As tensions within the Center East proceed to escalate, cyberattacks and operations have grow to be a typical a part of the material of the geopolitical battle.
Final week, the pinnacle of Israel’s Nationwide Cyber Directorate blamed Iran and Hezbollah for “around the clock” cyberattacks in opposition to the nation’s networks, authorities businesses, and companies, tripling in depth as Israel’s army operations continued in opposition to Hamas in Gaza. Following Quds Day — Iran’s commemoration of its pro-Palestinian Jerusalem Day on April 5 — dozens of denial-of-service assaults disrupted Israeli targets, in accordance with knowledge from cybersecurity agency Radware.
Whereas the quantity of cyberattacks are working at a decrease degree up to now this yr, renewed tensions between Israel, Iran, and Lebanon may simply result in extra cyber exercise, says Pascal Geenens, director of risk analysis for Tel Aviv-based Radware, a maker of cloud safety options.
“There are two planes that we need to consider here,” Geenens says. “One is more nation-state aligned, meaning purposely doing attacks against another nation, while the other is all the hacktivist activity — they just want to share their message [and] show that they’re not happy with the situation.”
Total, Israel must be prepared for extra damaging cyberattacks, as Iran and different regional cyber teams have proven little restraint in such assaults, Google conclude in its “Instrument of First Resort: Israel-Hamas Warfare in Cyber” report, revealed in February. As Iran and Hezbollah seem prepared to make use of damaging cyberattacks in opposition to each Israel and the USA, Israeli-linked teams doubtless will proceed to focus on Iran, and hacktivists will doubtless goal any group they deem related to their perceived enemies, the report acknowledged.
“We assess with high confidence that Iran-linked groups are likely to continue to conduct destructive cyber attacks, particularly in the event of any perceived escalation to the conflict, which may include kinetic activity against Iranian proxy groups in various countries, such as Lebanon and Yemen,” the corporate acknowledged within the report.
Not Your Father’s Cyber Battle
When Russia invaded Ukraine, the Russian army used cyberattacks to focus on Ukraine previous to the invasion and throughout the invasion, and broadly attacked the US and Ukraine’s allies in Europe within the two years because the begin of the struggle.
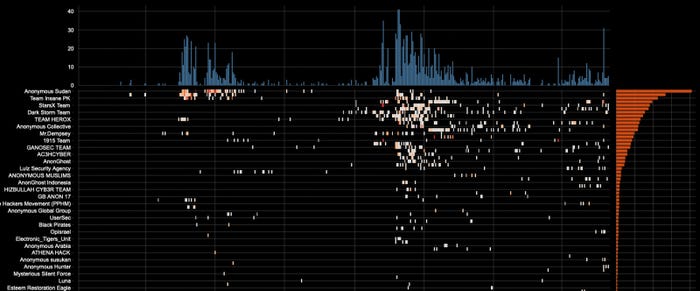
A big spike in cyberattacks got here previous to and after Oct. 7, whereas way more modest ranges of exercise focused Israel this yr. Supply: Radware
For the Center East, the cyber battle has a special character. On one hand, the contributors within the battle have totally different strengths and limitations, that are affecting their choices and making the cyber battle extra asymmetrical. The place the Russian authorities has a unity of objective, Iran and Hamas are extra opportunistic adversaries. The place Russia and Ukraine have comparable cyber capabilities, Israel’s army operations have restricted Hamas’ potential to reply, and the nation has probably the most subtle cyber-offensive capabilities within the area, says Ben Learn, head of cyber espionage evaluation for Google Cloud’s Mandiant incident-response group.
“Iran is very opposed to Israel, but aren’t a direct party to the conflict, so their goals aren’t necessarily about supporting the seizure of territory in the same sort of way as Russia,” he says. “Because conventional weapons are not [currently] an outcome acceptable to Iran, they are using cyber to do some destructive [operations]. … Cyber can be an easier tool to reach for there.”
Iran is just not the one anti-Israeli actor within the area. Google has noticed cyber operations by teams linked to Hezbollah, a Lebanese Islamist political celebration and militant group aligned with Iran.
Iran has additionally been the goal of disruptive cyber operations within the context of the battle, says Kirsten Dennesen, reporting analyst with Google’s Menace Evaluation Group (TAG). A number of disruptive assaults on the nation’s infrastructure have been attributed to Predatory Sparrow, which reappeared in October and attacked Iranian gasoline stations in December, and which some analysts have linked to Israel.
“Telegraphing intent and demonstrating involvement in the conflict without escalating or directly taking part in on-the-ground confrontation … limits potential blowback while also giving regional players the opportunity to project power through the cyber domain,” she says. “Moreover, cyber capabilities can be quickly deployed at minimal cost by actors who may wish to avoid armed conflict.”
Resurgence in Hacktivism
Nation-states aren’t the one actors concerned within the battle. Up to now yr, hacktivism has taken off as technologically savvy protesters react to the Russia-Ukraine struggle and the battle between Israel and Hamas. A lot of the rise in assault exercise in Israel is because of hacktivism, as is demonstrated by sharp upticks in denial-of-service assaults, says Radware’s Geenens.
“It’s not like it did not exist before, but before they were much less organized, and now they have like this ability to gather on Telegram,” he says. “They all started to communicate with each other through hashtags. They find each other much more easy, so they come together and create alliances to perform attacks.”
Up to now, the teams banded collectively underneath the Nameless title, claiming the monicker for their very own and trying to get different teams to enroll. Right now, they use operation-specific hashtags on Telegram to realize like-minded collaborators, a way more environment friendly technique of operation, Geenens says.
Hacktivism doubtless will proceed to gas assaults in opposition to not solely Israel, however different international locations as properly, he says. Assaults usually tend to ramp up rapidly as nation-states develop normal methods and hacktivists are capable of collaborate extra effectively.
“Anything that happens in the future,” Geenens says, “whether it be a military operation or an outcome of an election that they don’t like or somebody says something that that they don’t like — they will be there and there will be a wave of DDoS attacks.”