North Korean hackers have been exploiting the updating mechanism of the eScan antivirus to plant backdoors on massive company networks and ship cryptocurrency miners via GuptiMiner malware.
Researchers describe GuptiMiner as “a highly sophisticated threat” that may carry out DNS requests to the attacker’s DNS servers, extract payloads from photographs, signal its payloads, and carry out DLL sideloading.
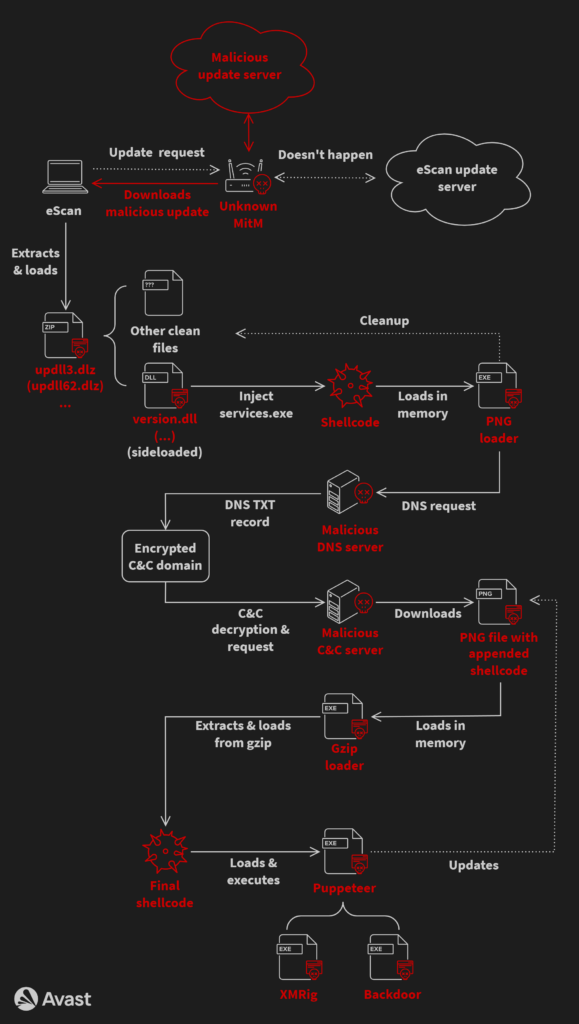
Delivering GuptiMiner by way of eScan updates
In a report launched at this time, cybersecurity firm Avast says that the risk actor behind GuptiMiner had an adversary-in-the-middle (AitM) place to hijack the conventional virus definition replace bundle and exchange it with a malicious one named ‘updll62.dlz.’
The malicious file contains the mandatory antivirus updates in addition to a GuptiMiner malware as a DLL file named ‘version.dll.’
The eScan updater processes the bundle as regular, unpacking and executing it. Throughout that stage, the DLL is sideloaded by eScan’s respectable binaries, giving the malware system-level privileges.
Subsequent, the DLL fetches further payloads from the attacker’s infrastructure, establishes persistence on the host by way of scheduled duties, performs DNS manipulation, injects shellcode on respectable processes, makes use of code virtualization, shops XOR-encrypted payloads within the Home windows registry, and extracts PEs from PNGs.
GuptiMiner additionally checks if the system it runs has greater than 4 CPU cores and 4GB of RAM to evade sandbox environments, and determines if Wireshark, WinDbg, TCPView, 360 Whole Safety, Huorong Web Safety, Course of Explorer, Course of Monitor, and OllyDbg are actively operating.
AhnLab and Cisco Talos merchandise are additionally deactivated if they’re operating on the breached machine. Under is a full diagram of the an infection chain:
Avast
Avast researchers say that GuptiMiner could also be linked to the North Korean APT group Kimsuki, based mostly on similarities between the data stealing operate and the Kimsuky keylogger.
The researchers additionally found that some elements of the GuptiMiner operation counsel a potential connection to Kimsuki. A commonality is the usage of the area mygamesonline[.]org, which is ordinarily seen in Kimsuky operations.
Deployed malware instruments
The hackers used GuptiMiner to deploy a number of malware on compromised programs, together with two distinct backdoors and the XMRig Monero miner.
The primary backdoor is an enhanced model of Putty Hyperlink, deployed on company programs to scan the native community for susceptible programs and pivot factors for lateral motion.
It particularly seeks out Home windows 7 and Home windows Server 2008 programs, exploiting them via SMB visitors tunneling.
The second backdoor is a fancy modular malware that scans the host for saved non-public keys and cryptocurrency wallets, and creates a registry key to mark the completion of the scan, to keep away from noisy repeats.
It might probably settle for instructions to put in further modules in registry, additional enhancing its capabilities inside contaminated environments. Nevertheless, Avast didn’t present further particulars.
The attackers additionally dropped the XMRig miner in lots of circumstances, which is in distinction with the sophistication exhibited within the analyzed marketing campaign and might be an try to divert consideration from the principle assault line.
eScan’s response
Avast researchers disclosed the exploited vulnerability to eScan and the antivirus vendor confirmed that the difficulty was mounted.
eScan additionally stated that the final comparable report they acquired was in 2019. In 2020, the seller carried out a extra sturdy checking mechanism to make it possible for non-signed binaries had been rejected.
In the latest implementation, eScan’s replace downloads happen over HTTPS to make sure encrypted communication for shoppers interacting with the seller’s cloud-facing servers.
Nevertheless, Avast reviews that it continues to look at new infections by GuptiMiner, which may point out outdated eScan shoppers.
The whole record of GuptiMiner indicators of compromise (IoCs) to assist defenders mitigate this risk will be discovered on this GitHub web page.
