Between crossovers – Do menace actors play soiled or determined?
In our dataset of over 11,000 sufferer organizations which have skilled a Cyber Extortion / Ransomware assault, we observed that some victims re-occur. Consequently, the query arises why we observe a re-victimization and whether or not or not that is an precise second assault, an affiliate crossover (that means an affiliate has gone to a different Cyber Extortion operation with the identical sufferer) or stolen knowledge that has been travelling and re-(mis-)used. Both manner, for the victims neither is sweet information.
However very first thing’s first, let’s discover the present menace panorama, dive into considered one of our most up-to-date analysis focuses on the dynamics of this ecosystem; after which discover our dataset on Regulation Enforcement actions on this house. May the re-occurrence that we observe be foul play by menace actors and thus present how desperately they’re attempting to regain the belief of their co-offenders after disruption efforts by Regulation Enforcement? Or are they simply enjoying soiled after receiving no funds from the sufferer?
What we’re observing within the Cy-X menace panorama
Cyber Extortion (Cy-X) or Ransomware, because it’s extra generally recognized, is a subject that has garnered numerous consideration over the previous three to 4 years. Orange Cyberdefense has lined this menace extensively since 2020.
Within the newest annual safety report, the Safety Navigator 2024 (SN24), analysis confirmed a rise of 46% between 2022 and 2023 (interval of This fall 2022 to Q3 2023). Updating our dataset, we discover that the precise enhance is even greater with just below 51% enhance. The up to date quantity is because of the dynamic nature of the dataset; the ecosystem constantly modifications and so we solely grew to become conscious of sure leak websites and their victims as soon as the analysis interval had concluded.
Sadly, this simply additional compounds the fact. Predicting whether or not this degree of enhance shall be maintained is tough. Cy-X could have reached a saturation level, the place we’d see the Cy-X menace persevering with on the 2023 ranges. Alternatively, if we do observe the sufferer depend patterns of the final years (decrease numbers at first of the yr, rising all year long), which might have the alternative impact, offering us with an ever-growing sufferer depend as soon as extra. Nonetheless, we imagine that the Cy-X sufferer depend ranges will stay regular for now, and if we’re lucky, it may chance level to a lower in extortion victims. However, we’re a good distance off from claiming victory.
Six months have handed for the reason that finish of the SN24 Cy-X dataset was mentioned within the report, and quite a bit has occurred throughout that point. The overall variety of victims for This fall 2023 and Q1 2024 tallies to 2,141 – practically all of the victims recorded for the entire of 2022, which was 2,220 victims. The quantity of this sufferer depend is exceptional provided that two of probably the most lively Cy-X teams had been (tried) to be disrupted throughout this time. Regulation Enforcement (LE) aimed to disrupt ALPHV in December 2023, the place they confirmed resistance by “unseizing” themselves simply days after. LE then took down LockBit’s infrastructure in February 2024, nevertheless, this solely meant a couple of days’ downtime for LockBit since additionally they managed to get again on-line a couple of days after the preliminary takedown. Despite the fact that the 2 Cy-X operations appeared very resistant on the time, ALPHV (BlackCat) went offline at first of March 2024, “exiting” the sport with most definitely a so-called exit rip-off.
Efforts to disrupt this risky ecosystem – challenges attributable to brief lifespans of Cy-X manufacturers
Irrespective of its impact, earlier LE actions render vital insights into Cy-X operations. One instance is the darkish variety of the Cy-X crime, which is the variety of victims we do not find out about as a result of they are not uncovered on the leak websites that we monitor. Figuring out the darkish quantity would assist us full the image of the present Cy-X menace. Thus, the entire image would come with the precise variety of victims that embrace our partial view of the victims that had been uncovered on the leak websites (our knowledge) and the sufferer organizations we are going to by no means find out about (the darkish quantity). The takedown of Hive in 2023 revealed the next variety of victims than what we had recorded from their knowledge leak web site, the place the precise quantity was 5 to six occasions greater. If we use the multiplier of six with the recorded sufferer depend – 11,244 – from the beginning of January 2020 to finish of March 2024, then the true sufferer depend could possibly be as excessive as 67,000 victims throughout all Cy-X teams.
Cl0p, who’s probably the most persistent menace actor in our dataset, was very busy throughout 2023 and was chargeable for 11% of all victims. Nonetheless, for the final six months since that evaluation solely 7 victims had been noticed on the Cy-X group’s knowledge leak web site. Cl0p has flickered up up to now, mass exploiting vulnerabilities, solely to drag again into the shadows, therefore this would possibly simply be Cl0p’s modus operandi.
Safety Navigator 2024 is Right here – Obtain Now
The newly launched Safety Navigator 2024 presents important insights into present digital threats, documenting 129,395 incidents and 25,076 confirmed breaches. Greater than only a report, it serves as a information to navigating a safer digital panorama.
What’s Inside?#
- 📈 In-Depth Evaluation: Discover tendencies, assault patterns, and predictions. Be taught from case research in CyberSOC and Pentesting.
- 🔮 Future-Prepared: Equip your self with our safety predictions and analysis abstract.
- 👁️ Actual-Time Information: From Darkish Internet surveillance to industry-specific statistics.
Keep one step forward in cybersecurity. Your important information awaits!
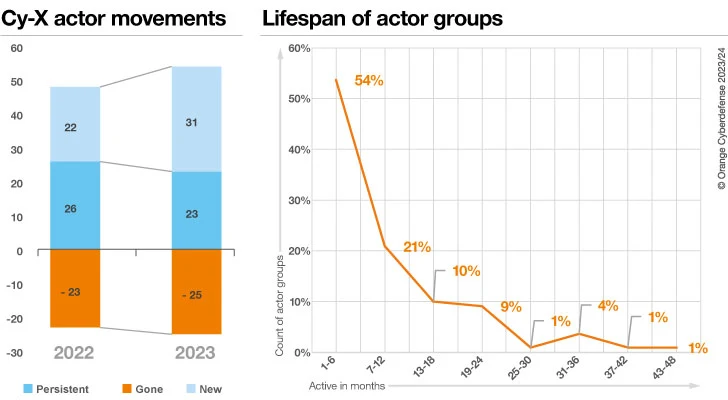
The overall variety of lively Cy-X teams fluctuates over time, and sure teams persist longer than others. The Safety Navigator 2024 report addressed this query by analyzing the year-on-year modifications. Total, 2023 did see a web enhance within the variety of lively Cy-X teams in contrast with 2022. Usually, it is a very risky ecosystem with a number of motion in it. Our analysis discovered that 54% of Cy-X ‘manufacturers’ disappear after 1 to six months of operation. There have been fewer Cy-X teams carried over to 2023, however the enhance within the variety of new Cy-X teams resulted in a web achieve in exercise. Additional affirmation of the ephemeral nature of those teams. Sarcastically, LockBit3 and ALPHV had been listed beneath the grouping of “Persistent” for 2023.
This analysis was carried out as a part of the examination of the effectiveness in defending towards Cy-X. LE and authorities companies from throughout the globe are working exhausting at eliminating Cyber Extortion as it’s actually a world downside. Within the final two and a half years we’ve seen a gentle enhance in LE exercise, recording 169 actions combating cybercrime.
Of all documented LE actions, we noticed Cyber Extortion addressed probably the most. 14% of all actions had been attributed to be associated to the crime of Cyber Extortion, adopted by Hacking and Fraud with 11% every respectively. Crypto-related crimes claimed a share of 9%. Nearly half of LE actions concerned arrests and the sentencing of people or teams.
In our newest Safety Navigator report, we wrote that “in 2023, we specifically noted increased efforts to take down or disrupt the infrastructure and hosting services threat actors (mis-)used.” With our up to date dataset from the final 6 months, we do see a good greater proportion of the class “Law Enforcement disrupts”. Right here, we collected actions corresponding to bulletins on kicking off worldwide taskforces to fight Ransomware, LE tricking menace actors in offering them decryption keys, seizing infrastructure, infiltrating cybercrime markets, and many others. Whereas we’ve beforehand argued whether or not the actions that we do see executed most often, e.g. arrest and seizures may not be as efficient, the 2 newest LE actions have been very attention-grabbing to observe.
In ALPHV’s case, who in first response appeared very resilient towards the LE’s efforts to disrupt it, has fled the scene and (most definitely) performed an exit rip-off. This may enormously undermine “the trust” throughout the Ransomware-as-a-Service (RaaS) ecosystem, there could possibly be a short-term lower within the variety of victims as associates and different actors assess their dangers. On the identical time, there’s a void to fill, and traditionally it doesn’t take lengthy for a brand new (re-)model to fill this hole.
Just like ALPHV, LockBit has claimed to have survived the preliminary takedown, however on the earth of Cyber Extortion, popularity is all the things. Would associates proceed to do enterprise with the “revived” LockBit not marvel if which may be a LE honeypot?
Re-victimization of Cy-X victims in type of desperation or affiliate crossovers
We all know by now that the cybercrime ecosystem is a fancy one, together with many various sort of actors, roles and actions. That is very true for the kind of cybercrime we’re monitoring – Cyber Extortion. Over the previous decade, the ecosystem of Cybercrime-as-a-Service (CaaS) has actually advanced and added a number of challenges to observe this crime. One such problem is that not one single menace actor executes one assault from starting to finish (the total assault chain).
As we see within the graph above, many various roles play an element in a Cy-X ecosystem, most notably the associates aka ‘Affiliate Ransomware Operator’. Associates are a important a part of the Cyber Extortion ecosystem as they permit the dimensions and attain of those cyber-attacks. This construction additionally provides a layer of separation between the Ransomware creators (Malware Writer) and the attackers (Affiliate), which might present a level of authorized and operational manoeuvrability for the builders. The affiliate mannequin has contributed to the proliferation of Ransomware, making it a major cybersecurity menace right now. The character of those associations doesn’t lend itself to the reassurance of exclusivity. In some instances, it appears that evidently sufferer knowledge propagates by the cybercrime ecosystem in methods that aren’t at all times clear.
When analyzing the sufferer listings on Cy-X knowledge leak websites, we observe the re-appearance of victims. That is nothing new, we’ve been observing this phenomenon since 2020. However we lastly have a sufficiently big dataset to make an evaluation on the sightings of re-occurrences to research whether or not these are certainly re-victimizations or different dynamics of the ecosystem that even the ecosystem itself will not be conscious of. We discover, for instance, that some victims are listed months or years aside, whereas others are reposted inside days or even weeks. We don’t obtain the stolen knowledge and look at the content material of the listings as that is an moral concern of ours the place we don’t wish to obtain and retailer stolen sufferer knowledge. Therefore, we base our observations on matching the sufferer names.
One among our most pressing questions when doable re-victimization is why we see some victims re-appearing.
We’ve some simplified hypotheses about it:
- One other cyber-attack: An precise re-victimization and thus a second spherical of Cyber Extortion / cyber-attack towards the identical sufferer has occurred. Both by probably utilizing the identical level of entry or backdoor; or utterly unrelated to the primary incidence.
- Re-use of entry or knowledge: The sufferer knowledge has ‘travelled’ (leaked or offered to the underground) and is getting used as leverage to attempt to extort the sufferer as soon as extra. Or the entry has been offered to totally different patrons. However, knowledge or entry is being re-used.
- Affiliate crossover: An affiliate has reused sufferer knowledge between totally different Cy-X operations.
The final speculation would possibly present how financially pushed menace actors are and the way determined they could have change into. We’re positive that there could be different variations of our hypotheses, however we wished to maintain it so simple as doable for the next evaluation. We wished to discover whether or not we see patterns of re-victimizations between actors. We discovered over 100 occurrences the place victims had been re-posted, both to the identical or one other group’s leak web site.
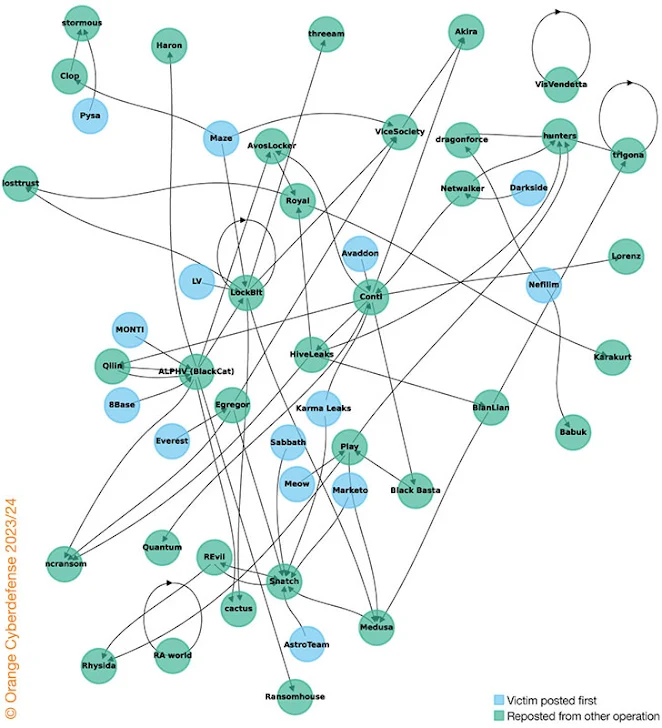
We created a community graph and added some color coding to the nodes. The inexperienced nodes signify actors who had been the second to publish a few specific sufferer. They spotlight the re-victimization. The blue nodes signify actors that act because the origin or first poster of a sufferer. When a Cy-X actor has been each, a first-time poster and second time poster, the node is by default inexperienced. The arrows are a further indicator. a directed community graph of sufferer appearances we are able to see the route of the re-victimization. Some Cy-X actors with round references repost victims on their very own knowledge leak web site. The evaluation under is an summary from our present analysis, we’re planning to publish a extra in depth evaluation in our upcoming Cy-Xplorer, our annual Ransomware report.
As might be seen above within the community graph, a number of clusters catch one’s eye. The Snatch group for instance demonstrates re-victimization exercise by constantly re-posting victims from different Cy-X operations corresponding to from AstroTeam, Meow, Sabbath, Karma Leaks, cactus, Quantum, Egregor and Marketo. Please keep in mind, re-victimization refers back to the phenomenon the place a sufferer of a criminal offense experiences further hurt or victimization sooner or later. In our consideration that signifies that victims expertise the re-occurrence of for instance unauthorized entry and/or knowledge exfiltration and/or knowledge theft and/or extortion and/or encryption and/or injury to popularity, and/or monetary loss and psychological hurt and many others.
Within the three hypotheses, the sufferer shall be victimized as soon as extra, experiencing one, a number of or all the harms simply listed. This isn’t in regards to the technical sophistication of the assault itself however by purely being listed as soon as once more on a darkweb leak web site, the sufferer group is uncovered once more to a number of extreme types of hurt.
If we proceed finding out the graph, we see one other cluster, ALPHV’s, the place we see that ALPHV re-posted victims from MONTI, 8Base and Qilin (within the latter the sufferer group was posted in the identical day at each leak websites, ALPHV and Qilin). And on the identical time, sufferer organizations that appeared first on ALPHV’s leak web site, had been re-posted by varied different operations corresponding to AvosLocker, LockBit, Ransomhouse, incransom, Haron, cactus, and many others. The arrows assist to point directionality of the connection, e.g. who acted first. Different clusters present very comparable patterns that we are going to not dive into on this exploration. However, the community graph and the above (partial) evaluation present us the relationships and patterns of re-posting sufferer organizations. Extra particularly, this propagation of the identical sufferer (not identical incident) by the Cyber Extortion panorama reaffirms one other idea that we’ve talked about in prior work, specifically the “opportunistic nature” of Cyber Extortion. Cyber Extortion is a quantity sport and a method to make sure monetary achieve is to ‘play on totally different fronts’ with a purpose to safe a minimum of some type of funds. Moreover, on a excessive degree, it reveals how messy this ecosystem has change into. All three of our hypotheses additional shine gentle onto the unpredictability of the cybercrime ecosystem.
Consequently, re-victimization will not be one thing that modifications how Cyber Extortion works however it does present us the potential for various types of re-victimizations, and thus sadly will increase the struggling of sufferer organizations which were experiencing a Cyber Extortion assault. And eventually, these sorts of analyses assist us to grasp the dynamics of a cybercrime ecosystem, on this case the Cyber Extortion / Ransomware menace panorama and its menace actors.
As with a first-time cyber-attack, for sufferer organizations it is very important tackle your sufferer variables that decide the result of your victimhood. In brief, your cyber practices, your digital footprint, the worth your group’s knowledge has to you, the time a menace actor has entry to your surroundings, the safety controls you may need in place to extend the “noisiness” of information exfiltration; are all variables that influence the attractiveness of your group to the opportunistic menace actors on the market in cyber house.
This can be a pattern of our evaluation. A extra in depth overview of the menace potential of Cyber Extortion, its foremost actors and the impact of legislation enforcement (in addition to a ton of different attention-grabbing analysis matters like an evaluation of the info obtained from our in depth vulnerability administration operations and Hacktivism) might be discovered within the Safety Navigator. Simply fill within the type and get your obtain. It is price it!