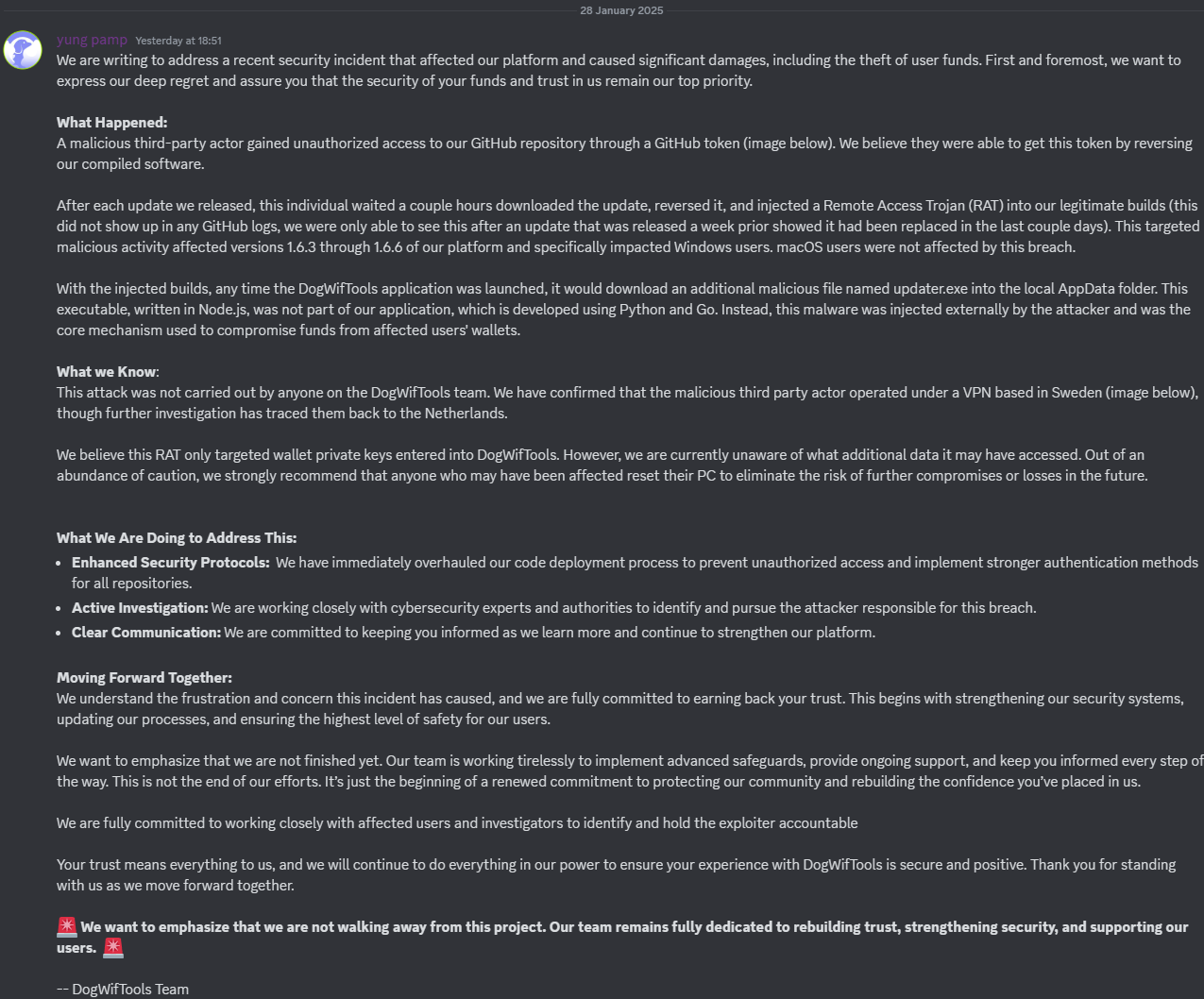
Hackers have compromised the Home windows model of the DogWifTools software program for selling meme cash on the Solana blockchain in a supply-chain assault that drained customers’ wallets.
The builders declare that a malicious risk actor compromised the undertaking’s personal GitHub repository after reverse engineering the software program to extract a GitHub token.
The maintainers of the platform mentioned on the official Discord channel that the risk actor gained entry to the GitGub repository and trojanized DogWifTools variations 1.6.3 via 1.6.6.
DogWifTools is a platform that assists builders in launching and selling meme cash on the Solana blockchain. It provides quantity automation, bundling, remark bots to spice up engagement, and excessive exercise simulation to assist tokens development on Pump.enjoyable.
Stealthy malware injection
Because the platform clarify Discord, a malicious risk actor compromised the undertaking’s personal GitHub repository after reverse engineering the software program to extract a GitHub token.
After gaining entry, the risk actor didn’t begin publishing malicious updates instantly, because it occurred in comparable instances lately. As an alternative, the risk actors waited for DogWifTools builders to launch a brand new model, which the risk actors then trojanized and uploaded a few hours later.
“After each update we released, this individual waited a couple hours downloaded the update, reversed it, and injected a Remote Access Trojan (RAT) into our legitimate builds (this did not show up in any GitHub logs, we were only able to see this after an update that was released a week prior showed it had been replaced in the last couple days,” defined DogWifTools.
“This targeted malicious activity affected versions 1.6.3 through 1.6.6 of our platform and specifically impacted Windows users. macOS users were not affected by this breach.”
Supply: BleepingComputer
When launched, the malicious DogWifTools utility downloaded a file (updater.exe) into the native AppData folder that focused customers’ cryptocurrency pockets personal keys.
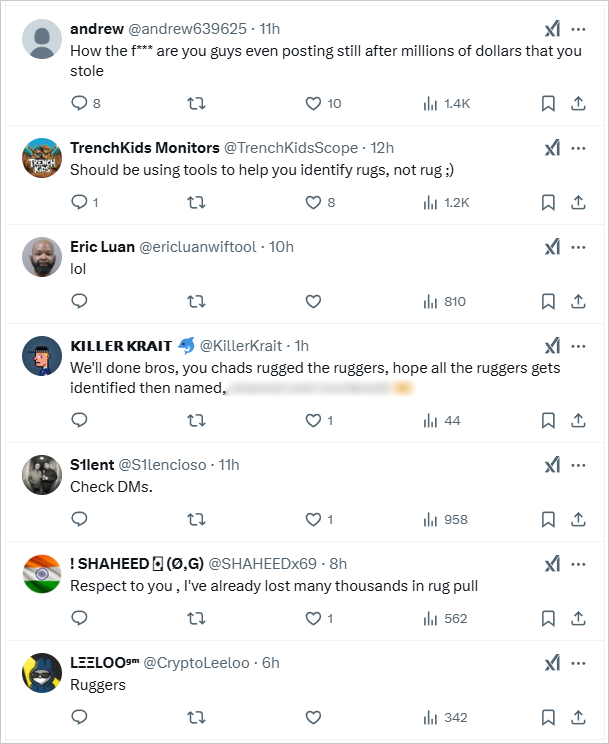
Accusations and blended emotions
On X (Twitter), many customers accuse the platform of “rug pulling,” although there’s no proof of this or indicators of fraudulent exercise from DogWifTools themselves.
The explanation behind these accusations is that DogWifTools is inbuilt a method that enables many memecoin scammers to abuse it for fraudulent token launches.
Blockchain investigator ZachXBT defined to BleepingComputer that “the platform ‘optimizes’ token launches through the bundler, which discreetly holds a large quantity of the launched coin.” The bundler additionally has a quantity bot that automates the purchase/promote transactions to inflate exercise.
Over the previous two days, DogWifTools customers reported that the trojanized utility drained all their wallets, cold and warm, and so they misplaced entry to their cryptocurrency trade accounts (Binance, Coinbase).
In keeping with crypto neighborhood member solboy, entry to delicate information can be potential as a result of DogWifTools asks “for very intrusive permissions on your computer.” This allegedly gave the hacker entry to ID images that could possibly be used to hijack accounts at cryptocurrency exchanges.
In keeping with neighborhood estimates, the risk actor drained greater than $10 million from DogWifTools customers however somebody claiming the assault says that the determine is “completely off,” with out providing any additional clarification.
The alleged hacker additionally mentioned that they didn’t steal any person information, aside from DogWifTools walled information saved regionally, and didn’t interact in id theft.
Within the incident disclosure on Discord, the DogWifTools group flatly denies its workers being straight concerned within the breach and emphasizes that they may do the whole lot potential to rebuild belief with their neighborhood.
The platform is engaged on implementing further safety measures whereas it’s also collaborating with investigators to establish the attacker and maintain them accountable.
