Safety researchers analyzing phishing campaigns that concentrate on United States Postal Service (USPS) noticed that the visitors to the pretend domains is often much like what the reputable web site information and it’s even larger throughout holidays.
Phishing operations sometimes goal individuals’s delicate data (account credentials, card particulars) or attempt to trick customers into making funds to fraudulent retailers or overlaying charges supposedly required for clearing gadgets which have been positioned on maintain for varied causes.
USPS phishing
In the course of the 2023 vacation season, Akamai Applied sciences noticed a major quantity of DNS queries going to “combosquatting” domains that impersonate the USPS service.
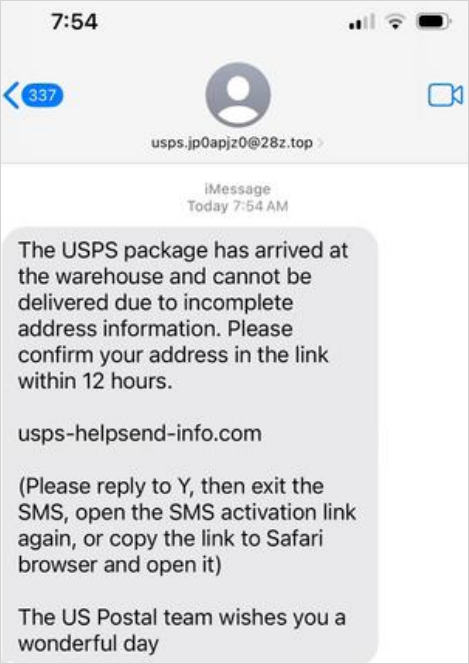
Akamai began investigating USPS-themed phishing in October 2023 after an worker obtained a suspicious SMS that redirected to a web site containing malicious JavaScript code.
Akamai
Subsequent, the analysts compiled a listing of all domains utilizing the identical JS file from the previous 5 months and saved solely these with the USPS string of their identify.
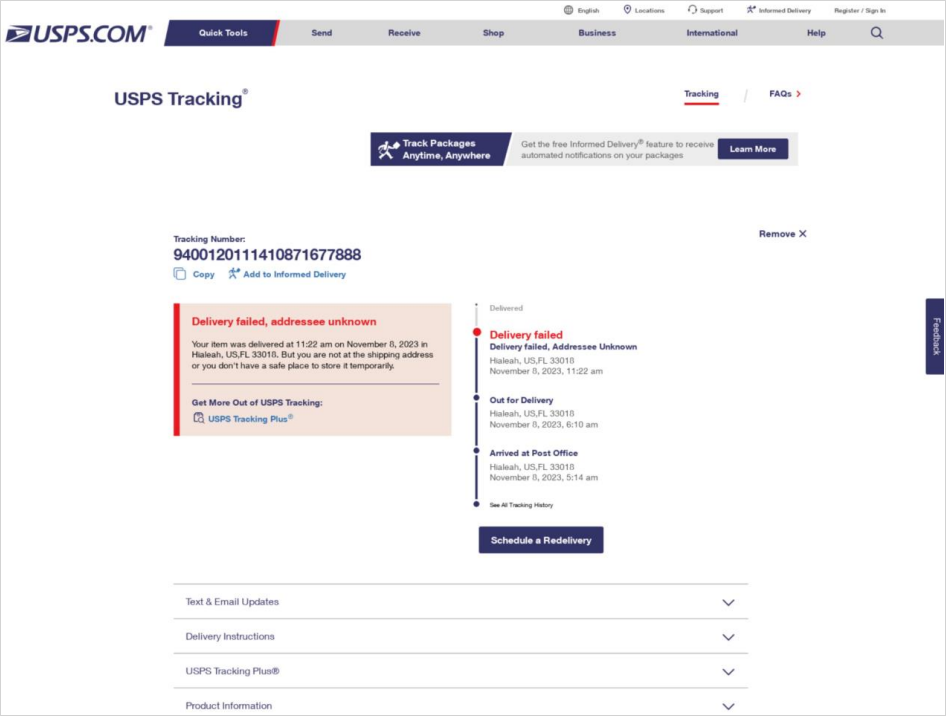
The design of those pages may be very convincing and seem as actual replicas of the genuine USPS web site with life like monitoring pages for standing updates.
Akamai
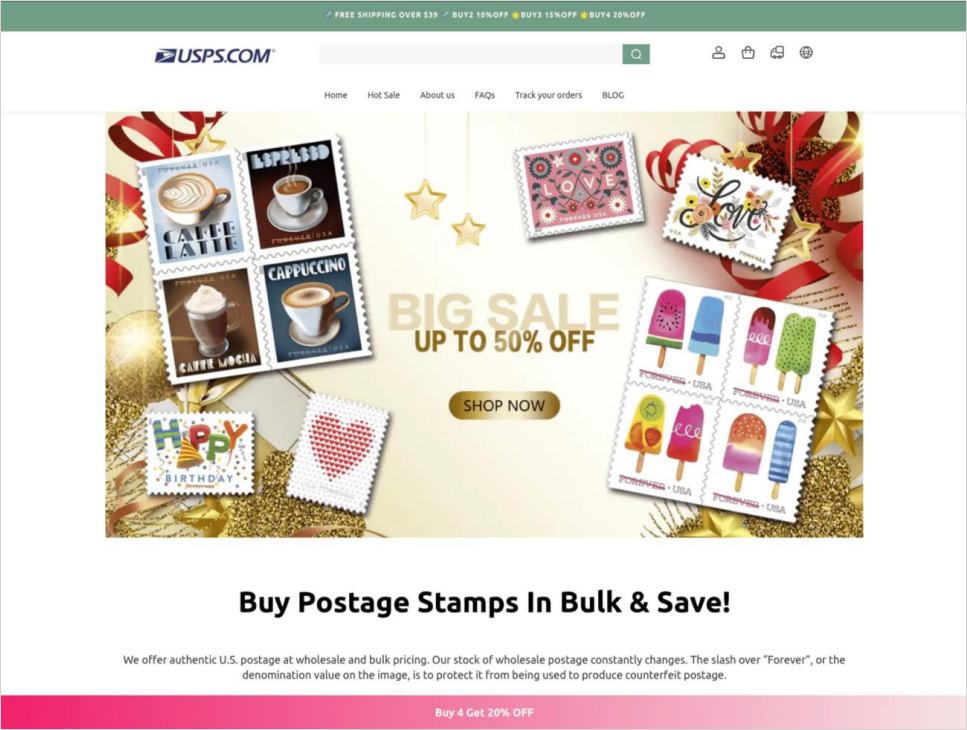
In a single case, the phishing actors arrange what seems to be like a devoted postage gadgets store, which began getting vital visitors in late November, as customers sought to purchase presents and collectibles for the vacation season.
Akamai
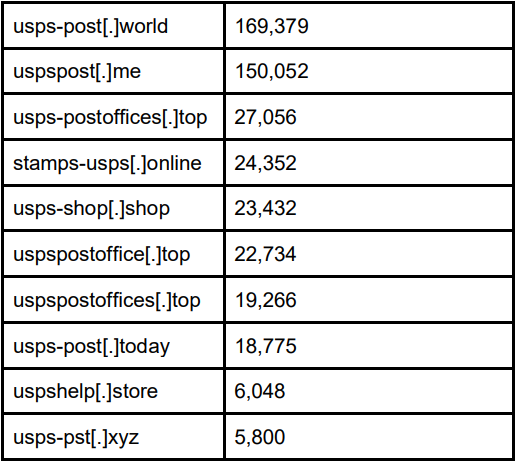
From October 2023 to February 2024, the preferred malicious domains that Akamai found obtained practically half one million queries, with two surpassing 150k every.
Akamai
The preferred top-level domains (TLDs) related to phishing USPS-themed domains had been:
- .com – 4459 domains and 271,278 queries
- .high – 3,063 domains and 274,257 queries
- .store – 566 domains and 58,194 queries
- .xyz – 397 domains and 30,870 queries
- .org – 352 domains and 16,391 queries
- .information – 257 domains and seven,597 queries
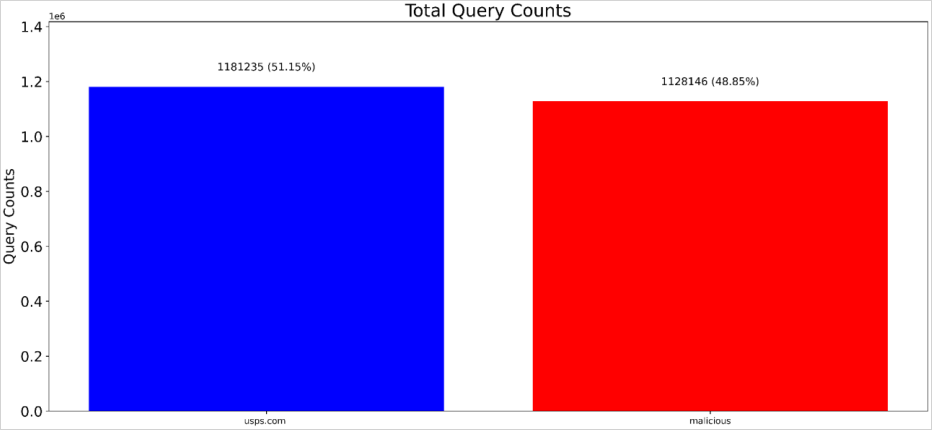
The full queries generated by all malicious web sites uncovered by Akamai’s analysis through the examined interval is over 1,128,146, simply in need of the 1,181,235 queries recorded for the reputable USPS web site.
Akamai
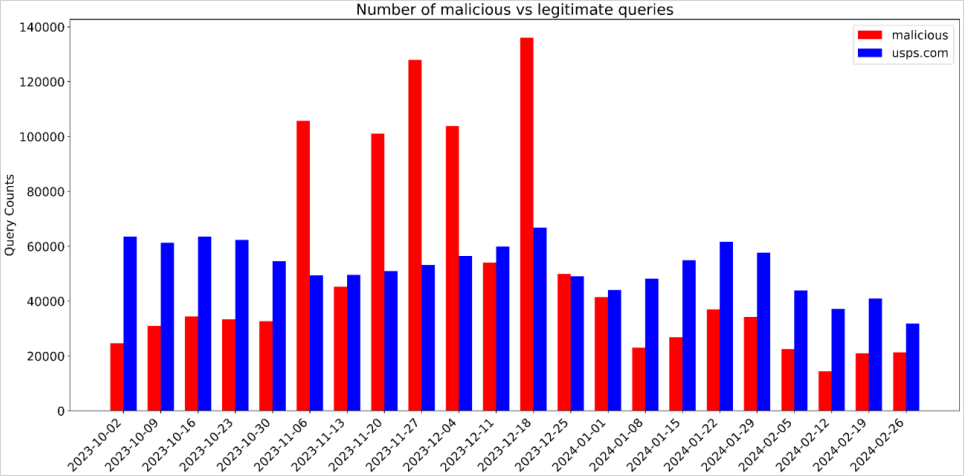
Nevertheless, the stats present that visitors to malicious domains between November to December was larger in comparison with the reputable one, indicating elevated malicious exercise throughout winter vacation season.
Akamai
Akamai solely targeted this analysis on USPS, so the precise scale of those combosquatting campaigns that doubtlessly embody many extra manufacturers is probably going bigger.
Customers ought to train warning and be skeptic about any SMS or electronic mail messages about package deal shipments.
To confirm the legitimacy of such communications, it is advisable to make use of the official web site (by manually loading it within the browser) to verify the supply standing of a product.
Clicking on the hyperlinks included in messages for monitoring parcels might result in malicious places.
