As GenAI instruments and SaaS platforms develop into a staple part within the worker toolkit, the dangers related to knowledge publicity, identification vulnerabilities, and unmonitored looking habits have skyrocketed.
Ahead-thinking safety groups are searching for safety controls and methods to handle these dangers, however they don’t all the time know which dangers to prioritize. In some circumstances, they may have blind spots into the existence of dangers.
To assist, a brand new complimentary danger evaluation is now accessible. The evaluation can be custom-made for every group’s looking atmosphere, evaluating their danger and offering actionable insights.
Safety and IT groups can leverage the evaluation to strengthen their safety posture, inform their decision-making, evangelize throughout the group, and plan subsequent steps.
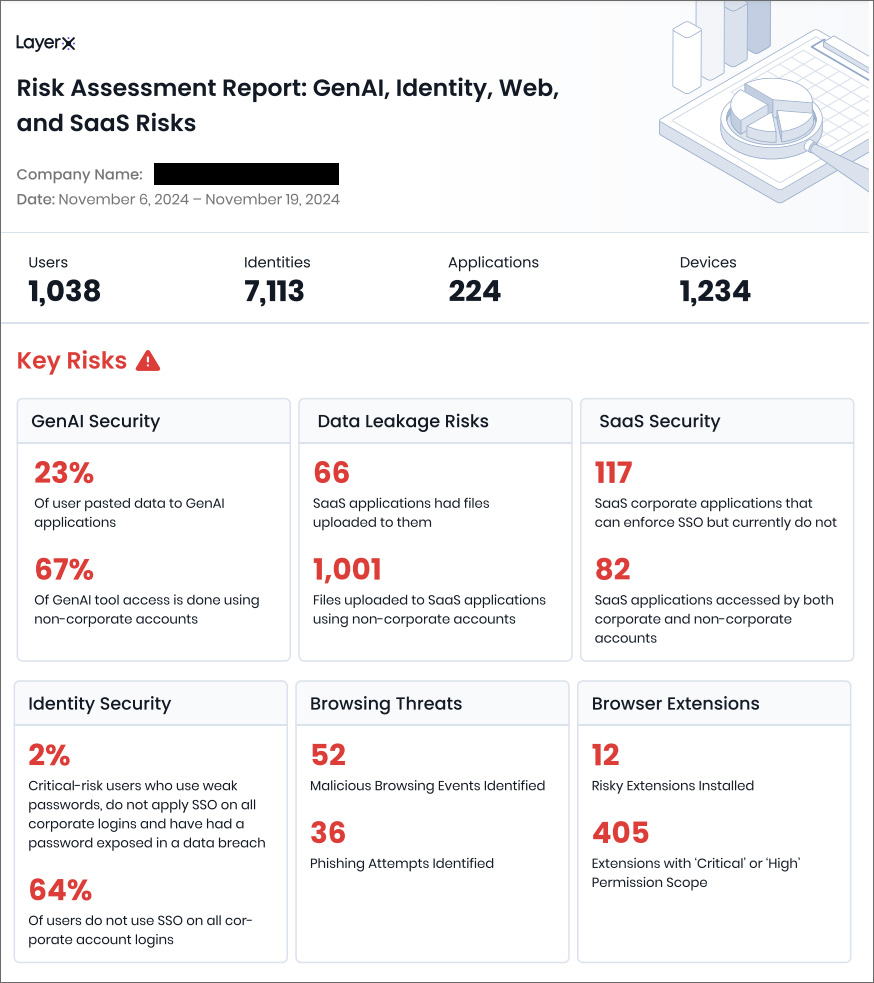
The evaluation leads to a report that features a high-level overview of key dangers, together with insecure use of gen AI, delicate knowledge leakage dangers via the browser, SaaS app utilization, identification safety gaps, looking threats, and the usage of malicious extensions and their permissions.
The evaluation report then drills down into every discovering, offering correct metrics and mitigation suggestions. You’ll find an evaluation report instance right here.
Why Assess? Browser Threats and Dangers
The browser is the nerve middle of the trendy workforce. It drives productiveness, but additionally introduces dangers. A few of the high dangers organizations face embody:
- GenAI Safety Threats: Workers could unintentionally share delicate info, reminiscent of supply code, buyer PII, enterprise plans, or monetary knowledge, with ChatGPT and different generative AI instruments.
- Knowledge Leakage Dangers: Browsers can function assault vectors, enabling attackers to exfiltrate inside information, emails, CRM knowledge, and extra. Workers may additionally add or paste delicate info into exterior web sites or SaaS apps.
- SaaS Safety Dangers: Shadow SaaS purposes, together with doubtlessly malicious ones, may be exploited to exfiltrate knowledge or infiltrate company networks.
- Identification Vulnerabilities: Weak credential practices—reminiscent of password reuse, account sharing, compromised or weak passwords, and utilizing private passwords for work—can result in identification fraud and account takeovers.
- Looking Threats: Social engineering and phishing web sites can extract delicate credentials or inside paperwork. Attackers might additionally harvest cookies and saved browser knowledge for malicious functions.
- Dangerous Browser Extensions: Malicious browser extensions can monitor consumer exercise, steal credentials, hijack classes, harvest cookies, and facilitate assaults.
Is Your Group at Danger?
Step one in addressing these challenges is knowing what you’re prone to. To assist, LayerX Safety offers organizations with a complimentary danger evaluation designed to assist them uncover and analyze their danger profile throughout areas of recent net and SaaS safety that always go unaddressed.
It’s tailor-made to evaluate and report on their particular atmosphere. This evaluation offers detailed and actionable insights that may be applied instantly.
Use this complimentary danger evaluation to determine, assess, and deal with looking and SaaS dangers in your office. This evaluation is useful for organizations of any stage of maturity, throughout any business and for any variety of customers.
Click on right here to get a complimentary danger evaluation.
Sponsored and written by LayerX.
