Checkmarx SCS (Provide Chain Safety) workforce discovered a vulnerability in GitHub that may enable an attacker to take management over a GitHub repository, and probably infect all functions and different code counting on it with malicious code.
If not explicitly tended, all renamed usernames on GitHub have been susceptible to this flaw, together with over 10,000 packages on the Go, Swift, and Packagist bundle managers. Because of this 1000’s of packages may have been hijacked instantly and begin serving malicious code to thousands and thousands of customers.
The vulnerability was mounted by GitHub following our report and is now not exploitable.
This isn’t the primary vulnerability discovered on this mechanism; earlier this yr, an attacker used the same vulnerability to hijack and poison standard PHP packages with thousands and thousands of downloads.
The mechanism that was discovered susceptible, the “Popular repository namespace retirement”, stays a gorgeous assault level for provide chain attackers sooner or later. Subsequently, we offer an open-source device to determine and assist mitigate this danger.
GitHub Repository URL is Coupled to its Username
GitHub Repositories have a novel URL, it’s nested beneath the person account which created the repository. Each time somebody wish to obtain (clone) the open supply repository, they use the complete repository URL.
When GitHub Customers Rename Their Username
We confirmed that GitHub repositories are coupled to usernames. What occurs when customers determine to rename their account? In that case, GitHub helps the rename and shows the next warning noting that each one site visitors for the outdated repository’s URL might be redirected to the brand new one.
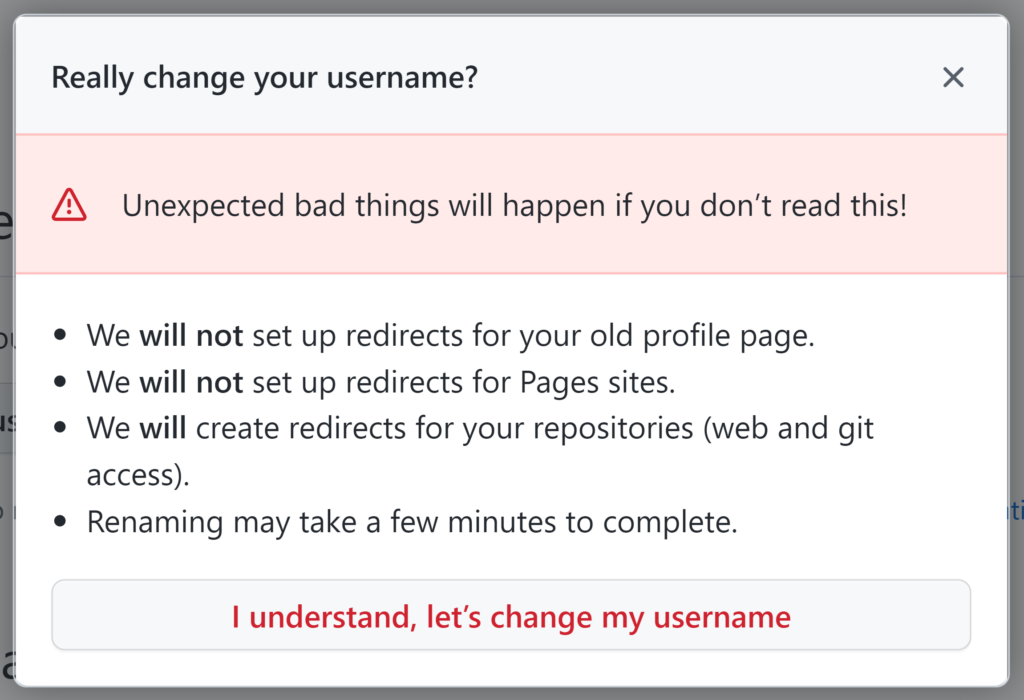
After accepting the warning and renaming the username, GitHub mechanically units up redirect guidelines from the outdated repository’s URLs to the brand new URLs. That is accomplished to maintain issues working for customers unaware of this username change.

What’s RepoJacking?
RepoJacking is a method to hijack renamed repository URLs site visitors and routing it to the attacker’s repository by exploiting a logical flaw that breaks the unique redirect.
A GitHub repository is susceptible to RepoJacking when its creator determined to rename his username whereas the outdated username is obtainable for registration. Now we have proven the coupling within the repository URLs between the repository title and the creator username, and this implies attackers can create a brand new GitHub account having the identical mixture to match the outdated repository URL utilized by present customers.
Each time attackers do that, the default redirect is disabled, and all present site visitors is instantly routed to the attackers malicious GitHub repository.

GitHub Safety Towards RepoJacking
To keep away from this probably dangerous conduct, GitHub put in place the “popular repository namespace retirement” safety measure: any repository with greater than 100 clones on the time its person account is renamed is taken into account “retired” and can’t be utilized by others.
To make clear: what is taken into account “retired’ is the namespace, that means the mixture of the username and the repository title.
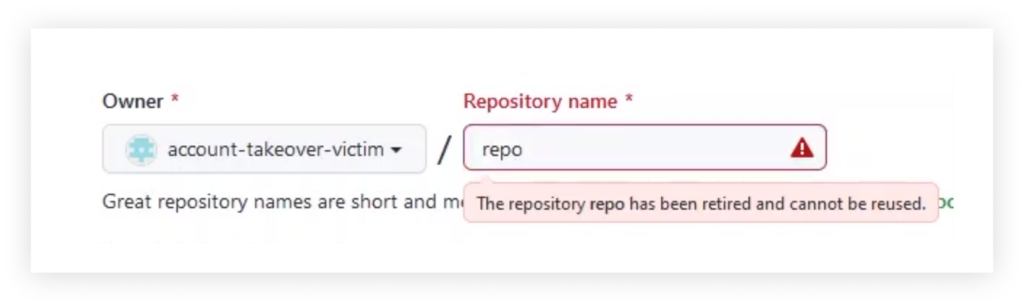
For instance, let’s take the repository named “repo” of the username “account-takeover-victim.”
This repository was just lately cloned 100 instances, which qualifies it for the favored repository namespace retirement.
At this level, the account’s proprietor decides to rename the username to whichever title they select.
The sensible results of that is that the username “account-takeover-victim” can now be claimed by anybody.
Nevertheless, as soon as the brand new proprietor of this username tries to open a brand new repository beneath the title “repo,” they are going to be blocked and get the next message:
Bypassing GitHub Safety
In a earlier weblog, we described one method for bypassing this safety. This was most definitely the way in which it was accomplished within the CTX incident. Shortly after that incident and the publicity it gained, GitHub patched this vulnerability.
Our group’s Chief Architect, Elad Rapoport, felt that there was extra to this story, took one other go, and located a brand new technique to bypass the identical safety. The brand new exploit was reported to the GitHub bug bounty program, which just lately confirmed and patched the brand new vulnerability.
The present bypass abuses the “Repository Transfer” characteristic to realize its purpose within the following method:
- “victim/repo” is a well-liked GitHub repository retired beneath the “popular repository namespace retirement” safety.
- “helper_account” creates the “repo” repository
- “helper_account” switch possession of the “repo” repository to “attacker_account.”
- “attacker_account” rename its username to “victim.”
- The brand new “victim” account (beforehand “attacker_account”) accepts the possession switch
The namespace “victim/repo” is now within the attacker’s management
Impression
As proven with the earlier bypass of this safety measure, profitable exploitation allows the takeover of standard code packages in a number of bundle managers, together with “Packagist,” “Go,” “Swift,” and extra. Now we have recognized over 10,000 packages in these bundle managers utilizing renamed usernames and are vulnerable to being susceptible to this method in case a brand new bypass is discovered.
As well as, exploiting this bypass can even end in a takeover of standard GitHub actions, that are additionally consumed by specifying a GitHub namespace. Poisoning a well-liked GitHub motion may result in main Provide Chain assaults with important repercussions.
As talked about, by now this vulnerability is mounted and now not exploitable, which isn’t to say that one other technique to bypass this similar safety gained’t be discovered.
Timeline
1 Nov 21 – We discovered a technique to bypass the GitHub namespace retirement characteristic
8 Nov 21 – We disclose the bypass findings to GitHub
8 Nov 21 – GitHub acknowledged the bypass and replied that they’re engaged on a repair
24 Mar 22 – GitHub reply that they’ve mounted the bypass
11 Could 22 – We uncover that the bypass continues to be exploitable and reported to GitHub
23 Could 22 – This assault was discovered lively towards open-source assault
25 Could 22 – This system was revealed by a safety researcher taking possession of the assaults and was mounted shortly after by GitHub
13 June 22 – we discovered extra vulnerability to bypass GitHub namespace retirement characteristic and reported to GitHub
19 Sep 22 – GitHub mounted the vulnerability, classifies it as “High” severity, and grants us a bug bounty
26 Oct 22 – Full disclosure
Conclusion
Many GitHub customers select to make use of the “User rename” characteristic GitHub provides, amongst them, customers that management standard repositories and packages. For that cause, the try and bypass the “Popular repository namespace retirement” stays a gorgeous assault level for provide chain attackers with the potential to trigger substantial damages.
Furthermore, it’s attention-grabbing to note that GitHub’s offered safety is activated primarily based on inside metrics and provides the customers no indication if a selected namespace is protected by it or not. This may go away some repositories and packages unknowingly in danger.
We suggest that clients keep away from utilizing retired namespaces to reduce the assault floor as different vulnerabilities on this mechanism should still exist.
Now we have launched an open-source device to determine these packages and recommend a safer technique to devour them (utilizing the brand new Package deal URL).
We wish to thank GitHub for working with us and making use of a repair to this vulnerability.
Working collectively to maintain the open supply ecosystem secure.
