A 7-Zip vulnerability permitting attackers to bypass the Mark of the Internet (MotW) Home windows safety function was exploited by Russian hackers as a zero-day since September 2024.
In keeping with Development Micro researchers, the flaw was utilized in SmokeLoader malware campaigns concentrating on the Ukrainian authorities and personal organizations within the nation.
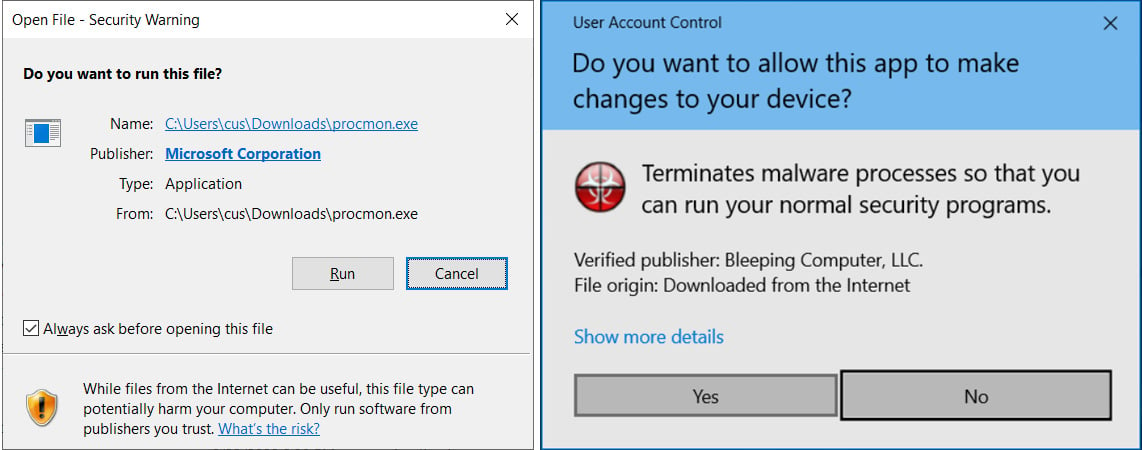
The Mark of the Internet is a Home windows safety function designed to warn customers that the file they’re about to execute comes from untrusted sources, requesting a affirmation step through an extra immediate. Bypassing MoTW permits malicious information to run on the sufferer’s machine with out a warning.
When downloading paperwork and executables from the online or acquired as an electronic mail attachment, Home windows provides a particular ‘Zone.Id’ alternate information stream referred to as the Mark-of-the-Internet (MoTW) to the file.
When trying to open a downloaded file, Home windows will test if a MoTW exists and, if that’s the case, show extra warnings to the consumer, asking if they’re positive they want to run the file. Equally, when opening a doc in Phrase or Excel with a MoTW flag, Microsoft Workplace will generate extra warnings and switch off macros.
Supply: BleepingComputer
Because the Mark of the Internet security measures forestall harmful information from routinely operating, menace actors generally try and discover MoTW bypasses so their information routinely run and execute.
For years, cybersecurity researchers requested 7-Zip add help for the Mark of the Internet, however it was solely in 2022 that help for the function was lastly added.
MoTW bypasses exploited in assaults
Development Micro’s Zero Day Initiative (ZDI) workforce first found the flaw, now tracked as CVE-2025-0411, on September 25, 2024, observing it in assaults carried out by Russian menace actors.
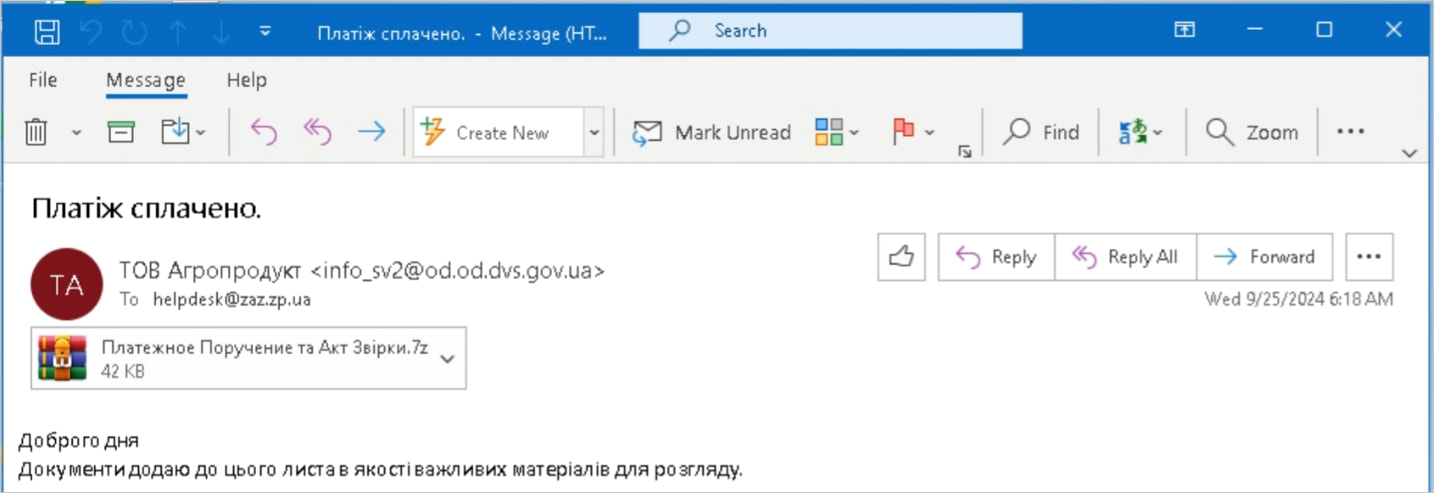
Hackers leveraged CVE-2025-0411 utilizing double archived information (an archive inside an archive) to take advantage of a scarcity of inheritance of the MoTW flag, leading to malicious file execution with out triggering warnings.
The specifically crafted archive information have been despatched to targets through phishing emails from compromised Ukrainian authorities accounts to bypass safety filters and seem professional.
Supply: Development Micro
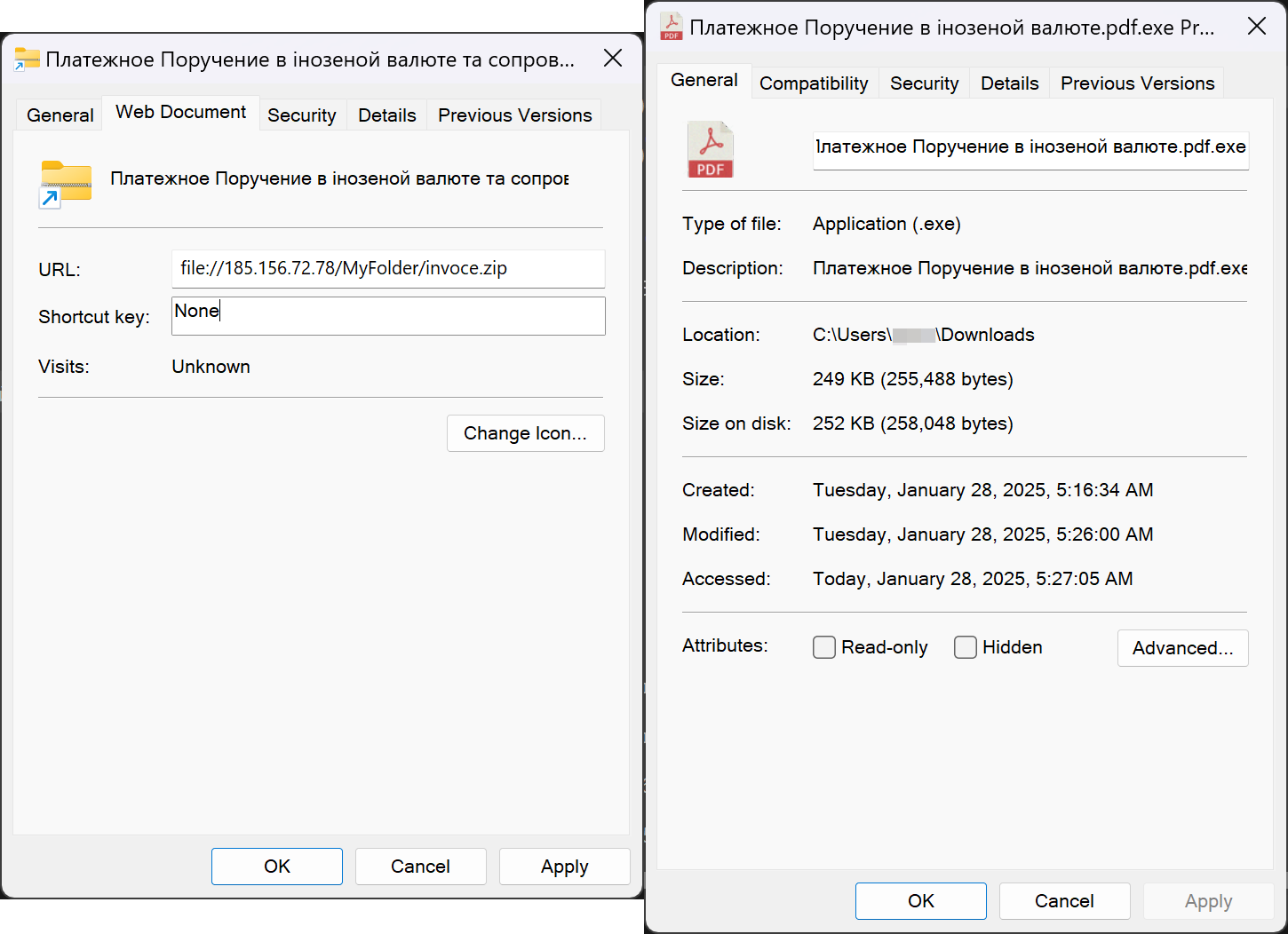
Using homoglyph methods, the attackers hid their payloads inside the 7-Zip information, making them seem innocent Phrase or PDF paperwork.
Though opening the father or mother archive does propagate the MoTW flag, the CVE-2025-0411 flaw precipitated the flag to not propagate to the contents of the internal archive, permitting malicious scripts and executables to launch immediately.
Supply: Development Micro
This final step triggers the SmokeLoader payload, a malware dropper used up to now to put in info-stealers, trojans, ransomware, or creating backdoors for persistent entry.
Development Micro says these assaults impacted the next organizations:
- State Government Service of Ukraine (SES) – Ministry of Justice
- Zaporizhzhia Vehicle Constructing Plant (PrJSC ZAZ) – Vehicle, bus, and truck producer
- Kyivpastrans – Kyiv Public Transportation Service
- SEA Firm – Home equipment, electrical tools, and electronics producer
- Verkhovyna District State Administration – Ivano-Frankivsk oblast administration
- VUSA – Insurance coverage firm
- Dnipro Metropolis Regional Pharmacy – Regional pharmacy
- Kyivvodokanal – Kyiv Water Provide Firm
- Zalishchyky Metropolis Council – Metropolis council
Replace 7-Zip
Though the invention of the zero-day got here in September, it took Development Micro till October 1, 2024, to share a working proof-of-concept (PoC) exploit with the builders of 7-Zip.
The latter addressed the dangers through a patch applied in model 24.09, launched on November 30, 2024. Nevertheless, as 7-Zip doesn’t embody an auto-update function, it is not uncommon for 7-Zip customers to run outdated variations.
Subsequently, it’s strongly advisable that customers obtain the most recent model to verify they’re shielded from this vulnerability.
