A crew of safety researchers has disclosed new side-channel vulnerabilities in trendy Apple processors that might steal delicate data from internet browsers.
The Georgia Institute of Expertise and Ruhr College Bochum researchers, who introduced one other assault dubbed ‘iLeakage‘ in October 2023, introduced their new findings in two separate papers, particularly FLOP and SLAP, which present distinct flaws and methods to take advantage of them.
The failings stem from defective speculative execution implementation, the underlying explanation for infamous assaults like Spectre and Meltdown.
The FLOP and SLAP side-channel assaults goal options aimed toward dashing up processing by guessing future directions as an alternative of ready for them can go away traces in reminiscence to extract delicate data.
“Starting with the M2/A15 generation, Apple CPUs attempt to predict the next memory address that will be accessed by the core,” defined the researchers to BleepingComputer.
“Moreover, starting with the M3/A17 generation, they attempt to predict the data value that will be returned from memory. However, mispredictions in these mechanisms can result in arbitrary computations being performed on out-of-bounds data or wrong data values.”
These mispredictions can have real-world safety implications, corresponding to escaping the online browser sandbox and studying cross-origin personally identifiable data on Safari and Chrome, as demonstrated within the two papers.
The assaults are executed remotely by way of an internet browser utilizing a malicious webpage containing JavaScript or WebAssembly code designed to set off them.
The researchers disclosed the failings to Apple on March 24, 2024 (SLAP) and September 3, 2024 (FLOP).
Apple acknowledged the shared proof-of-concept and acknowledged it plans to deal with the problems. Nonetheless, on the time of writing, the failings stay unmitigated.
“We want to thank the researchers for their collaboration as this proof of concept advances our understanding of these types of threats,” Apple informed BleepingComputer.
“Based on our analysis, we do not believe this issue poses an immediate risk to our users.”
FLOP
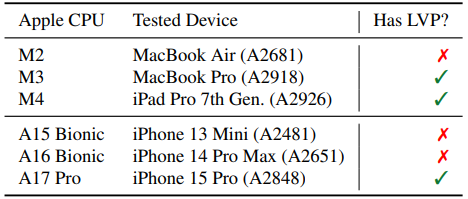
The first paper describes False Load Output Prediction (FLOP), an issue with Apple’s newest M3, M4, and A17 processors, which predict not simply the reminiscence addresses they are going to entry however even the precise values saved in reminiscence.
If these Load Worth Prediction (LVP) guesses are unsuitable, incorrect information is used for non permanent computations, which attackers can exploit to leak delicate data.
Supply: flop.fail
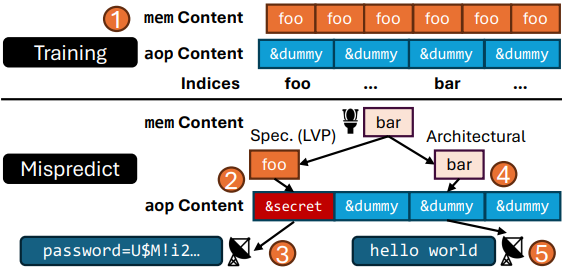
The researchers demonstrated the FLOP assault by tricking Apple’s M3 CPU into making unsuitable guesses after coaching it by way of an execution loop that hundreds a selected fixed worth after which triggers a misprediction.
Whereas the CPU stays on this incorrect state, it leaks information by way of a cache timing assault. This leak lasts lengthy sufficient for the researchers to measure reminiscence entry instances and deduce the key worth earlier than the CPU corrects itself.
Supply: flop.fail
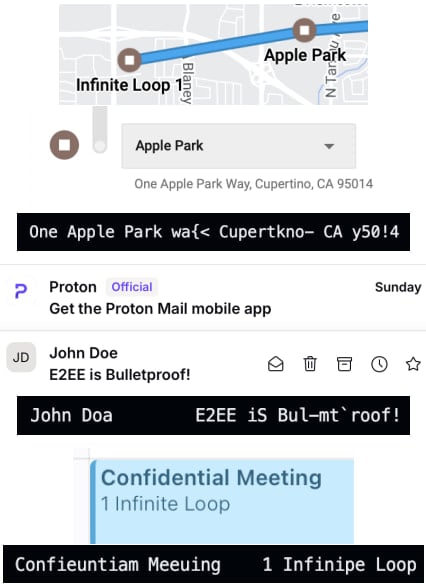
Via FLOP, the researchers demonstrated escaping Safari’s sandbox, retrieving sender and topic data from Proton Mail inbox, stealing Google Maps location historical past, and recovering personal occasions from iCloud Calendar.
Supply: flop.fail
SLAP
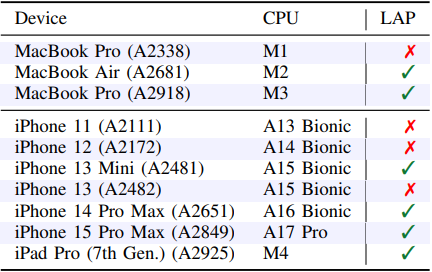
The second paper describes Speculative Load Tackle Prediction (SLAP), which impacts Apple’s M2 and A15 processors, and lots of the later fashions.
As an alternative of FLOP, which is guessing what worth a reminiscence load will return, SLAP considerations the prediction of the reminiscence deal with that will probably be accessed subsequent, referred to as Load Tackle Prediction (LAP).
Supply: slap.fail
An attacker can “train” the CPU to anticipate a selected reminiscence entry sample, then manipulate it into accessing secret information by abruptly altering the reminiscence structure, inflicting the next prediction to level to the key.
The CPU, trusting its prediction, reads and processes the delicate information earlier than realizing and correcting the error, permitting an attacker to take advantage of cache timing or different aspect channels to deduce the leaked information.
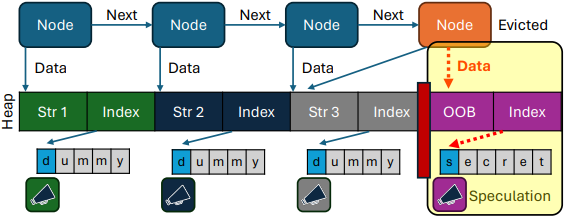
Supply: slap.fail
By executing the SLAP assault repeatedly, the attacker can reconstruct stolen data corresponding to retrieving Gmail inbox information, Amazon orders and shopping information, and Reddit consumer exercise.
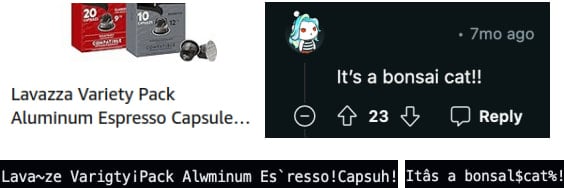
Supply: slap.fail
Actual-world implications
The FLOP and SLAP assaults are important because of their affect on trendy and broadly used {hardware} and since they are often executed remotely with out requiring bodily entry.
A sufferer would simply want to go to a malicious web site for the secrets and techniques to leak, bypassing browser sandboxing, ASLR, and conventional reminiscence protections.
The scripts used within the demo web sites execute a sequence of reminiscence hundreds designed to govern Apple’s FLOP and SLAP, so no malware an infection is required. Trendy browsers permit superior computation, successfully serving as assault instruments on this case.
Till safety updates from Apple are made obtainable, a doable mitigation could be to show off JavaScript in Safari and Chrome, although it will expectedly break many web sites.
