Poland says a state-backed risk group linked to Russia’s navy intelligence service (GRU) has been focusing on Polish authorities establishments all through the week.
In response to proof discovered by CSIRT MON, the nation’s Pc Safety Incident Response Workforce (led by the Polish Minister of Nationwide Protection) and CERT Polska (the Polish laptop emergency response staff), Russian APT28 state hackers attacked a number of authorities establishments in a large-scale phishing marketing campaign.
The phishing emails tried tricking the recipients into clicking an embedded hyperlink that would offer them with entry to extra data concerning a “mysterious Ukrainian woman” promoting “used underwear” to “senior authorities in Poland and Ukraine.”
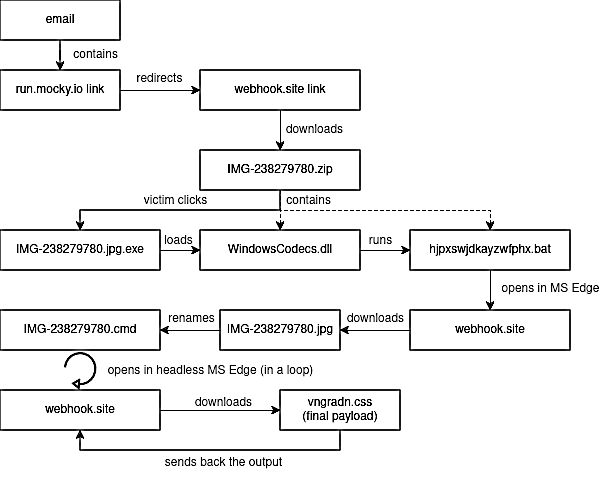
As soon as clicked, the hyperlink redirected them by a number of web sites earlier than touchdown on a web page that downloaded a ZIP archive. The archive contained a malicious executable disguised as a JPG picture file and two hidden information: a DLL and a .BAT script.
If the goal opens the camouflaged executable file, it hundreds the DLL by way of DLL facet loading, which runs the hidden script. The script shows a photograph of a lady in a swimsuit within the Microsoft Edge browser as a distraction whereas concurrently downloading a CMD file and altering its extension to JPG.
“The script we finally received collects only information about the computer (IP address and list of files in selected folders) on which they were launched, and then send them to the C2 server. Probably computers of the victims selected by the attackers receive a different set of the endpoint scripts,” CERT Polska stated.
The techniques and infrastructure utilized in these assaults are an identical to these utilized in one other extremely focused marketing campaign during which APT28 operatives used Israel-Hamas battle lures to backdoor units of officers from 13 nations, together with United Nations Human Rights Council members, with Headlace malware.
Because it surfaced within the mid-2000s, the Russian state-backed hacking group has coordinated many high-profile cyber-attacks and was linked to GRU’s Navy Unit 26165 in 2018.
APT28 hackers have been behind hacks of the Democratic Nationwide Committee (DNC) and the Democratic Congressional Marketing campaign Committee (DCCC) earlier than the 2016 U.S. Presidential Election and the breach of the German Federal Parliament (Deutscher Bundestag) in 2015.
The US charged a number of APT28 members for his or her involvement within the DNC and DCCC assaults in July 2018, whereas the Council of the European Union sanctioned APT28 in October 2020 for the Bundestag hack.
One week in the past, NATO and the European Union, with worldwide companions, additionally formally condemned a long-term APT28 cyber espionage marketing campaign towards a number of European nations, together with Germany and Czechia.
Germany stated the Russian risk group compromised many e-mail accounts belonging to members of the Social Democratic Social gathering’s government committee. The Czech Ministry of International Affairs additionally revealed that APT28 focused some Czech establishments in the identical Outlook marketing campaign in 2023.
The attackers exploited the CVE-2023-23397 Microsoft Outlook vulnerability within the assault, a safety flaw used as a zero-day to goal NATO members in Europe, Ukrainian authorities businesses, and NATO quick response corps beginning in April 2022.
“We call on Russia to stop this malicious activity and abide by its international commitments and obligations. With the EU and our NATO Allies, we will continue to take action to disrupt Russia’s cyber activities, protect our citizens and foreign partners, and hold malicious actors accountable,” the U.S. State Division stated in a press release.
