It looks like builders engaged on REST APIs have lastly come to phrases with the hazards of verbose error messages, however GraphQL builders are nonetheless studying what occurs when their API schema is left unprotected.
In March 2022, CVE-2021-4191 disclosed how GitLab’s API allowed “a remote, unauthenticated attacker to recover usernames, names, and sometimes email addresses”. This was potential for the reason that Consumer object sort was uncovered with none type of authentication.
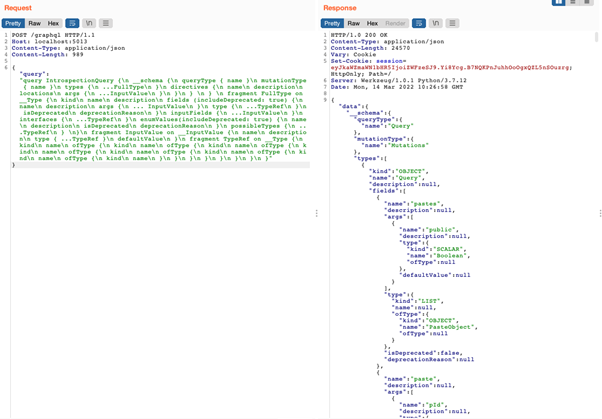
After all, auth-related vulnerabilities are generally reported on different APIs, however detecting them in GraphQL will be aided by a singular characteristic of the language: Introspection.
Introspection is a useful improvement characteristic that, when enabled in manufacturing, discloses the categories and operations which are supported by the API, together with (generally) queries and mutations which are solely out there to excessive privilege customers.
Profitable introspection question on the Rattling Susceptible GraphQL Software (DVGA) API
Hottest GraphQL servers now disable this characteristic in manufacturing by default, which is a step in the proper course, however clearly not sufficient.
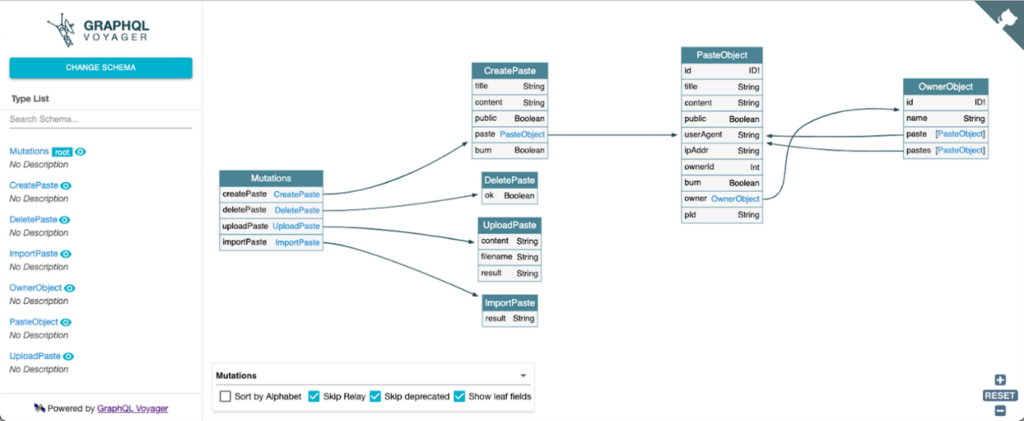
Visualization of the DVGA API mutations by importing its schema in GraphQL Voyager
Corporations usually depend on this characteristic to assist others navigate their public APIs, as described in a HackerOne report submitted to New Relic:
“We do not consider introspection revealing schema definitions to be sensitive information exposure. Our scheme definitions themselves are not sensitive information and we have designed our endpoints to be discoverable via introspection. Introspection is not something limited to internal use, quite the opposite; it’s super useful for external implementers to know how our API/domain works.”
Even when Introspection is disabled, an attacker can acquire knowledge by abusing the “Schema Suggestions” characteristic.
If you happen to’re not acquainted with this characteristic, it’s mainly a means for some GraphQL servers to assist builders construct queries by hinting on the right identify of operations, varieties, and fields.
Beneath, we will see an instance: once we attempt to fetch the “descriptions” subject (which doesn’t exist) utilizing the Introspection question, the server tries to assist us repair this error by responding with “Did you mean ‘description’?”
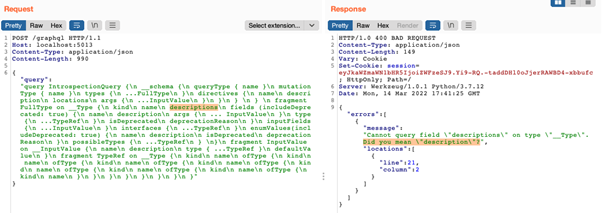
Question subject identify suggestion on the DVGA API
Nikita Stupin’s analysis and its ensuing device clairvoyance make this characteristic a complete lot simpler to use … all you want is a wordlist, and the device will brute-force its method to the unique API schema, primarily based on the server’s useful hints.
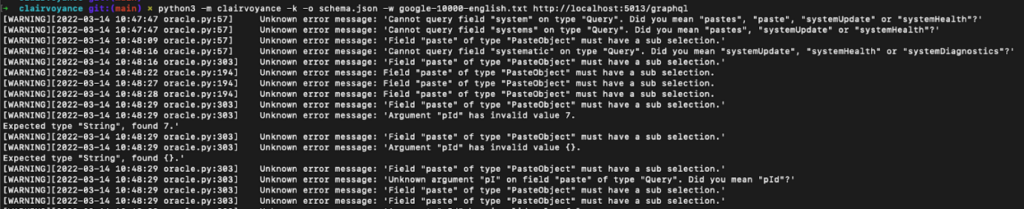
Apollo GraphQL is likely one of the servers that supply strategies “out of the box” and, sadly, there may be presently no method to disable them, however there are some workarounds.
What else?
Nicely, attackers seeking to bypass enterprise logic limitations would additionally love the truth that the GraphQL schema specifies which fields are deprecated, and there are even some verbose “deprecation reasons” that disclose inside choices and future iterations of the API.

Deprecated fields within the DVGA schema
Usually realizing a couple of delicate operation is half the battle … if you mix this with different vulnerabilities, exploiting GraphQL APIs is as straightforward as pie.
IDOR (Insecure Direct Object Reference), CSRF (Cross-Web site Request Forgery), SQL Injection, and all forms of Damaged Entry Management vulnerabilities paired with GraphQL are simpler to detect and exploit, although they happen with the identical frequency in REST APIs.
And we shouldn’t overlook concerning the vulnerabilities which are extra prone to happen because of the inherent flexibility of this querying language, resembling Denial of Service (DoS).
GraphQL purchasers can specify precisely what (and the way a lot) knowledge they wish to obtain from the server, so it’s straightforward to think about how this flexibility is perhaps a strong device when making an attempt to overload a system with requests:
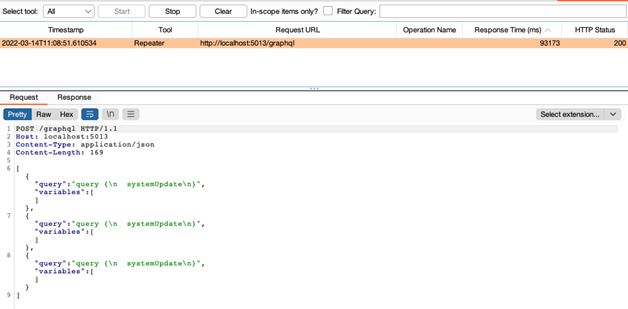
Abusing batch requests utilizing the DVGA
Present finest practices recommend a mix of the next approaches:
GraphQL builders in impact have to work in opposition to the options of the language to make sure that their APIs are as strong, opaque, and dependable as some other.
Fortunately, there may be an ecosystem of open-source safety instruments that may assist, amongst them:
- batchQL, a script that makes an attempt frequent assaults in opposition to GraphQL APIs “with a focus on performing batch GraphQL queries and mutations”;
- the InQL Burp extension, which routinely tries to seek out GraphQL endpoints and improvement consoles;
- graphql-path-enum, which helps discover round references within the schema, which will result in DoS
… and plenty of extra.