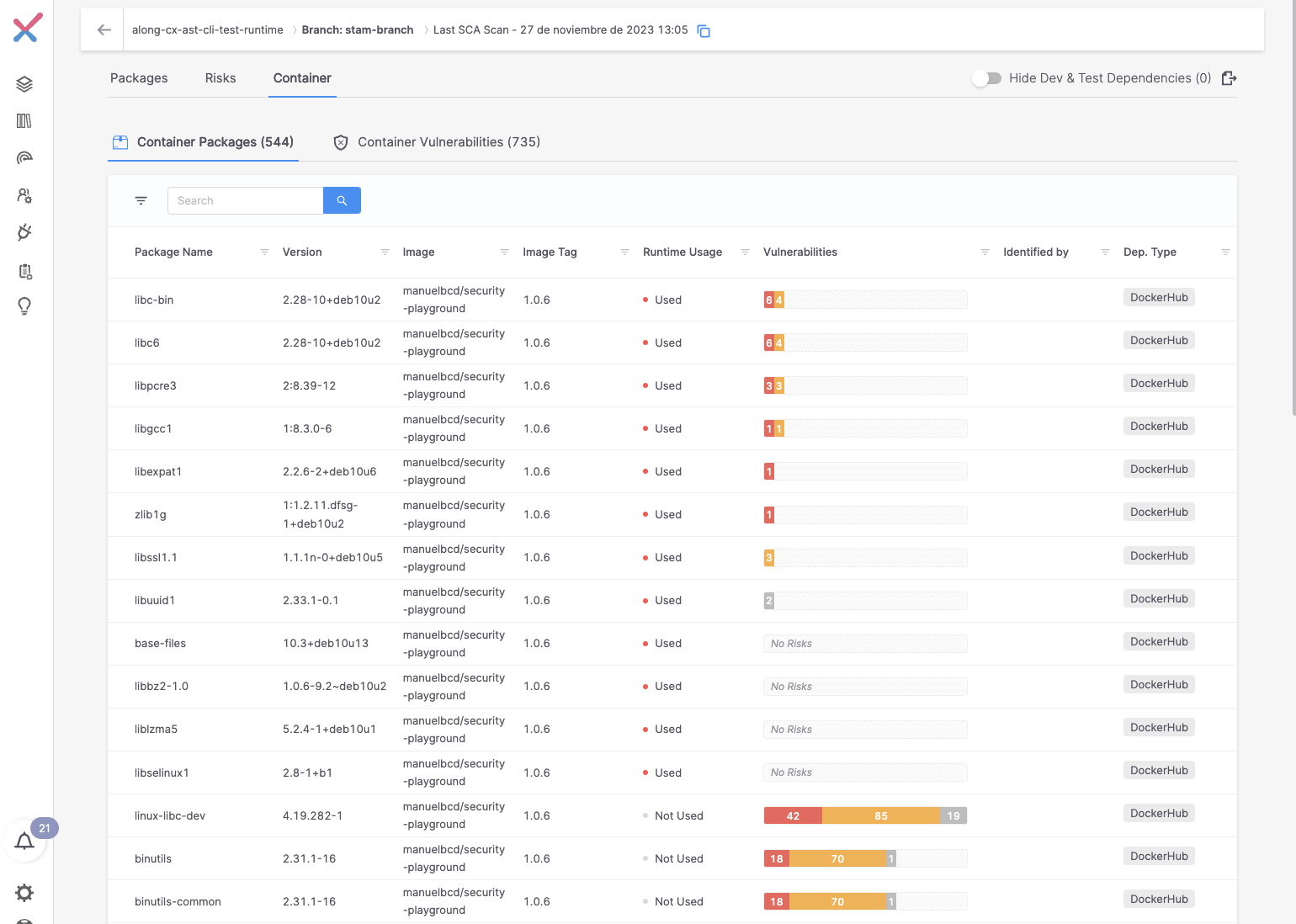
As part of integrating Sysdig runtime insights with Checkmarx SCA workflow, it’s essential to provoke a picture scan activity. Checkmarx has designed this course of to be streamlined by a single command line using Checkmarx One CLI and Checkmarx SCA resolver instruments. Moreover, the open supply Syft can also be used on this workflow for picture scanning.
Let’s arrange our surroundings:
- Obtain and configure Checkmarx One CLI, guaranteeing you insert your Checkmarx AST API Token when prompted. Depart the remaining fields clean.
- Obtain Checkmarx SCA resolver instrument.
- Obtain and set up Syft.
$ wget https://github.com/Checkmarx/ast-cli/releases/obtain/2.0.62/ast-cli_2.0.62_linux_x64.tar.gz $ tar zxvf ast-cli_2.0.62_linux_x64.tar.gz $ cx configure Creating listing Setup information: https://checkmarx.com/useful resource/paperwork/en/34965-68621-checkmarx-one-cli-quick-start-guide.html AST Base URI []: AST Base Auth URI (IAM) []: AST Tenant []: Do you need to use API Key authentication? (Y/N): Y AST API Key []: <PASTE_YOUR_API_KEY_HERE>
$ wget https://sca-downloads.s3.amazonaws.com/cli/newest/ScaResolver-linux64.tar.gz $ tar zxvf ScaResolver-linux64.tar.gz
$ curl -sSfL https://uncooked.githubusercontent.com/anchore/syft/foremost/set up.sh | sh -s -- -b /usr/native/bin
Allow Checkmarx + Sysdig integration
As of March 2024, Checkmarx customers who want to allow the Sysdig integration ought to contact a Checkmarx consultant for help with the method.
Easy methods to run the Checkmarx scanner
- Create a brand new Checkmarx challenge.
- Run a brand new picture scan activity.
- Test the brand new scan activity within the Checkmarx UI.
$ cx challenge create --project-name java-demo-app Mission ID Identify Created at Tags Teams ---------- ---- ---------- ---- ------ cdbabb8f-b984-4984-a47e-e625f39d2828 java-demo-app 11-28-23 [] []
$ cx scan create --project-name java-demo-app -s '/dwelling/victor/cicd-secure-scan/myapp' --branch stam-branch --scan-types sca --debug --async --sca-resolver './ScaResolver' --sca-resolver-params "--log-level Debug --scan-containers true --images quay.io/vhernandomartin/myimage:latest --containers-result-path /home/victor/cicd-secure-scan/myapp/.cxsca-container-results.json"
Conclusion
This new partnership enhances the capabilities of each Checkmarx and Sysdig clients by strengthening shift-left safety with invaluable runtime insights. Collectively, Checkmarx and Sysdig current a singular method to detecting and responding to safety threats.
Do you need to be taught extra? Go to the Checkmarx web site on the Sysdig ecosystem portal for additional data, or register to look at the beneath webinar.