Microsoft has highlighted a novel assault dubbed “Dirty Stream,” which may permit malicious Android apps to overwrite information in one other utility’s residence listing, probably resulting in arbitrary code execution and secrets and techniques theft.
The flaw arises from the improper use of Android’s content material supplier system, which manages entry to structured information units meant to be shared between totally different purposes.
This method incorporates information isolation, URI permissions, and path validation safety measures to forestall unauthorized entry, information leaks, and path traversal assaults.
When applied incorrectly, customized intents, that are messaging objects that facilitate communication between parts throughout Android apps, may bypass these safety measures.
Examples of incorrect implementations embrace trusting unvalidated filenames and paths in intents, misuse of the ‘FileProvider’ part, and insufficient path validation.
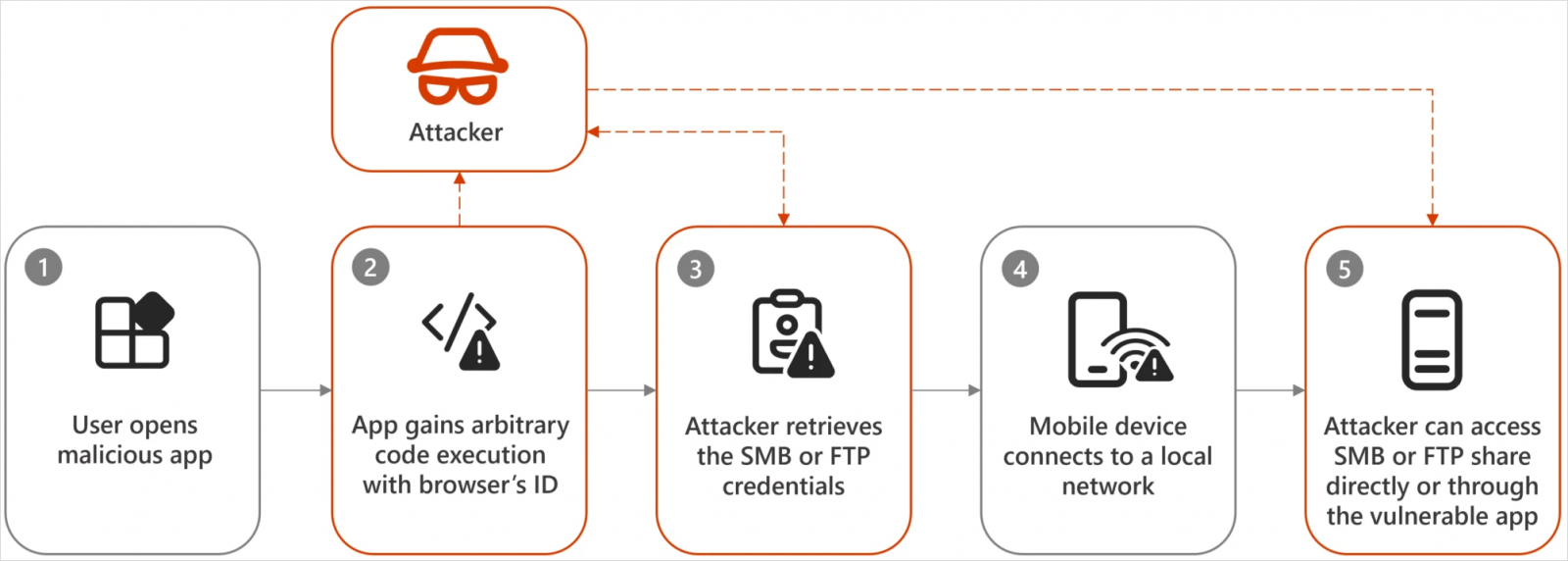
Soiled Stream permits malicious apps to ship a file with a manipulated filename or path to a different app utilizing a customized intent. The goal app is misled into trusting the filename or path and executes or shops the file in a crucial listing.
.png)
Supply: Microsoft
This manipulation of the info stream between two Android apps turns a typical OS-level operate right into a weaponized instrument and may result in unauthorized code execution, information theft, or different malicious outcomes.
Supply: Microsoft
Microsoft researcher Dimitrios Valsamaras famous that these incorrect implementations are sadly plentiful, impacting apps put in over 4 billion instances and providing an enormous assault floor.
“We identified several vulnerable applications in the Google Play Store that represented over four billion installations,” reads the report.
“We anticipate that the vulnerability pattern could be found in other applications. We’re sharing this research so developers and publishers can check their apps for similar issues, fix as appropriate, and prevent introducing such vulnerabilities into new apps or releases.”
Two apps highlighted as weak to Soiled Stream assaults in Microsoft’s report are Xiaomi’s File Supervisor utility, which has over a billion installations, and WPS Workplace, which counts round 500 million installs.
Each corporations had been conscious of the findings and collaborated with Microsoft to deploy fixes to mitigate the dangers posed by the vulnerability.
Microsoft’s findings had been shared with the Android developer neighborhood via an article on the Android Builders web site to forestall comparable vulnerabilities in future builds.
Google additionally up to date its app safety steering to focus on widespread implementation errors within the content material supplier system that permit safety bypasses.
As for finish customers, there’s not a lot they’ll do apart from conserving the apps they use updated and avoiding downloading APKs from unofficial third-party app shops and different poorly vetted sources.
