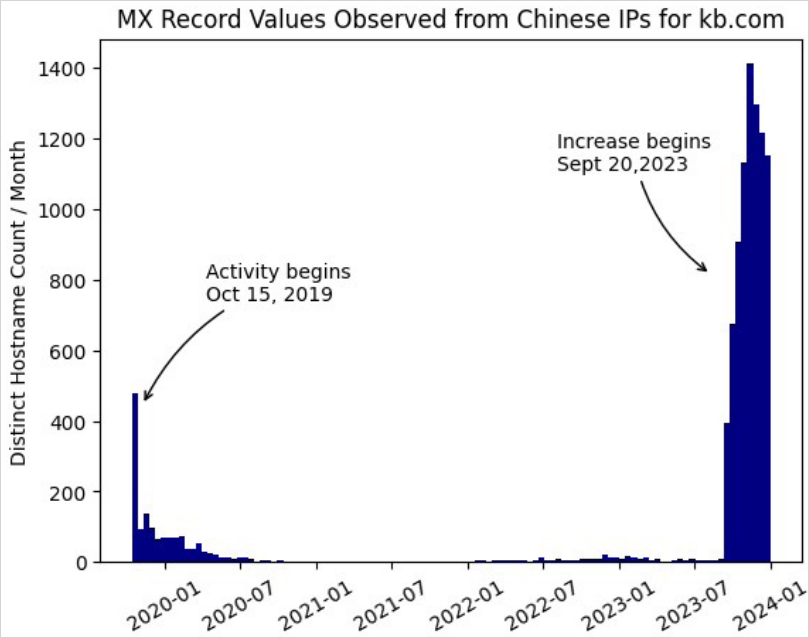
A brand new cluster of exercise tracked as “Muddling Meerkat” is believed to be linked to a Chinese language state-sponsored menace actor’s manipulation of DNS to probe networks globally since October 2019, with a spike in exercise noticed in September 2023.
A notable facet of Muddling Meerkat’s exercise is the manipulation of MX (Mail Trade) information by injecting faux responses by means of China’s Nice Firewall (GFW), an uncommon and beforehand unseen conduct for the nation’s web censorship system.
Found by Infoblox, the exercise doesn’t have a transparent objective or motivation however demonstrates sophistication and superior capabilities to control world DNS techniques.
Supply: Infoblox
Muddling Meerkat operations
By trying into large volumes of DNS information, Infoblox researchers found an exercise they are saying might simply fly below the radar or be mistaken for innocuous.
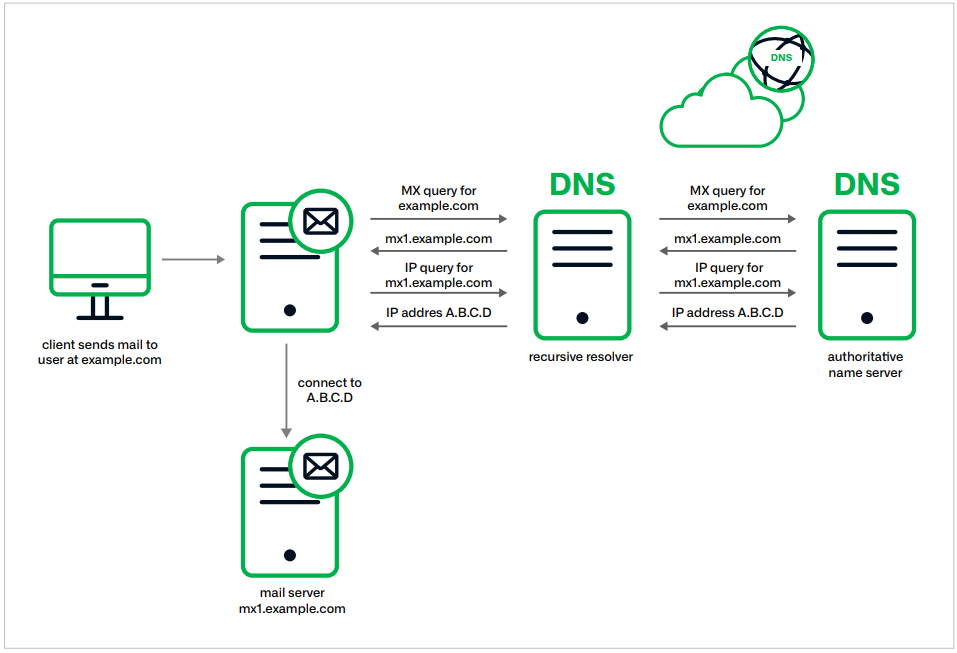
DNS is a vital practical part of the web, translating human-readable domains into IP addresses that computer systems use to establish one another on the community and set up connections.
Muddling Meerkat manipulates DNS queries and responses by concentrating on the mechanism by which resolvers return the IP addresses.
For example, they’ll provoke false MX document responses from the GFW to fiddle with the routing and probably misdirect emails.
Supply: Infoblox
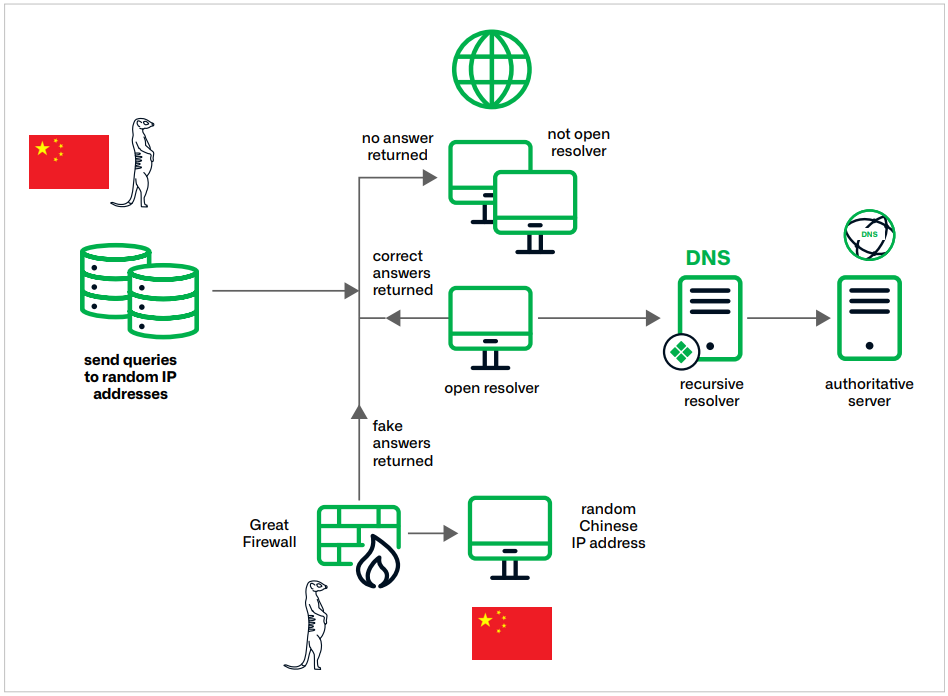
The Nice Firewall’s perform is often to filter and block content material by intercepting DNS queries and offering invalid responses, redirecting customers away from sure websites. Muddling Meerkat’s actions trigger it to concern faux responses that serve goals similar to testing the resilience and conduct of different networks.
“The GFW will be described as an “operator on the side,” meaning that it does not alter DNS responses directly but injects its own answers, entering into a race condition with any response from the original intended destination. When the GFW response is received by the requester first, it can poison their DNS cache. In addition to the GFW, China operates a system referred to as the Great Cannon (GC). The GC is an“operator in the middle,” permitting it to change packets en path to their vacation spot.”
❖ InfoBlox
To additional obfuscate their actions, Muddling Meerkat makes DNS requests for random subdomains of their goal domains, which regularly do not exist.
Although this resembles an assault named “Slow Drip DDoS,” Infoblox notes that in Muddling Meerkat’s case, the queries are small in scale and aimed toward testing slightly than disruption.
The menace actor additionally exploits open resolvers to obfuscate their exercise and engages with each authoritative and recursive resolvers.
Supply: Infoblox
Infoblox experiences that Muddling Meerkat chooses goal domains with brief names registered earlier than 2000, making them much less prone to be on DNS blocklists.
As for the aim of the exercise, Muddling Meerkat may be mapping networks and evaluating their DNS safety to plan future assaults, or their objective could possibly be to create DNS “noise,” which can assist cover extra malicious actions and confuse admins who try and pinpoint the supply of anomalous DNS requests.
The Infoblox report offers an entire listing of Muddling Meerkat indicators of compromise (IoCs) and methods, techniques, and procedures (TTPs), together with lists of domains that will be blocked with out important influence attributable to internet hosting no web site, internet hosting unlawful content material, or being parked.
