The North Korea-linked menace actor referred to as Lazarus Group employed its time-tested fabricated job lures to ship a brand new distant entry trojan referred to as Kaolin RAT.
The malware might, “aside from standard RAT functionality, change the last write timestamp of a selected file and load any received DLL binary from [command-and-control] server,” Avast safety researcher Luigino Camastra stated in a report revealed final week.
The RAT acts as a pathway to ship the FudModule rootkit, which has been lately noticed leveraging a now-patched admin-to-kernel exploit within the appid.sys driver (CVE-2024-21338, CVSS rating: 7.8) to acquire a kernel learn/write primitive and finally disable safety mechanisms.
The Lazarus Group’s use of job supply lures to infiltrate targets isn’t new. Dubbed Operation Dream Job, the long-running marketing campaign has a monitor file of utilizing numerous social media and prompt messaging platforms to ship malware.
These preliminary entry vectors trick targets into launching a malicious optical disc picture (ISO) file bearing three recordsdata, one in all which masquerades as an Amazon VNC shopper (“AmazonVNC.exe”) that, in actuality, is a renamed model of a official Home windows software referred to as “alternative.exe.”
The 2 different recordsdata are named “version.dll” and “aws.cfg.” The executable “AmazonVNC.exe” is used to side-load “version.dll,” which, in flip, spawns an IExpress.exe course of and injects into it a payload residing inside “aws.cfg.”
The payload is designed to obtain shellcode from a command-and-control (C2) area (“henraux[.]com”), which is suspected to be an actual-but-hacked web site belonging to an Italian firm that focuses on excavating and processing marble and granite.
Whereas the precise nature of the shellcode is unclear, it is stated for use to launch RollFling, a DLL-based loader that serves to retrieve and launch the next-stage malware named RollSling, which was disclosed by Microsoft final 12 months in reference to a Lazarus Group marketing campaign exploiting a essential JetBrains TeamCity flaw (CVE-2023-42793, CVSS rating: 9.8).
RollSling, executed instantly in reminiscence in a possible try and evade detection by the safety software program, represents the following section of the an infection process. Its major perform is to set off the execution of a 3rd loader dubbed RollMid that is additionally run within the system’s reminiscence.
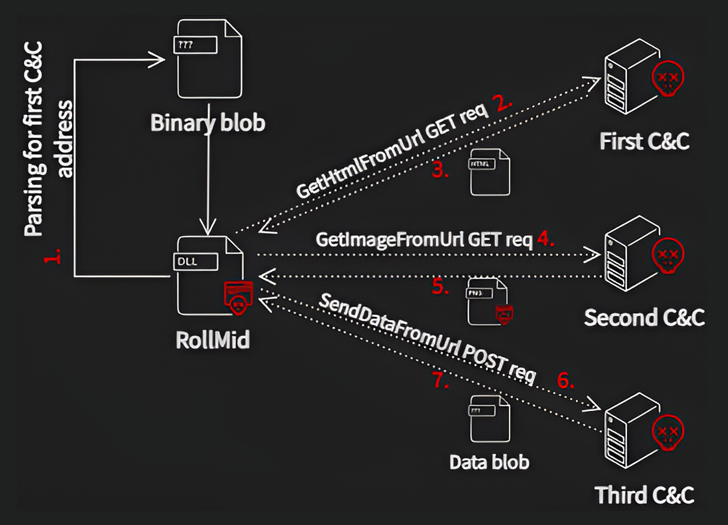
RollMid comes fitted with capabilities to set the stage for the assault and set up contact with a C2 server, which entails a three-stage technique of its personal as follows –
- Talk with the primary C2 server to fetch a HTML containing the deal with of the second C2 server
- Talk with the second C2 server to fetch a PNG picture that embeds a malicious part utilizing a way referred to as steganography
- Transmit information to the third C2 server utilizing the deal with specified within the hid information throughout the picture
- Retrieve an extra Base64-encoded information blob from the third C2 server, which is the Kaolin RAT
The technical sophistication behind the multi-stage sequence, whereas little doubt complicated and complicated, borders on overkill, Avast opined, with the Kaolin RAT paving the way in which for the deployment of the FudModule rootkit after organising communications with the RAT’s C2 server.
On high of that, the malware is provided to enumerate recordsdata; perform file operations; add recordsdata to the C2 server; alter a file’s final modified timestamp; enumerate, create, and terminate processes; execute instructions utilizing cmd.exe; obtain DLL recordsdata from the C2 server; and connect with an arbitrary host.
“The Lazarus group targeted individuals through fabricated job offers and employed a sophisticated toolset to achieve better persistence while bypassing security products,” Camastra stated.
“It is evident that they invested significant resources in developing such a complex attack chain. What is certain is that Lazarus had to innovate continuously and allocate enormous resources to research various aspects of Windows mitigations and security products. Their ability to adapt and evolve poses a significant challenge to cybersecurity efforts.”