A suspected Vietnamese-origin risk actor has been noticed focusing on victims in a number of Asian and Southeast Asian international locations with malware designed to reap beneficial knowledge since no less than Might 2023.
Cisco Talos is monitoring the cluster underneath the title CoralRaider, describing it as financially motivated. Targets of the marketing campaign embody India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam.
“This group focuses on stealing victims’ credentials, financial data, and social media accounts, including business and advertisement accounts,” safety researchers Chetan Raghuprasad and Joey Chen stated. “They use RotBot, a customized variant of Quasar RAT, and XClient stealer as payloads.”
Different commodity malware utilized by the group includes a mix of distant entry trojans and data stealers comparable to AsyncRAT, NetSupport RAT, and Rhadamanthys.
The focusing on of enterprise and commercial accounts has been of specific focus for attackers working out of Vietnam, with varied stealer malware households like Ducktail, NodeStealer, and VietCredCare deployed to take management of the accounts for additional monetization.
The modus operandi entails using Telegram to exfiltrate the stolen data from sufferer machines, which is then traded in underground markets to generate illicit revenues.
“CoralRaider operators are based in Vietnam, based on the actor messages in their Telegram C2 bot channels and language preference in naming their bots, PDB strings, and other Vietnamese words hard-coded in their payload binaries,” the researchers stated.
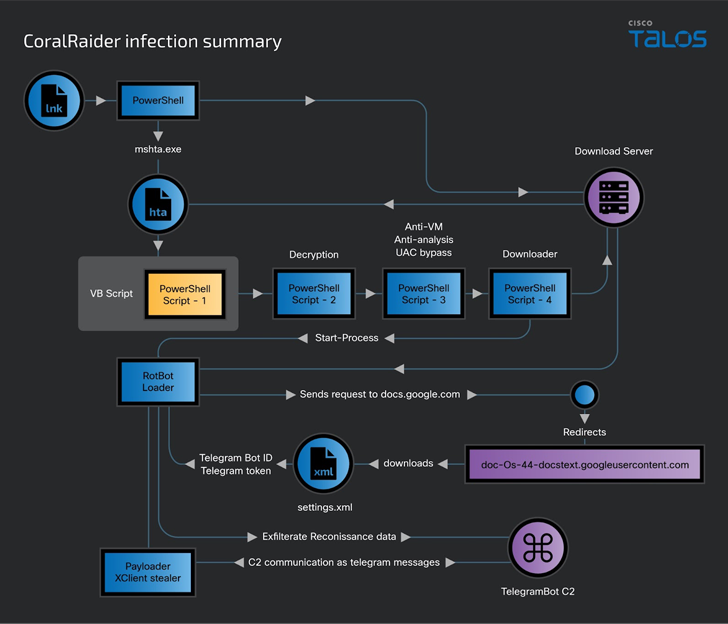
Assault chains begin with a Home windows shortcut file (LNK), though there may be at the moment no clear clarification as to how these recordsdata are distributed to the targets.
Ought to the LNK file be opened, an HTML software (HTA) file is downloaded and executed from an attacker-controlled obtain server, which, in flip, runs an embedded Visible Fundamental script.
The script, for its half, decrypts and sequentially executes three different PowerShell scripts which can be accountable for performing anti-VM and anti-analysis checks, circumventing Home windows Consumer Entry Management (UAC), disabling Home windows and software notifications, and downloading and working RotBot.
RotBot is configured to contact a Telegram bot and retrieve the XClient stealer malware and execute it in reminiscence, finally facilitating the theft of cookies, credentials, and monetary data from internet browsers like Courageous, Cốc Cốc, Google Chrome, Microsoft Edge, Mozilla Firefox, and Opera; Discord and Telegram knowledge; and screenshots.
XClient can also be engineered to siphon knowledge from victims’ Fb, Instagram, TikTok and YouTube accounts, gathering particulars concerning the fee strategies and permissions related to their Fb enterprise and advertisements accounts.
“RotBot is a variant of the Quasar RAT client that the threat actor has customized and compiled for this campaign,” the researchers stated. “[XClient] has extensive information-stealing capability through its plugin module and various modules for performing remote administrative tasks.”
The event comes as Bitdefender disclosed particulars of a malvertising marketing campaign on Fb that is profiting from the excitement surrounding generative AI instruments to push an assortment of data stealers like Rilide, Vidar, IceRAT, and a brand new entrant generally known as Nova Stealer.
The place to begin of the assault is the risk actor taking up an present Fb account and modifying its look to imitate well-known AI instruments from Google, OpenAI, and Midjourney, and increasing their attain by working sponsored advertisements on the platform.
One is imposter web page masquerading as Midjourney had 1.2 million followers earlier than it was taken down on March 8, 2023. The risk actors managing the web page had been primarily from Vietnam, the U.S., Indonesia, the U.Ok., and Australia, amongst others.
“The malvertising campaigns have tremendous reach through Meta’s sponsored ad system and have actively been targeting European users from Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and elsewhere,” the Romanian cybersecurity firm stated.